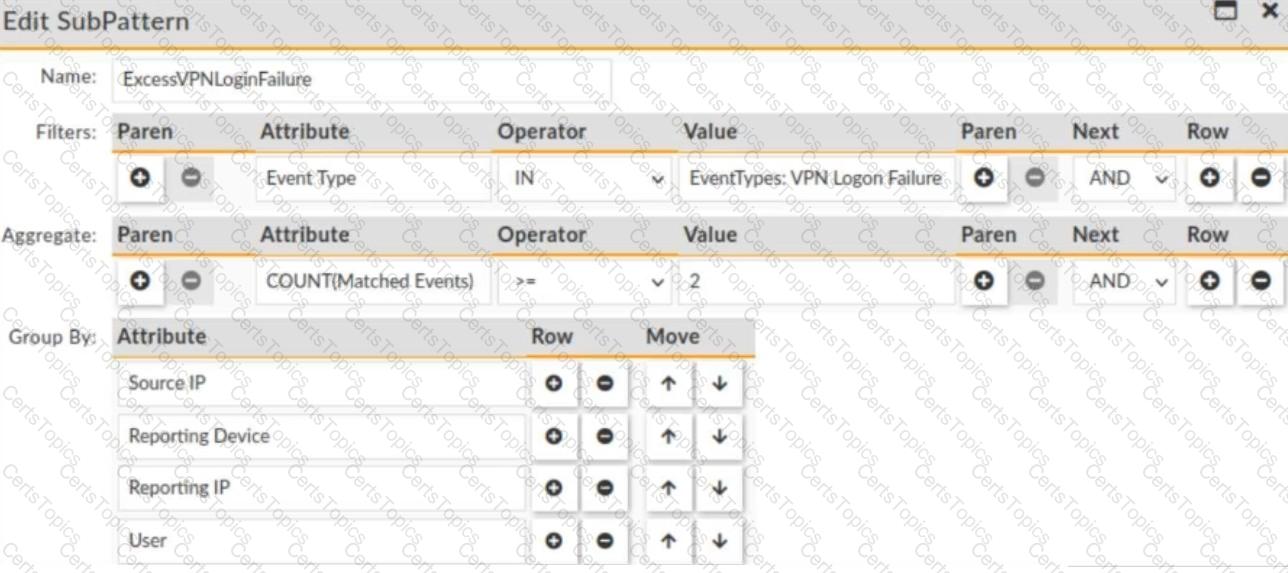
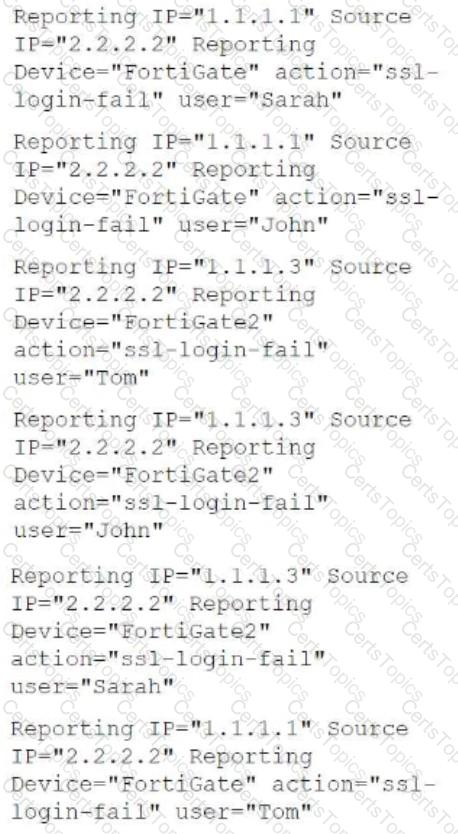
The rule triggers an incident when there are two or more VPN logon failures within a 10-minute window, grouped by Source IP, Reporting Device, Reporting IP, and User. Let's analyze the events:
Breakdown of Events:
1. Reporting IP: 1.1.1.1, Source IP: 2.2.2.2, Device: FortiGate, User: Sarah
2. Reporting IP: 1.1.1.1, Source IP: 2.2.2.2, Device: FortiGate, User: John
3. Reporting IP: 1.1.1.3, Source IP: 2.2.2.2, Device: FortiGate2, User: Tom
4. Reporting IP: 1.1.1.3, Source IP: 2.2.2.2, Device: FortiGate2, User: John
5. Reporting IP: 1.1.1.3, Source IP: 2.2.2.2, Device: FortiGate2, User: Sarah
6. Reporting IP: 1.1.1.1, Source IP: 2.2.2.2, Device: FortiGate, User: Tom
Now, applying the grouping criteria (Source IP, Reporting Device, Reporting IP, and User):
● Group 1: (1.1.1.1, 2.2.2.2, FortiGate, John) → 1 occurrence (not enough)
● Group 2: (1.1.1.1, 2.2.2.2, FortiGate, Sarah) → 1 occurrence (not enough)
● Group 3: (1.1.1.1, 2.2.2.2, FortiGate, Tom) → 2 occurrences (incident triggered)
● Group 4: (1.1.1.3, 2.2.2.2, FortiGate2, John) → 2 occurrences (incident triggered)
● Group 5: (1.1.1.3, 2.2.2.2, FortiGate2, Sarah) → 1 occurrence (not enough)
● Group 6: (1.1.1.3, 2.2.2.2, FortiGate2, Tom) → 1 occurrence (not enough)
Final Incident Count:
● One incident for Group 3 (Tom on FortiGate)
● One incident for Group 4 (John on FortiGate2)