Which of the following tools is used to recover data and partitions, and can run on Windows, Linux, SunOS, and Macintosh OS X operating systems?
Which of the following utilities is used for decrypting WEP encryption on an 802.11b network?
Which of the following IP packet elements is responsible for authentication while using IPSec?
Which of the following ICMP types refers to the message "Time Exceeded"?
Which of the following ports can be used for IP spoofing?
Which of the following password cracking attacks is based on a pre-calculated hash table to retrieve plain text passwords?
You work as a Desktop Support Technician for umbrella Inc. The company uses a Windows-based network. An employee from the sales department is facing problem in the IP configuration of the network connection. He called you to resolve the issue. You suspect that the IP configuration is not configured properly. You want to use the ping command to ensure that IPv4 protocol is working on a computer. While running the ping command from the command prompt, you find that Windows Firewall is blocking the ping command. What is the cause of the issue?
Which of the following terms is used to represent IPv6 addresses?
Which of the following tools is used to analyze a system and report any unsigned drivers found?
Which of the following tools is used to collect volatile data over a network?
Which of the following is true for XSS, SQL injection, and RFI?
Steve works as a Network Administrator for Blue Tech Inc. All client computers in the company run the Windows Vista operating system. He often travels long distances on official duty. While traveling, he connects to the office server through his laptop by using remote desktop connection.
He wants to run an application that is available on the server of the company. When he connects to the server, he gets a message that the connection is blocked by the firewall. He returns to his office to resolve the issue. He opens the Windows Firewall Settings dialog box. What actions should he perform in the dialog box given below to accomplish the task?
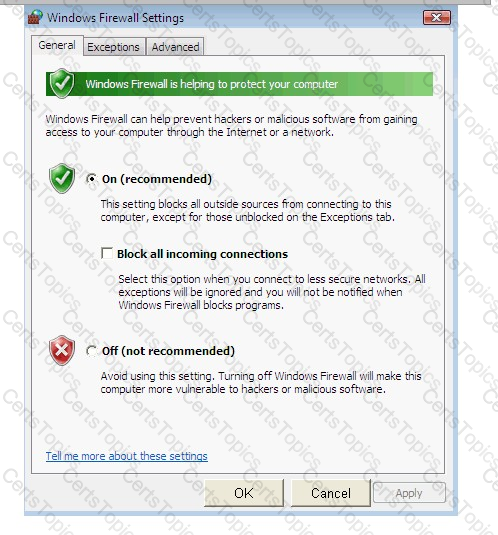
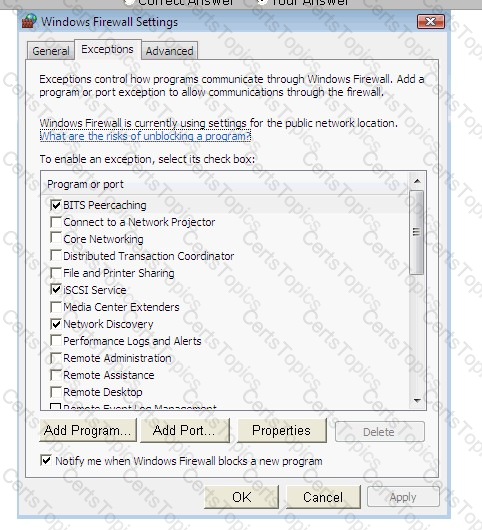
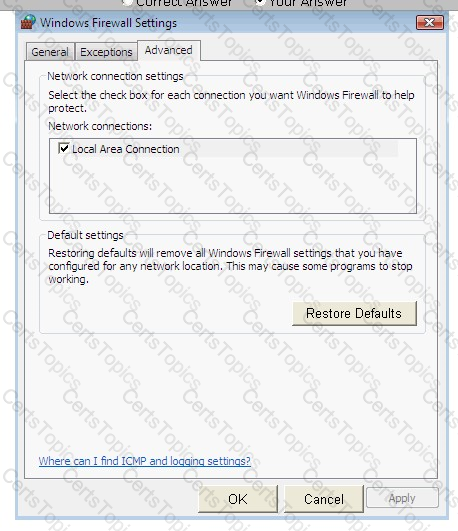
Mark works as a Network Administrator for Infonet Inc. The company has a Windows 2000 domainbased network. Mark wants to block all NNTP traffic between the network and the Internet. How will he configure the network?
Where is the Hypertext Transfer Protocol (HTTP) used?
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 domain-based network. The network has three Windows Server 2008 member servers and 150 Windows Vista client computers. The network contains a Windows Server 2008 Core computer. You want to install the DNS server role on the Windows Server 2008 Core computer. Which of the following commands will you use to accomplish the task?
In the DNS Zone transfer enumeration, an attacker attempts to retrieve a copy of the entire zone file for a domain from a DNS server. The information provided by the DNS zone can help an attacker gather user names, passwords, and other valuable information. To attempt a zone transfer, an attacker must be connected to a DNS server that is the authoritative server for that zone. Besides this, an attacker can launch a Denial of Service attack against the zone's DNS servers by flooding them with a lot of requests. Which of the following tools can an attacker use to perform a DNS zone transfer?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following tools is an open source network intrusion prevention and detection system that operates as a network sniffer?
You work as a Network Administrator for McRobert Inc. Your company has a TCP/IP-based network.
You want to know the statistics of each protocol installed on your computer. Which of the following commands will you use?
Which of the following tools allows an attacker to intentionally craft the packets to gain unauthorized access?
Each correct answer represents a complete solution. Choose two.
You work as a Network Administrator for Net Perfect Inc. The company has a Windows Server2008 network environment. The network is configured as a Windows Active Directory-based single forest single domain network. The network is configured on IP version 6 protocol. All the computers on the network are connected to a switch device. One day, users complain that they are unable to connect to a file server. You try to ping the client computers from the server, but the pinging fails. You try to ping the server's own loopback address, but it fails to ping. You restart the server, but the problem persists.
What is the most likely cause?
Which of the following is the default port used by Simple Mail Transfer Protocol (SMTP)?
Which of the following configuration schemes in IPv6 allows a client to automatically configure its own IP address with or without IPv6 routers?
Which of the following proxy servers is placed anonymously between the client and remote server and handles all of the traffic from the client?
Which of the following technologies is used to detect unauthorized attempts to access and manipulate computer systems locally or through the Internet or an intranet?
Which of the following utilities is used to display the current TCP/IP configuration of a Windows NT computer?
You work as a Network Administrator for McRobert Inc. Your company has a TCP/IP-based network. You want to get the protocol statistics and the active TCP/IP network connections of your computer. Which of the following will you use?
You are using a Windows-based sniffer named ASniffer to record the data traffic of a network. You have extracted the following IP Header information of a randomly chosen packet from the sniffer's log:
45 00 00 28 00 00 40 00 29 06 43 CB D2 D3 82 5A 3B 5E AA 72
Which of the following TTL decimal values and protocols are being carried by the IP Header of this packet?
You are using the TRACERT utility to trace the route to passguide.com. You receive the following output:
Which of the following conclusions can you draw from viewing the output?
Each correct answer represents a complete solution. Choose two.
Which of the following is used as a default port by the TELNET utility?
Sandra, an expert computer user, hears five beeps while booting her computer that has AMI BIOS; and after that her computer stops responding. Sandra knows that during booting process POST produces different beep codes for different types of errors. Which of the following errors refers to this POST beep code?
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate computer of an unfaithful employee of SecureEnet Inc. Suspect's computer runs on Windows operating system. Which of the following sources will Adam investigate on a Windows host to collect the electronic evidences?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator of a TCP/IP network. You are having DNS resolution problem. Which of the following utilities will you use to diagnose the problem?
Which of the following is a valid IP address for class B Networks?
Maria works as the Chief Security Officer for passguide Inc. She wants to send secret messages to the CEO of the company. To secure these messages, she uses a technique of hiding a secret message within an ordinary message. The technique provides 'security through obscurity'. What technique is Maria using?
Which of the following IPv4 to IPv6 transition methods uses encapsulation of IPv6 packets to traverse IPv4 networks?
Which of the following is the default port for Hypertext Transfer Protocol (HTTP)?
Which of the following programs is used to add words to spam e-mails so that the e-mail is not considered spam and therefore is delivered as if it were a normal message?
In which of the following IDS evasion attacks does an attacker send a data packet such that IDS accepts the data packet but the host computer rejects it?
Sasha wants to add an entry to your DNS database for your mail server. Which of the following types of resource records will she use to accomplish this?
Which of the following command-line utilities is used to show the state of current TCP/IP connections?
Which of the following techniques allows probing firewall rule-sets and finding entry points into the targeted system or network?
Computer networks and the Internet are the prime mode of Information transfer today. Which of the following is a technique used for modifying messages, providing Information and Cyber security, and reducing the risk of hacking attacks during communications and message passing over the Internet?
Which of the following components are usually found in an Intrusion detection system (IDS)?
Each correct answer represents a complete solution. Choose two.
Sandra, a novice computer user, works on Windows environment. She experiences some problem regarding bad sectors formed in a hard disk of her computer. She wants to run CHKDSK command to check the hard disk for bad sectors and to fix the errors, if any, occurred. Which of the following switches will she use with CHKDSK command to accomplish the task?
You work as a System Administrator for McNeil Inc. The company has a Linux-based network. You are a root user on the Red Hat operating system. Your network is configured for IPv6 IP addressing. Which of the following commands will you use to test TCP/IP connectivity?
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 Active Directory-based single forest multiple domain IPv4 network. All the DNS servers on the network run Windows Server 2008. The users in the network use NetBIOS name to connect network application on the network. You have migrated the network to IPv6-enabled network. Now you want to enable DNS Server to perform lookups in GlobalNames Zone. Which of the following commands will you use to accomplish the task?
Which of the following file systems is designed by Sun Microsystems?
Fill in the blank with the appropriate term.
___________is the practice of monitoring and potentially restricting the flow of information outbound from one network to another
You work as a Network Administrator for TechPerfect Inc. The company has a corporate intranet setup. A router is configured on your network to connect outside hosts to the internetworking. For security, you want to prevent outside hosts from pinging to the hosts on the internetwork. Which of the following steps will you take to accomplish the task?
You are concerned about outside attackers penetrating your network via your company Web server. You wish to place your Web server between two firewalls. One firewall between the Web server and the outside world. The other between the Web server and your network. What is this called?
Which of the following honeypots is a low-interaction honeypot and is used by companies or corporations for capturing limited information about malicious hackers?
Which of the following tools allows an attacker to intentionally craft the packets to gain unauthorized access?
Each correct answer represents a complete solution. Choose two.
In which of the following IKE phases the IPsec endpoints establish parameters for a secure ISAKMP session?
Ryan, a malicious hacker submits Cross-Site Scripting (XSS) exploit code to the Website of Internet forum for online discussion. When a user visits the infected Web page, code gets automatically executed and Ryan can easily perform acts like account hijacking, history theft etc.
Which of the following types of Cross-Site Scripting attack Ryan intends to do?
Which of the following methods is a behavior-based IDS detection method?
Windump is a Windows port of the famous TCPDump packet sniffer available on a variety of platforms. In order to use this tool on the Windows platform a user must install a packet capture library.
What is the name of this library?
Which of the following well-known ports is used by BOOTP?
Which of the following tools are used to determine the hop counts of an IP packet?
Each correct answer represents a complete solution. Choose two.
Which of the following algorithms produces a digital signature which is used to authenticate the bit-stream images?
Which of the following ports is used for DNS services?
John works as a professional Ethical Hacker. He has been assigned a project to test the security of John wants to redirect all TCP port 80 traffic to UDP port 40, so that he can bypass the firewall of the We-are-secure server. Which of the following tools will John use to accomplish his task?
Which of the following methods is used by forensic investigators to acquire an image over the network in a secure manner?
Which of the following attacks is used to hack simple alphabetical passwords?
Sandra, a novice computer user, works on Windows environment. She experiences some problem regarding bad sectors formed in a hard disk of her computer. She wants to run CHKDSK command to check the hard disk for bad sectors and to fix the errors, if any, occurred. Which of the following switches will she use with CHKDSK command to accomplish the task?
Which of the following proxy servers can be used for spamming?
Which of the following attacks is designed to deduce the brand and/or version of an operating system or application?
Which of the following is a checksum algorithm?
You work as a Network Administrator for Tech Perfect Inc. Your company has a Windows 2000- based network. You want to verify the connectivity of a host in the network. Which of the following utilities will you use?
Routers work at which layer of the OSI reference model?
Mark works as a Network Security Administrator for BlueWells Inc. The company has a Windowsbased network. Mark is giving a presentation on Network security threats to the newly recruited employees of the company. His presentation is about the External threats that the company recently faced in the past. Which of the following statements are true about external threats?
Each correct answer represents a complete solution. Choose three.
Which of the following NETSH commands for interface Internet protocol version 4 (IPv4) is used to delete a DNS server or all DNS servers from a list of DNS servers for a specified interface or for all interfaces?
Which of the following hacking tools provides shell access over ICMP?
Which of the following types of Intrusion detection systems (IDS) is used for port mirroring?
What is the process of detecting unauthorized access known as?
Which of the following is NOT an Intrusion Detection System?
Mark works as a Network administrator for SecureEnet Inc. His system runs on Mac OS X. He wants to boot his system from the Network Interface Controller (NIC). Which of the following snag keys will Mark use to perform the required function?