Refer to the exhibit, which shows an enterprise network connected to an internet service provider.
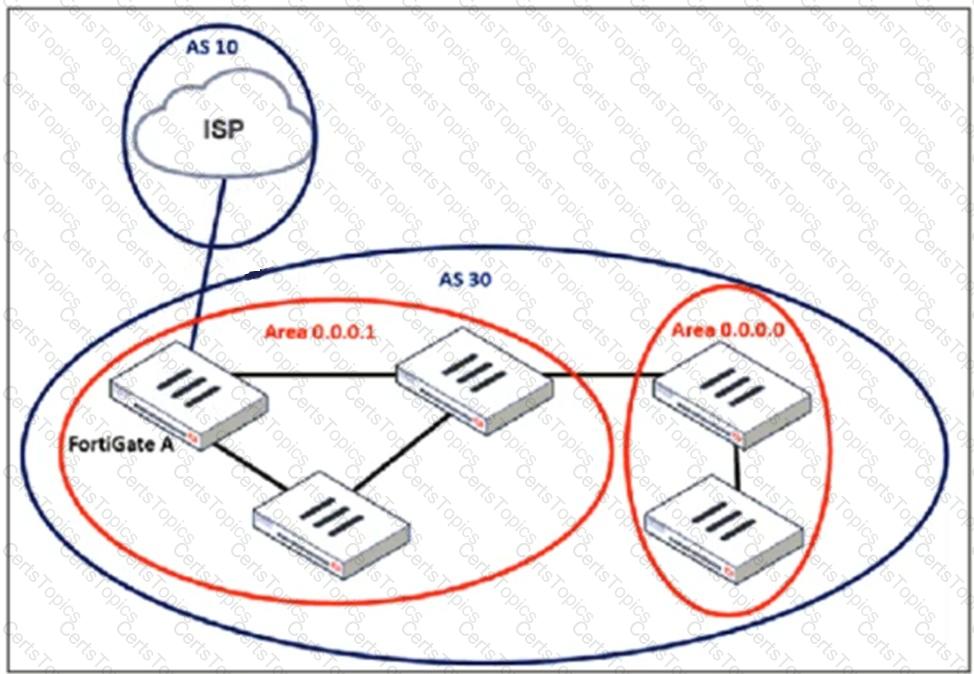
An administrator must configure a loopback as a BGP source to connect to the ISP.
Which two commands are required to establish the connection? (Choose two.)
Refer to the exhibit, which shows a command output.

FortiGate_A and FortiGate_B are members of an FGSP cluster in an enterprise network.
While testing the cluster using the ping command, the administrator monitors packet loss and found that the session output on FortiGate_B is as shown in the exhibit.
What could be the cause of this output on FortiGate_B?
Refer to the exhibit, which contains the partial output of an OSPF command.
An administrator is checking the OSPF status of a FortiGate device and receives the output shown in the exhibit.
What two conclusions can the administrator draw? (Choose two.)
An administrator must standardize the deployment of FortiGate devices across branches with consistent interface roles and policy packages using FortiManager.
What is the recommended best practice for interface assignment in this scenario?
Refer to the exhibits. The exhibits show a network topology, a firewall policy, and an SSL/SSH inspection profile configuration.
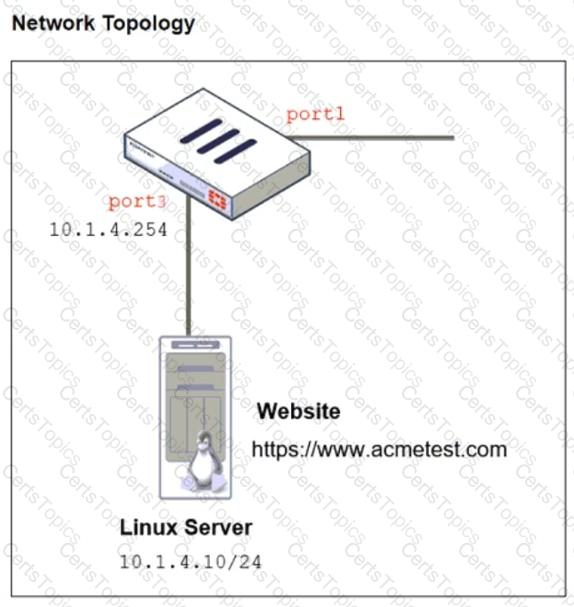
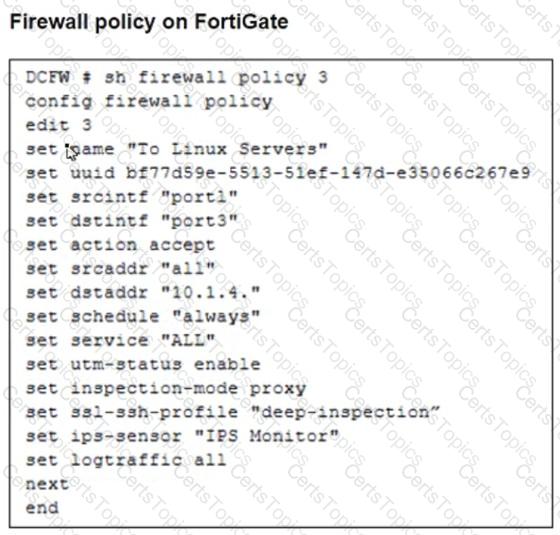
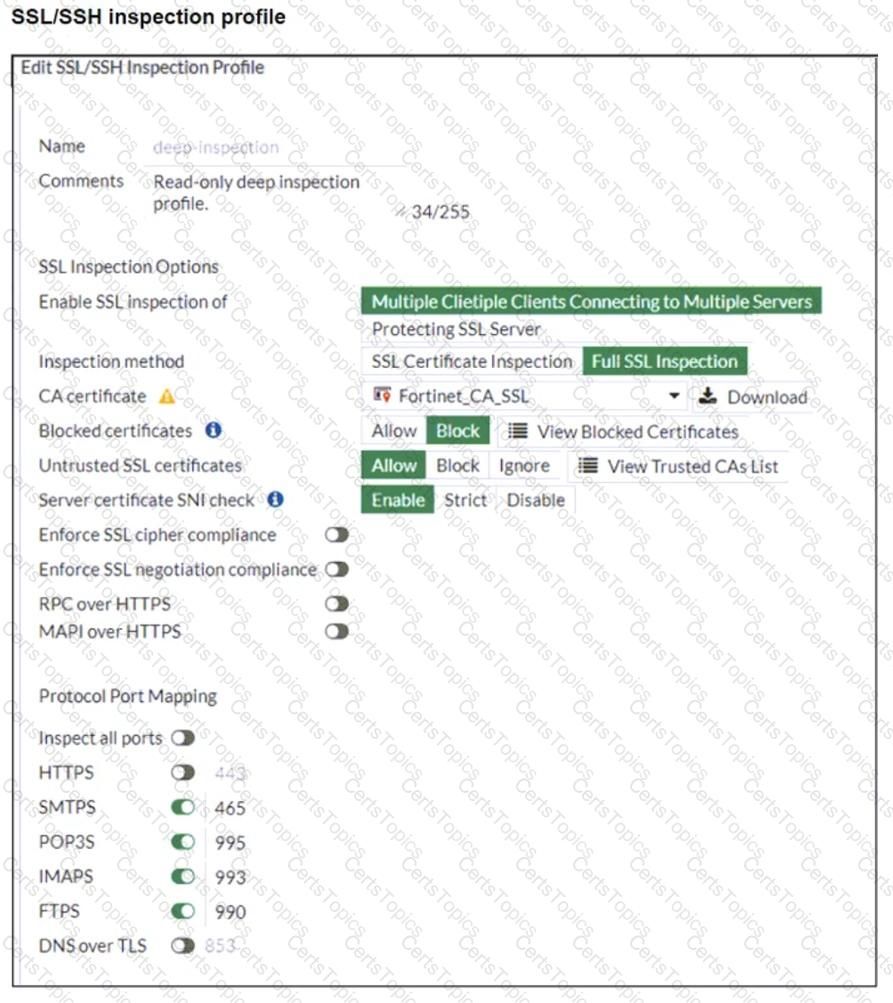
Why is FortiGate unable to detect HTTPS attacks on firewall policy ID 3 targeting the Linux server?
The IT department discovered during the last network migration that all zero phase selectors in phase 2 IPsec configurations impacted network operations.
What are two valid approaches to prevent this during future migrations? (Choose two.)
Refer to the exhibit, which shows the ADVPN network topology and partial BGP configuration.
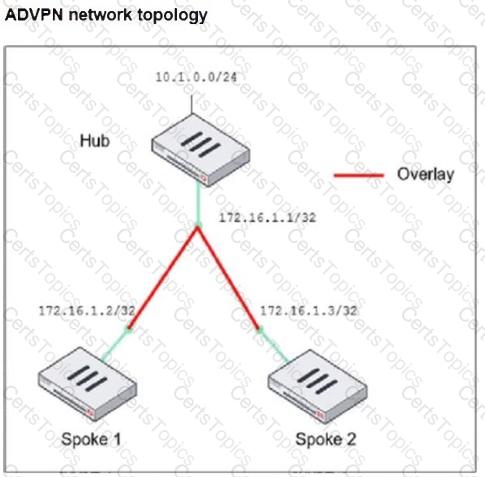

Which two parameters must an administrator configure in the config neighbor range for spokes shown in the exhibit? (Choose two.)
Refer to the exhibit, which shows a LAN interface connected from FortiGate to two FortiSwitch devices.
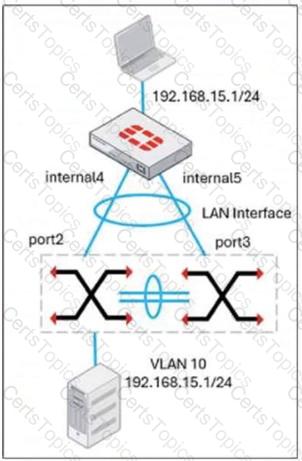
What two conclusions can you draw from the corresponding LAN interface? (Choose two.)
What does the command set forward-domain
An administrator is designing an ADVPN network for a large enterprise with spokes that have varying numbers of internet links. They want to avoid a high number of routes and peer connections at the hub.
Which method should be used to simplify routing and peer management?
A company that acquired multiple branches across different countries needs to install new FortiGate devices on each of those branches. However, the IT staff lacks sufficient knowledge to implement the initial configuration on the FortiGate devices.
Which three approaches can the company take to successfully deploy advanced initial configurations on remote branches? (Choose three.)
Refer to the exhibit, which contains a partial VPN configuration.

What can you conclude from this VPN IPsec phase 1 configuration?
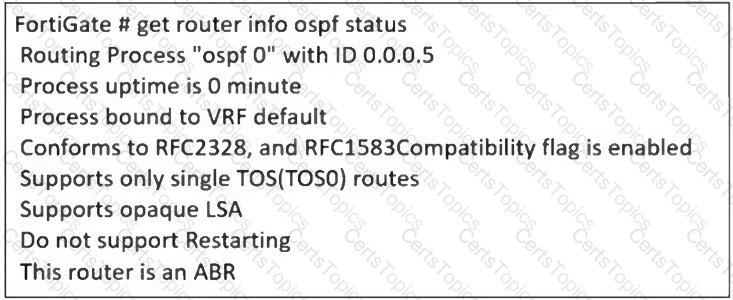
Refer to the exhibit, which contains the partial output of an OSPF command.
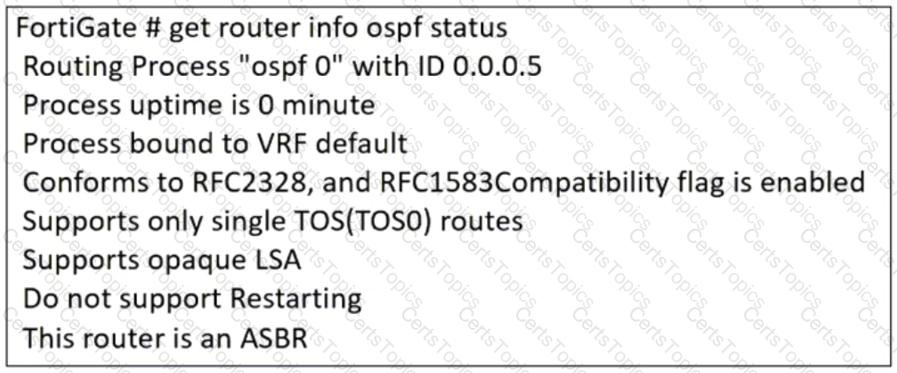
An administrator is checking the OSPF status of a FortiGate device and receives the output shown in the exhibit.
Which statement on this FortiGate device is correct?
A user reports that their computer was infected with malware after accessing a secured HTTPS website. However, when the administrator checks the FortiGate logs, they do not see that the website was detected as insecure despite having an SSL certificate and correct profiles applied on the policy.
How can an administrator ensure that FortiGate can analyze encrypted HTTPS traffic on a website?
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose two.)
Refer to the exhibit, which shows a hub and spokes deployment.
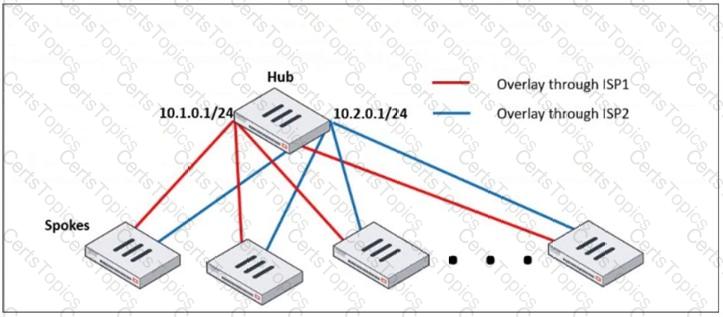
An administrator is deploying several spokes, including the BGP configuration for the spokes to connect to the hub.
Which two commands allow the administrator to minimize the configuration? (Choose two.)
Refer to the exhibit, which shows the HA status of an active-passive cluster.
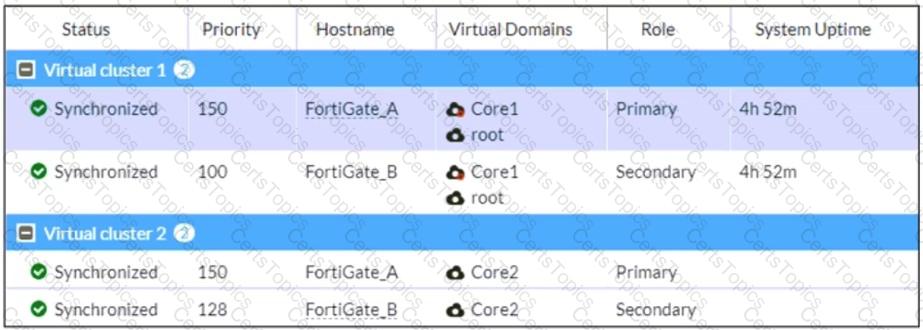
An administrator wants FortiGate_B to handle the Core2 VDOM traffic.
Which modification must the administrator apply to achieve this?