The incident response team has turned the evidence over to the forensic team. Now, it is the time to begin looking for the ways to improve the incident response process for next time. What are the typical areas for improvement?
Each correct answer represents a complete solution. Choose all that apply.
Adam works as a professional Computer Hacking Forensic Investigator with the local police of his area. A project has been assigned to him to investigate a PDA seized from a local drug dealer. It is expected that many valuable and important information are stored in this PDA. Adam follows investigative methods, which are required to perform in a pre-defined sequential manner for the successful forensic investigation of the PDA. Which of the following is the correct order to perform forensic investigation of PDA?
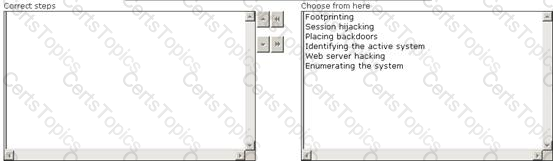
Maria works as a professional Ethical Hacker. She recently got a project to test the security of Arrange the three pre-test phases of the attack to test the security of weare-secure.
Mark works as a Network Administrator for Net Perfect Inc. The company has a Linux-based network. Mark installs a Checkpoint Firewall NGX on a SecurePlatform device. He performs a scheduled backup of his system settings and products configuration. Where are these backup files stored?
Each correct answer represents a complete solution. Choose all that apply.