Review the Application Control log.

Which configuration caused the IPS engine to generate this log?
Refer to the exhibits.
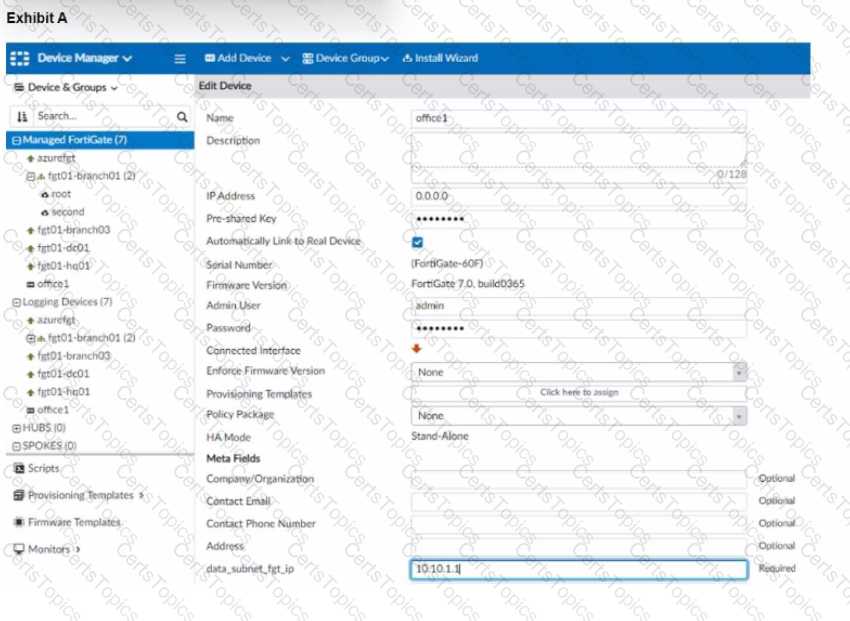
The exhibit shows a FortiGate model device that will be used for zero touch provisioning and a CLI Template.
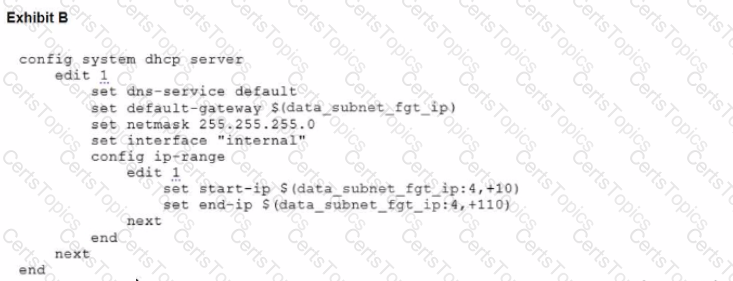
To facilitate a more efficient roll out of FortiGate devices, you are tasked with using meta fields with the CLI Template to configure the DHCP server on the "office1" FortiGate.
Given this scenario, what would be the output of the config ip-range section on the CLI Template?
A customer would like to improve the performance of a FortiGate VM running in an Azure D4s_v3 instance, but they already purchased a BYOL VM04 license.
Which two actions will improve performance the most without making a FortiGate license change? (Choose two.)
Refer to the CLI output:
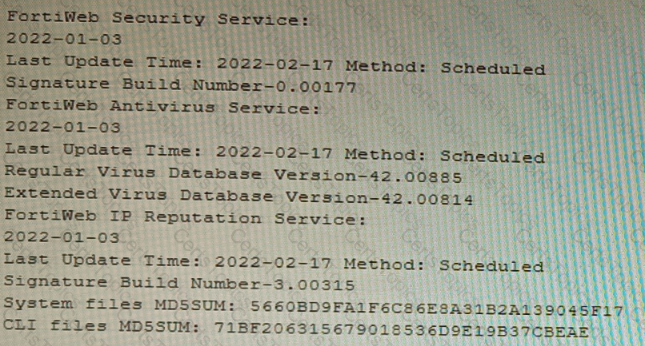
Given the information shown in the output, which two statements are correct? (Choose two.)
Refer to the exhibit, which shows diagnostic output.
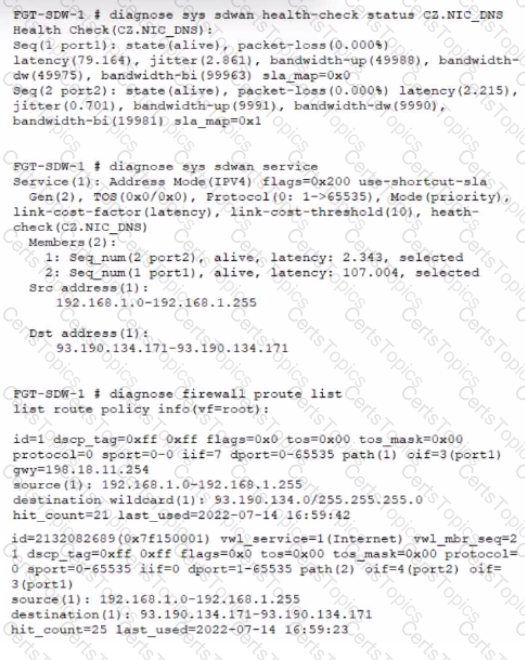
A customer reports that ICMP traffic flow from 192.168.1.11 to 93.190.134.171 is not corresponding to the SD-WAN setup.
What is the problem in this scenario?
Which two types of interface have built-in active bypass in FortiDDoS devices? (Choose two.)
You are performing a packet capture on a FortiGate 2600F with the hyperscale licensing installed. You need to display on screen all egress/ingress packets from the port16 interface that have been offloaded to the NP7.
Which three commands need to be run? (Choose three.)
Refer to the exhibit.
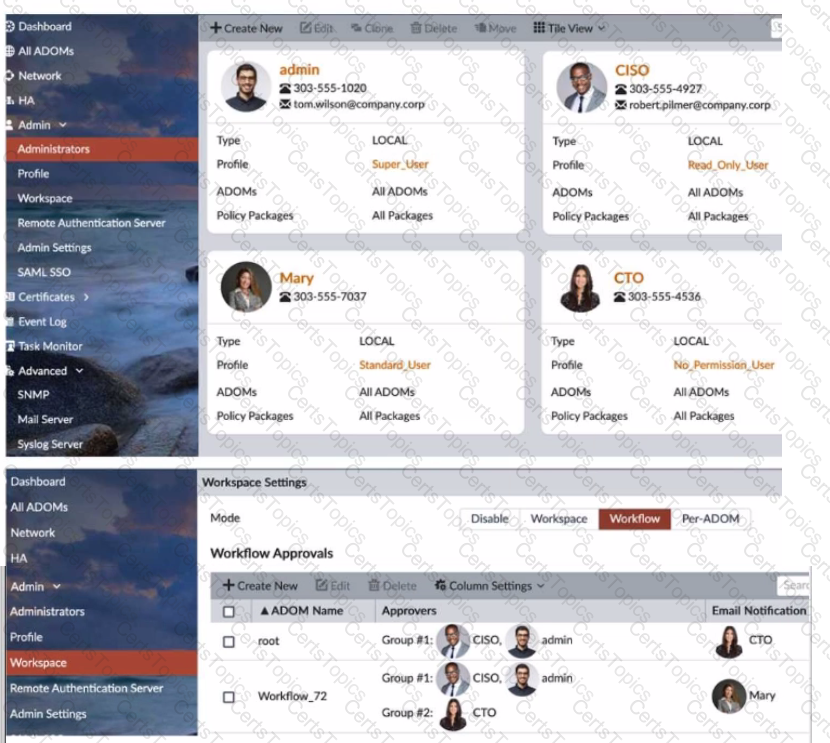
The Company Corp administrator has enabled Workflow mode in FortiManager and has assigned approval roles to the current administrators. However, workflow approval does not function as expected. The CTO is currently unable to approve submitted changes.
Given the exhibit, which two possible solutions will resolve the workflow approval problems with the Workflow_72 ADOM? (Choose two.)
A customer wants to use the FortiAuthenticator REST API to retrieve an SSO group called SalesGroup. The following API call is being made with the 'curl' utility:

Which two statements correctly describe the expected behavior of the FortiAuthenticator REST API? (Choose two.)
Refer to The exhibit showing a FortiEDR configuration.
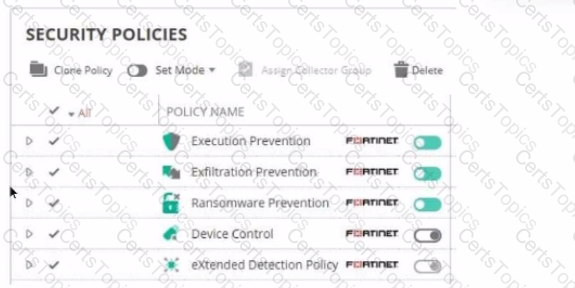
Based on the exhibit, which statement is correct?
Refer to the exhibits.
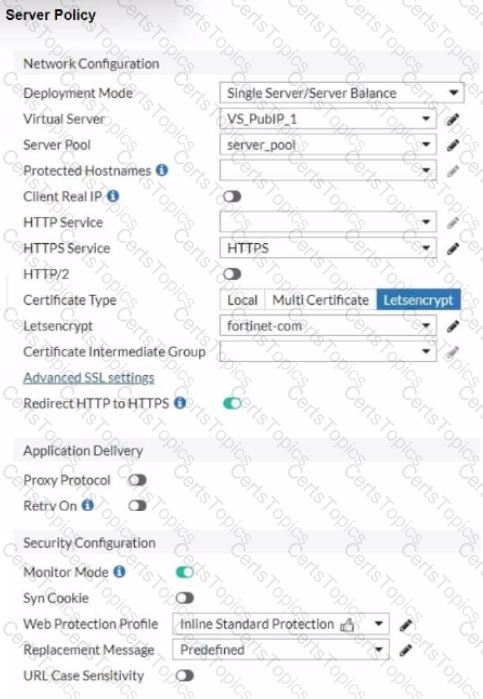
You are configuring a Let's Encrypt certificate to enable SSL protection to your website. When FortiWeb tries to retrieve the certificate, you receive a certificate status failed, as shown below.

Based on the Server Policy settings shown in the exhibit, which two configuration changes will resolve this issue? (Choose two.)
Refer to the exhibit showing a FortiView monitor screen.
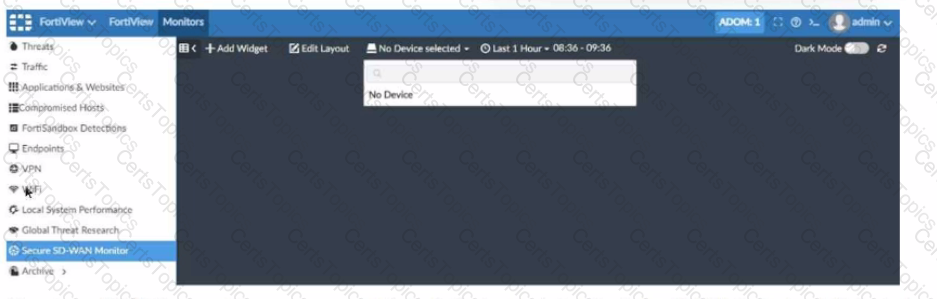
After a Secure SD-WAN implementation a customer reports that in FortiAnalyzer under FortiView Secure SD-WAN Monitor there is No Device for selection.
What can cause this issue?
You are responsible for recommending an adapter type for NICs on a FortiGate VM that will run on an ESXi Hypervisor. Your recommendation must consider performance as the main concern, cost is not a factor. Which adapter type for the NICs will you recommend?
Refer to the exhibit.
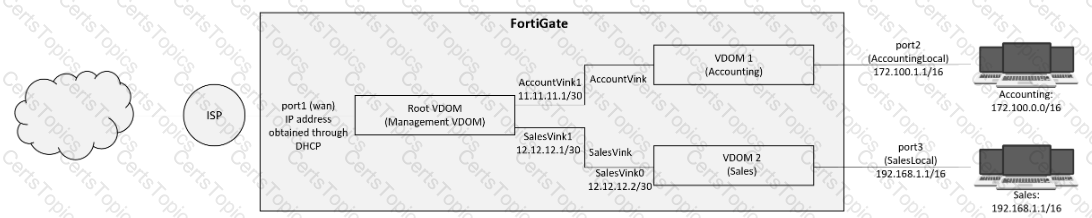
A customer has deployed a FortiGate 300E with virtual domains (VDOMs) enabled in the multi-VDOM mode. There are three VDOMs: Root is for management and internet access, while VDOM 1 and VDOM 2 are used for segregating internal traffic. AccountVInk and SalesVInk are standard VDOM links in Ethernet mode.
Given the exhibit, which two statements below about VDOM behavior are correct? (Choose two.)
Refer to the exhibit, which shows a VPN topology.
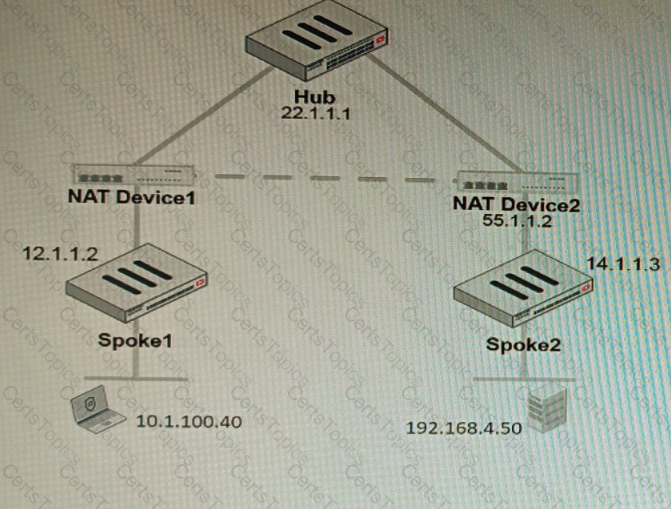
The device IP 10.1.100.40 downloads a file from the FTP server IP 192.168.4.50
Referring to the exhibit, what will be the traffic flow behavior if ADVPN is configured in this environment?
An HA topology is using the following configuration:
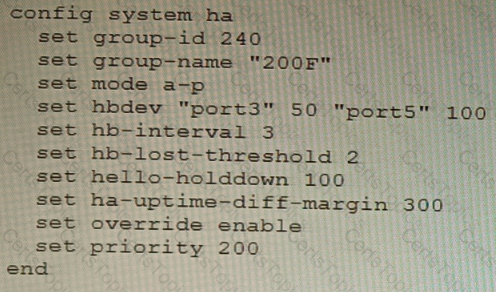
Based on this configuration, how long will it take for a failover to be detected by the secondary cluster member?
Refer to the exhibits.
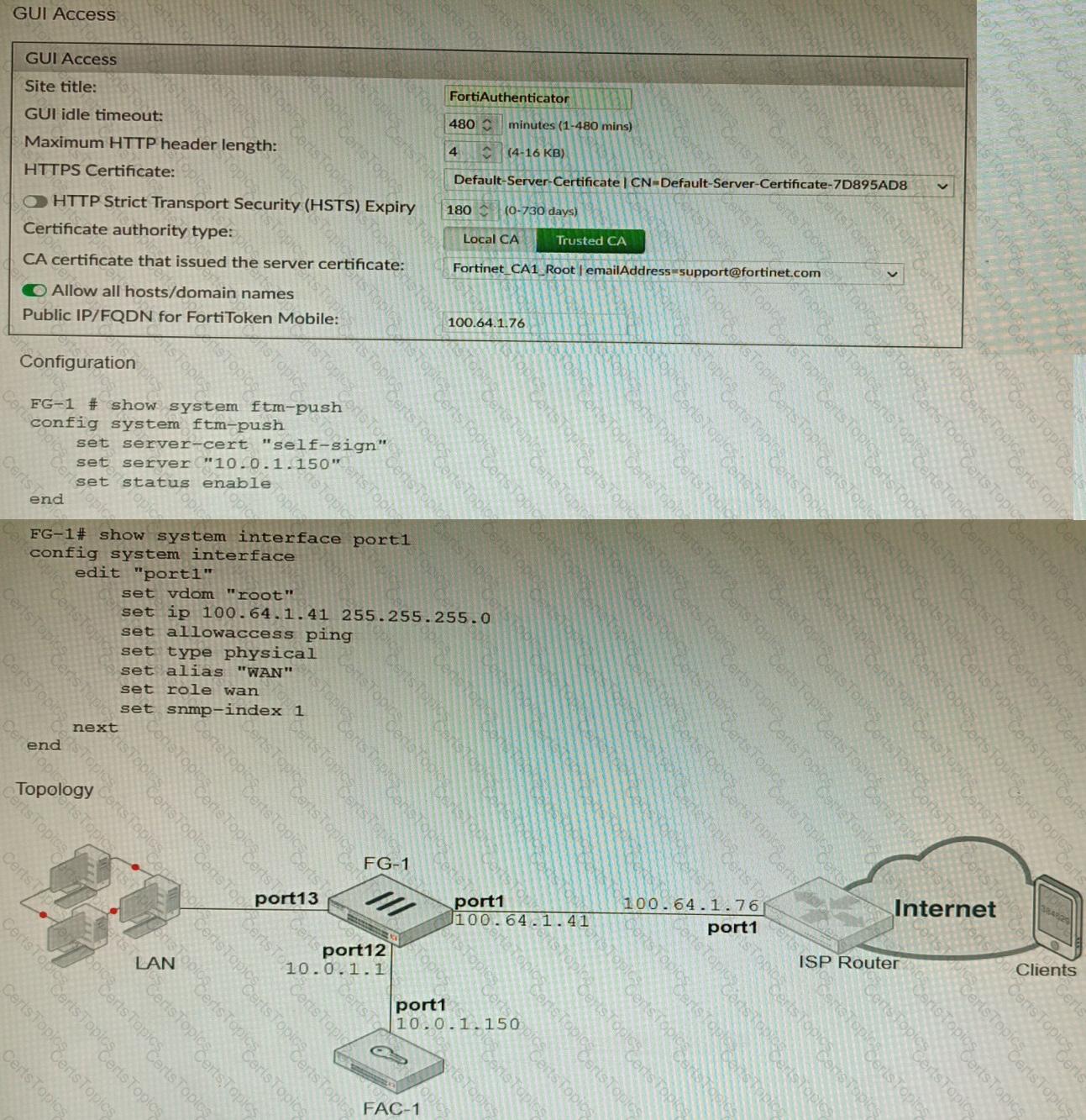
An administrator has configured a FortiGate and Forti Authenticator for two-factor authentication with FortiToken push notifications for their SSL VPN login. Upon initial review of the setup, the administrator has discovered that the customers can manually type in their two-factor code and authenticate but push notifications do not work
Based on the information given in the exhibits, what must be done to fix this?
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the OCSP server.
Part of the FortiGate configuration is shown below:
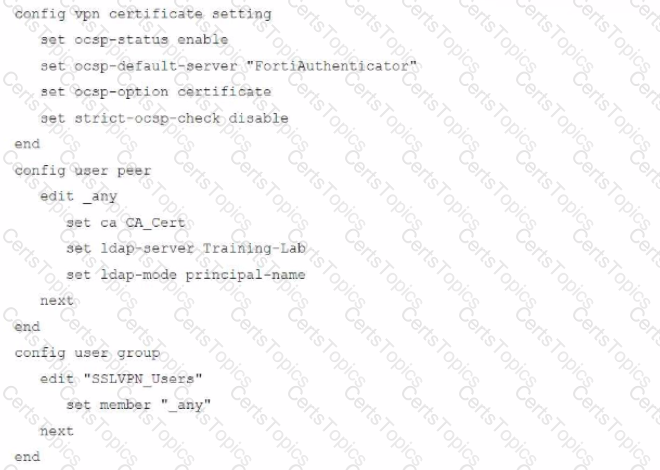
Based on this configuration, which authentication scenario will FortiGate deny?
SD-WAN is configured on a FortiGate. You notice that when one of the internet links has high latency the time to resolve names using DNS from FortiGate is very high.
You must ensure that the FortiGate DNS resolution times are as low as possible with the least amount of work.
What should you configure?
Refer to the exhibit.
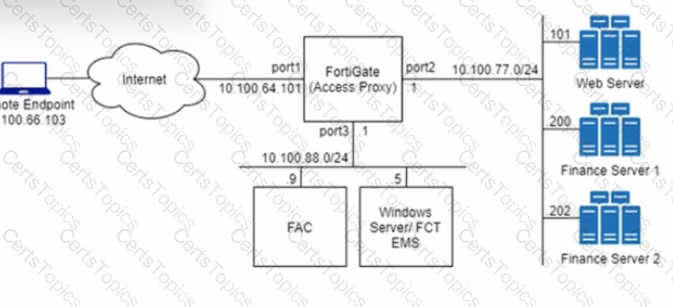
An HTTPS access proxy is configured to demonstrate its function as a reverse proxy on behalf of the web server it is protecting. It verifies user identity, device identity, and trust context, before granting access to the protected source. It is assumed that the FortiGate EMS fabric connector has already been successfully connected.
You need to ensure that ZTNA access through the FortiGate will redirect users to the FortiAuthenticator to perform username/password and multifactor authentication to validate access prior to accessing resources behind the FortiGate.
In this scenario, which two further steps need to be taken on the FortiGate? (Choose two.)
Refer to the exhibit.

You need to create a base SD-WAN configuration that includes SD-WAN rules and Performance SLAs for spoke sites with various connectivity types. It needs to be done in a way that can be easily applied to new sites with a minimum amount of change. How should you create the SD-WAN zones?
Refer to the exhibits.

The exhibits show a diagram of a requested topology and the base IPsec configuration.
A customer asks you to configure ADVPN via two internet underlays. The requirement is that you use one interface with a single IP address on DC FortiGate.
In this scenario, which feature should be implemented to achieve this requirement?
Which feature must you enable on the BGP neighbors to accomplish this goal?
An administrator discovers that CPU utilization of a FortiGate-200F is high and determines that no traffic is being accelerated by hardware.
Why is no traffic being accelerated by hardware?
Refer to the exhibits.
Exhibit A
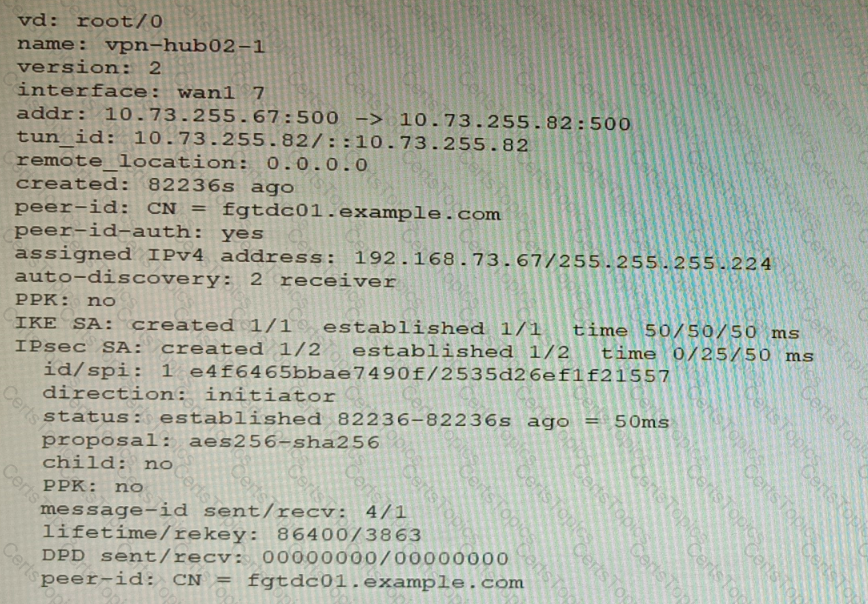
Exhibit B
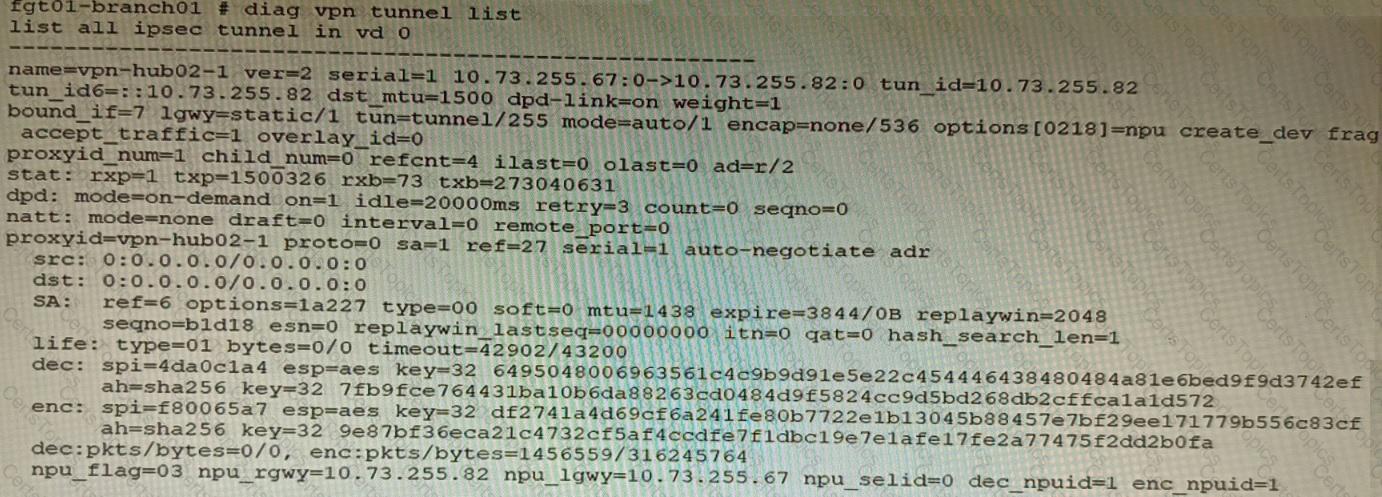
Exhibit C
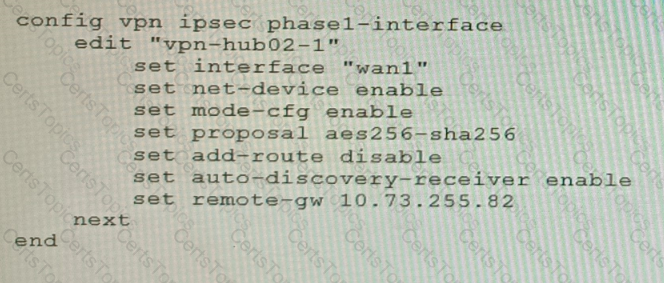
A customer is trying to set up a VPN with a FortiGate, but they do not have a backup of the configuration. Output during a troubleshooting session is shown in the exhibits A and B and a baseline VPN configuration is shown in Exhibit C Referring to the exhibits, which configuration will restore VPN connectivity?
A)
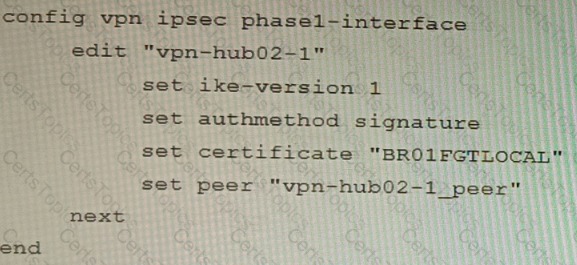
B)
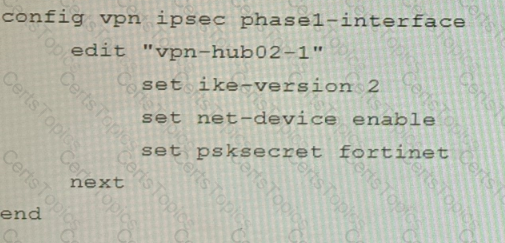
C)
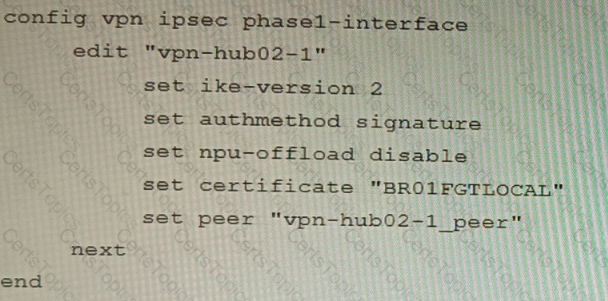
D)
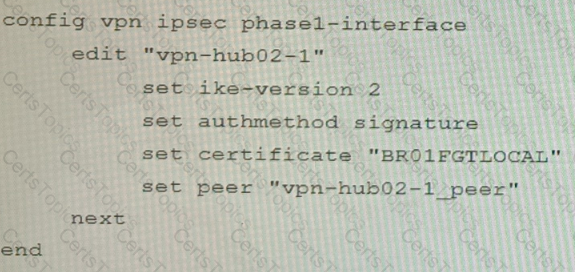
A FortiGate deployment contains the following configuration:
What is the result of this configuration?
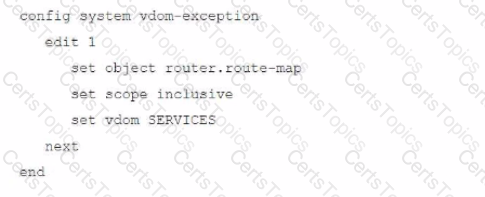
Refer to the exhibit.
What is happening in this scenario?
Refer to the exhibit.
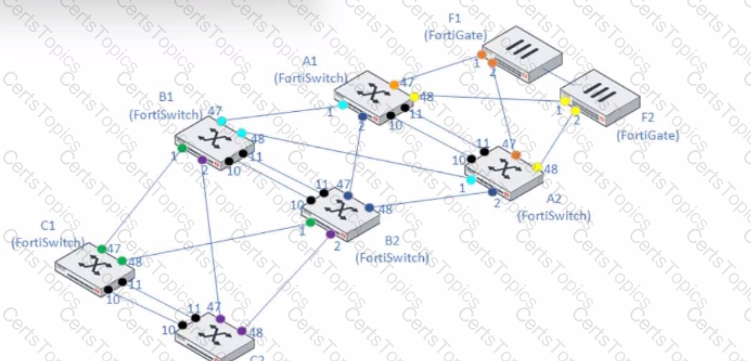
A customer needs to create a multi-tier MCLAG set up with the topology as shown in the exhibit.
A1/A2
B1/B2
C1/C2
Which command snippet should be applied to it, to allow active/active links in this topology?
A customer is operating a FortiWeb cluster in a high volume active-active HA group consisting of eight FortiWeb appliances. One of the secondary members is handling traffic for one specific VIP.
What will happen with the traffic if that secondary FortiWeb appliance fails?
A FortiGate running FortiOS 7.2.0 GA is configured in multi-vdom mode with a vdom set to vdom type Admin and another vdom set to vdom type Traffic.
Which two GUI sections are available on both VDOM types? (Choose two.)
You are migrating the branches of a customer to FortiGate devices. They require independent routing tables on the LAN side of the network.
After reviewing the design, you notice the firewall will have many BGP sessions as you have two data centers (DC) and two ISPs per DC while each branch is using at least 10 internal segments.
Based on this scenario, what would you suggest as the more efficient solution, considering that in the future the number of internal segments, DCs or internet links per DC will increase?