Which of the following is a formula, practice, process, design, instrument, pattern, or compilation of information which is not generally known, but by which a business can obtain an economic advantage over its competitors?
Which of the following Acts enacted in United States amends Civil Rights Act of 1964, providing technical changes affecting the length of time allowed to challenge unlawful seniority provisions, to sue the federal government for discrimination and to bring age discrimination claims?
In which of the following security tests does the security testing team simulate as an employee or other person with an authorized connection to the organization's network?
Which of the following is NOT an example of passive footprinting?
Your Windows XP hard drive has 2 partitions. The system partition is NTFS and the other is FAT. You wish to encrypt a folder created on the system partition for the purpose of data security. Which of the following statements is true about this situation?
You work as a Network Administrator for Tech Perfect Inc. The company has a Linux-based network. Users complain that they are unable to access resources on the network. However, there was no such problem the previous day. They are receiving the following error messages regularly:
Unable to resolve host name
As your primary step for resolving the issue, which of the following services will you verify whether it is running or not?
What are the purposes of audit records on an information system?
Each correct answer represents a complete solution. Choose two.
Which of the following laws enacted in United States makes it illegal for an Internet Service Provider (ISP) to allow child pornography to exist on Web sites?
Which of the following statements about SD cards are true?
Each correct answer represents a complete solution. Choose two.
The Klez worm is a mass-mailing worm that exploits a vulnerability to open an executable attachment even in Microsoft Outlook's preview pane. The Klez worm gathers email addresses from the entries of the default Windows Address Book (WAB). Which of the following registry values can be used to identify this worm?
Which of the following sections of United States Economic Espionage Act of 1996 criminalizes the misappropriation of trade secrets related to or included in a product that is produced for or placed in interstate commerce, with the knowledge or intent that the misappropriation will injure the owner of the trade secret?
Adrian, the Network Administrator for Peach Tree Inc., wants to install a new computer on the company's network. He asks his assistant to make a boot disk with minimum files. The boot disk will be used to boot the computer, which does not have an operating system installed, yet. Which of the following files will he include on the disk?
In a Windows 98 computer, which of the following utilities is used to convert a FAT16 partition to FAT32?
You work as the Network Administrator for McNeil Inc. The company has a Unix-based network. You want to set the hard disk geometry parameters, cylinders, heads, and sectors. Which of the following Unix commands can you use to accomplish the task?
Which of the following steps should be performed in order to optimize a system performance?
Each correct answer represents a complete solution. Choose three.
You want to change the attribute of a file named ACE.TXT to Hidden. Which command line will enable you to set the attribute?
You work as a Network Administrator for Web World Inc. You want to host an e-commerce Web site on your network. You want to ensure that storage of credit card information is secure. Which of the following conditions should be met to accomplish this?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is a correct sequence of different layers of Open System Interconnection (OSI) model?
Which of the following is the process of overwriting all addressable locations on a disk?
Which of the following methods is used by forensic investigators to acquire an image over the network in a secure manner?
Nathan works as a professional Ethical Hacker. He wants to see all open TCP/IP and UDP ports of his computer. Nathan uses the netstat command for this purpose but he is still unable to map open ports to the running process with PID, process name, and path. Which of the following commands will Nathan use to accomplish the task?
Which of the following tools can be used by a user to hide his identity?
Each correct answer represents a complete solution. Choose all that apply.
Normally, RAM is used for temporary storage of data. But sometimes RAM data is stored in the hard disk, what is this method called?
You company suspects an employee of sending unauthorized emails to competitors. These emails are alleged to contain confidential company data. Which of the following is the most important step for you to take in preserving the chain of custody?
Which of the following tools are used for footprinting?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following file systems cannot be used to install an operating system on the hard disk drive?
Each correct answer represents a complete solution. Choose two.
Which of the following types of evidence proves or disproves a specific act through oral testimony based on information gathered through the witness's five senses?
By gaining full control of router, hackers often acquire full control of the network. Which of the following methods are commonly used to attack Routers?
Each correct answer represents a complete solution. Choose all that apply.
The incident response team has turned the evidence over to the forensic team. Now, it is the time to begin looking for the ways to improve the incident response process for next time. What are the typical areas for improvement?
Each correct answer represents a complete solution. Choose all that apply.
Adam works as a professional Computer Hacking Forensic Investigator with the local police of his area. A project has been assigned to him to investigate a PDA seized from a local drug dealer. It is expected that many valuable and important information are stored in this PDA. Adam follows investigative methods, which are required to perform in a pre-defined sequential manner for the successful forensic investigation of the PDA. Which of the following is the correct order to perform forensic investigation of PDA?
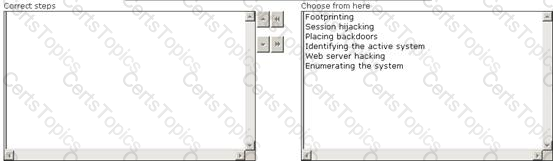
Maria works as a professional Ethical Hacker. She recently got a project to test the security of Arrange the three pre-test phases of the attack to test the security of weare-secure.
Mark works as a Network Administrator for Net Perfect Inc. The company has a Linux-based network. Mark installs a Checkpoint Firewall NGX on a SecurePlatform device. He performs a scheduled backup of his system settings and products configuration. Where are these backup files stored?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is the Windows feature on which the file management can be performed by a PC user?
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network. You are configuring a wireless LAN on the network. You experience interference on your network. Through investigation, you come to know that three foreign WAPs are within the range of your LAN. Although they have different SSIDs than yours, they are working on the same channel as yours.
Which of the following steps will you take to reduce the interference?
Which of the following provides high availability of data?
Which of the following file systems provides integrated security?
Which utility enables you to access files from a Windows .CAB file?
This type of virus infects programs that can execute and load into memory to perform predefined steps for infecting systems. It infects files with the extensions .EXE, .COM, .BIN, and .SYS. As it can replicate or destroy these types of files, the operating system becomes corrupted and needs reinstallation. This type of virus is known as __________.
Which of the following diagnostic codes sent by POST to the internal port h80 refers to the system board error?
Which of the following U.S. Federal laws addresses computer crime activities in communication lines, stations, or systems?
In the United States, Title VII of the 1964 Civil Rights Act was formulated to protect an employee from discrimination on the basis of religion, color, race, national origin, and sex. This law makes discrimination in employment illegal. Which of the following was the original emphasis of the Act?
John is a black hat hacker. FBI arrested him while performing some email scams. Under which of the following US laws will john be charged?
You are a professional Computer Hacking forensic investigator. You have been called to collect the evidences of Buffer Overflows or Cookie snooping attack. Which of the following logs will you review to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
John used to work as a Network Administrator for We-are-secure Inc. Now he has resigned from the company for personal reasons. He wants to send out some secret information of the company. To do so, he takes an image file and simply uses a tool image hide and embeds the secret file within an image file of the famous actress, Jennifer Lopez, and sends it to his Yahoo mail id. Since he is using the image file to send the data, the mail server of his company is unable to filter this mail. Which of the following techniques is he performing to accomplish his task?
Which of the following Windows XP system files handles memory management, I/O operations, and interrupts?
Mark has been hired by a company to work as a Network Assistant. He is assigned the task to
configure a dial-up connection. He is configuring a laptop. Which of the following protocols should he disable to ensure that the password is encrypted during remote access?
Which of the following representatives of incident response team takes forensic backups of the systems that are the focus of the incident?