Refer to the exhibit.
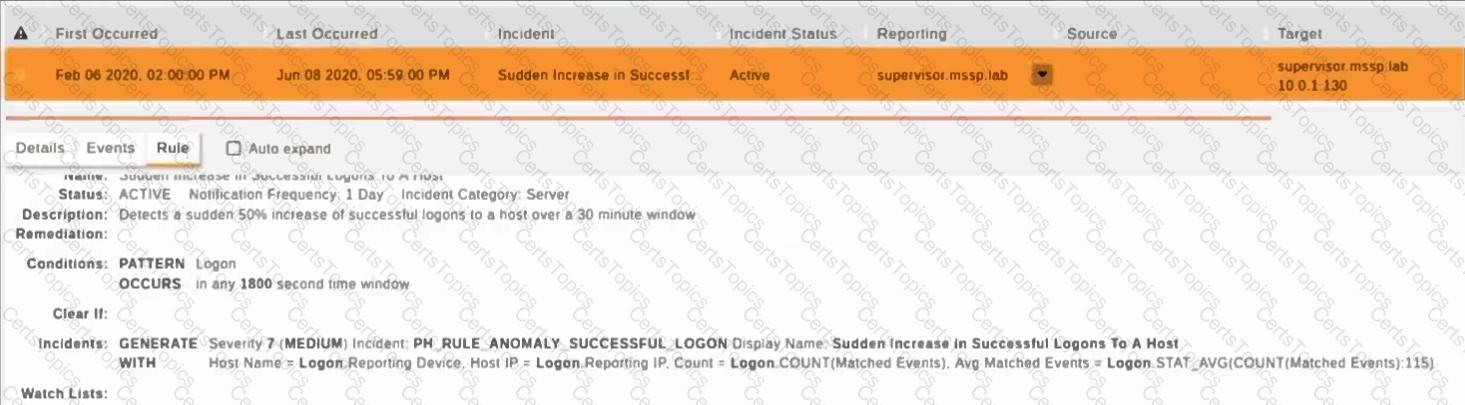
Within what time window is the incident auto cleared?
Which syntax will register a collector to the supervisor?
What is the hourly bucket used in baselining?
A service provider purchased a 500-EPS license and configured a new collector with 100 EPS for customer A, and another collector with 200 EPS for customer B.
How much is in the remaining EPS pool for future customers and for MSSP itself?
Which statement accurately contrasts lookup tables with watchlists?
Refer to the exhibit.
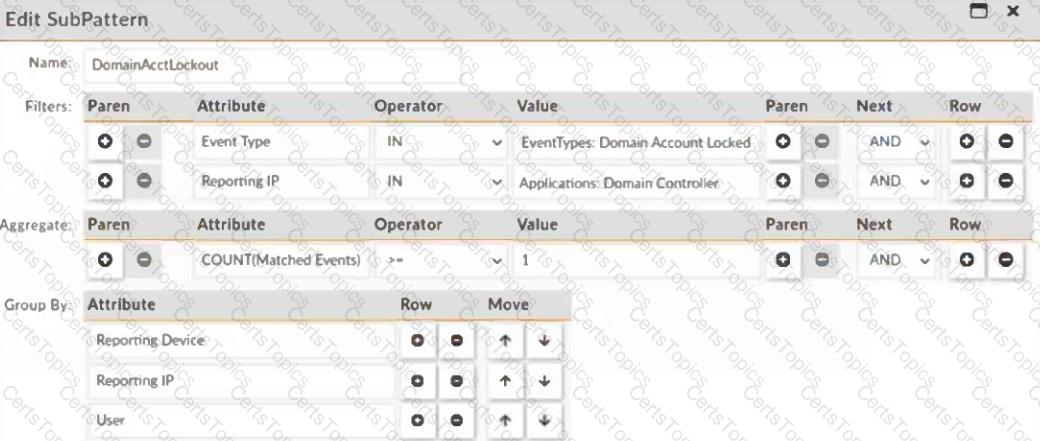
Which statement about the rule filters events shown in the exhibit is true?
Refer to the exhibit.
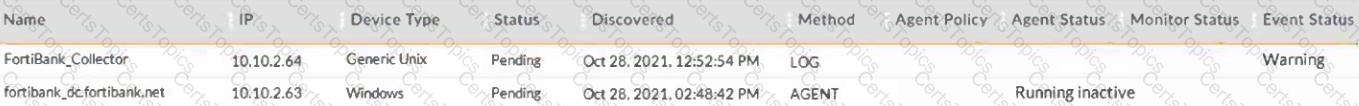
What are three possible reasons why theAgent StatusdisplaysRunning Inactive? (Choose three.)
Refer to the exhibit.
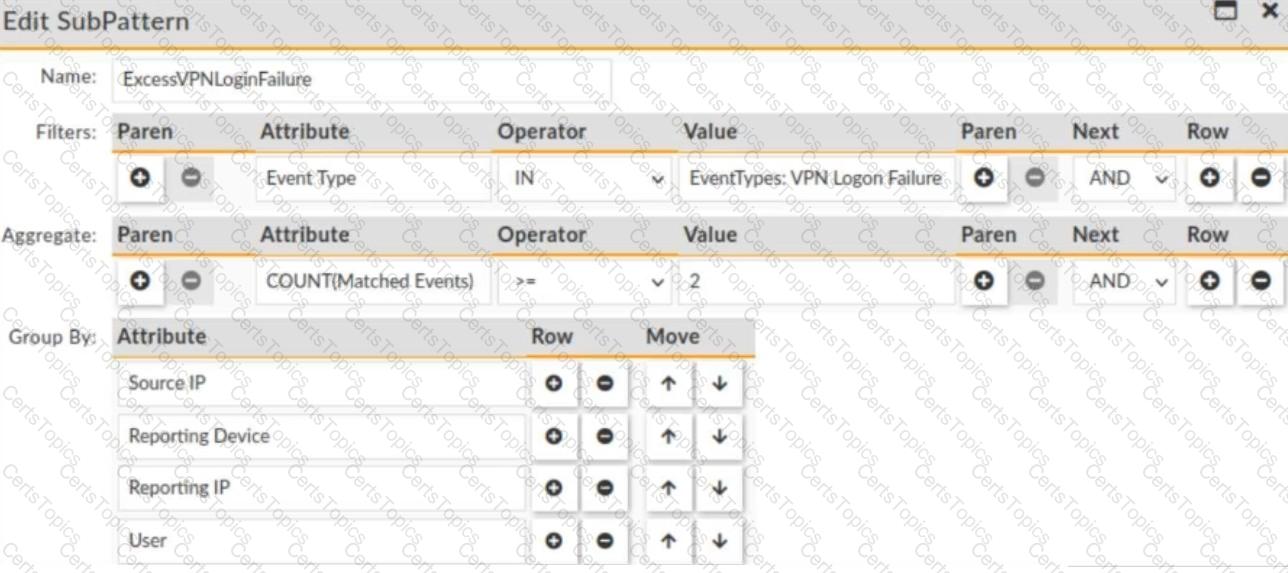
The rule evaluates multiple VPN logon failures within a ten-minute window. Consider the following VPN failure events received within a ten-minute window:
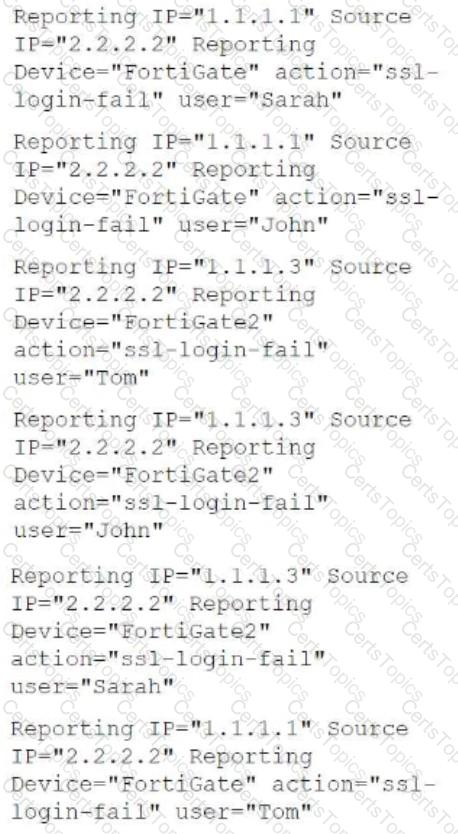
How many incidents are generated?
Refer to the exhibit.
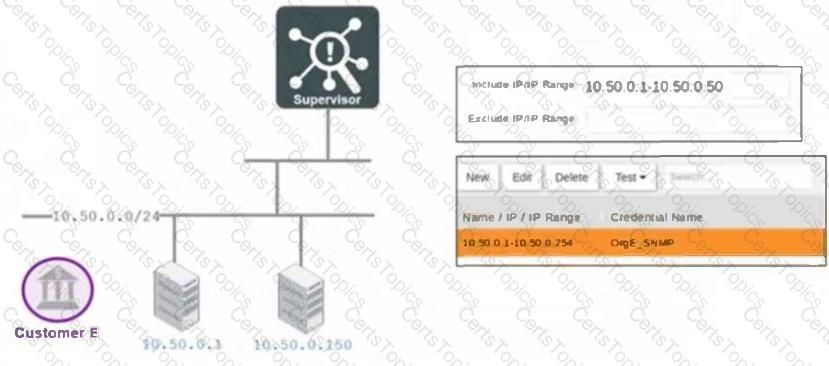
Which devices will be added to the CMDB and mapped to Customer E?
In a customer network that includes a collector, which device performs device discoveries?
Why do collectors communicate with the Supervisor after registration? (Choose two.)
Refer to the exhibit.
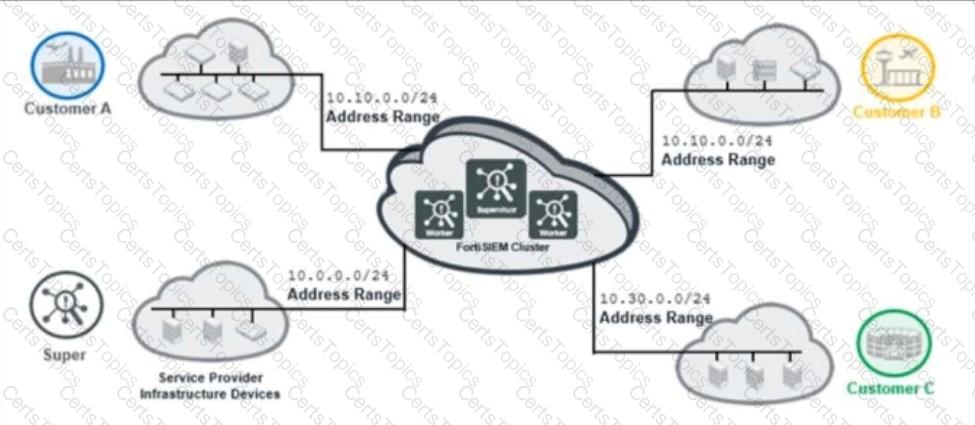
The service provider deployed FortiSIEM without a collector and added three customers on the supervisor.
What mistake did the administrator make?
Refer to the exhibit.
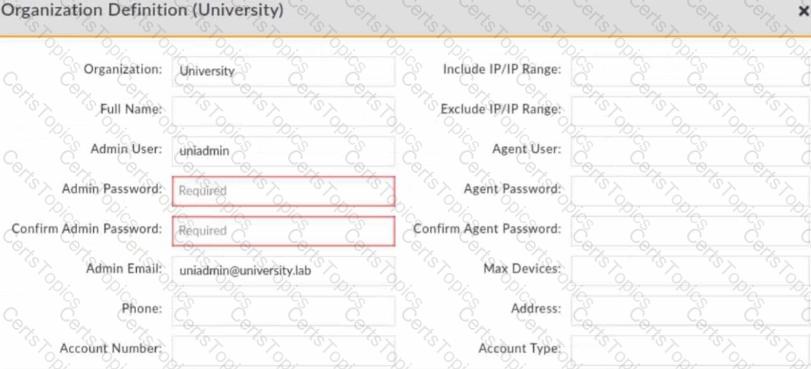
Which three fields from the organization destination are required while registering a collector? (Choose three.)
Refer to the exhibit.
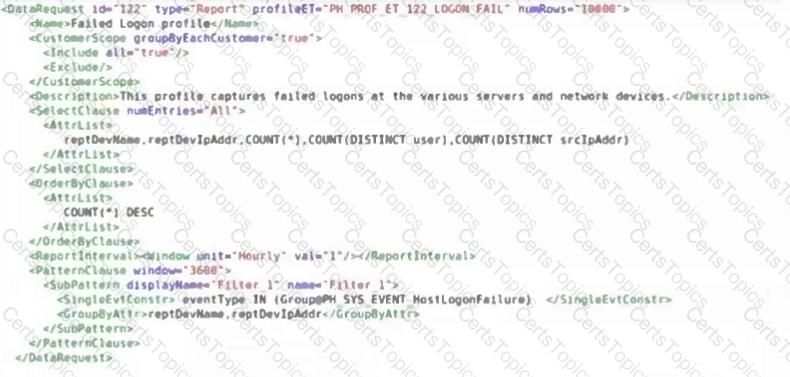
This is an example of a baseline profile that is configured in the backend of FortiSIEM.
Which two Group By attributes are configured for this profile? (Choose two.)
Which three processes are collector processes? (Choose three.)
Which two statements about the maximum device limit on FortiSIEM are true? (Choose two.)