Which of the following tools is used to analyze a system and report any unsigned drivers found?
Which of the following tools is used to collect volatile data over a network?
Which of the following is true for XSS, SQL injection, and RFI?
Steve works as a Network Administrator for Blue Tech Inc. All client computers in the company run the Windows Vista operating system. He often travels long distances on official duty. While traveling, he connects to the office server through his laptop by using remote desktop connection.
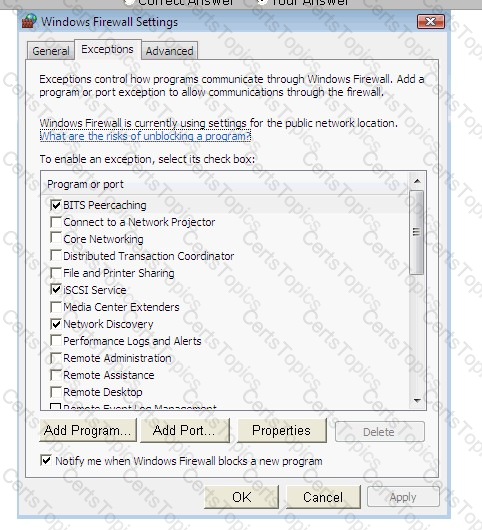
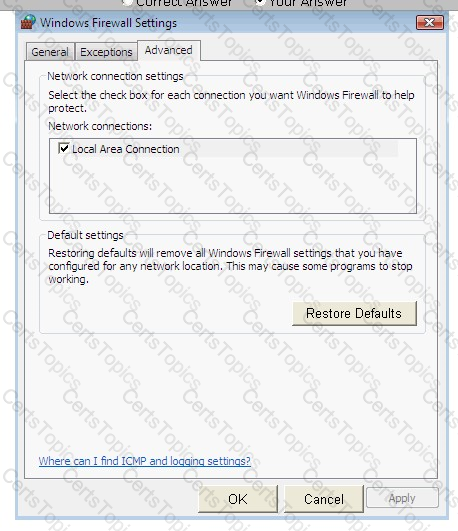
He wants to run an application that is available on the server of the company. When he connects to the server, he gets a message that the connection is blocked by the firewall. He returns to his office to resolve the issue. He opens the Windows Firewall Settings dialog box. What actions should he perform in the dialog box given below to accomplish the task?