Refer to the exhibits.
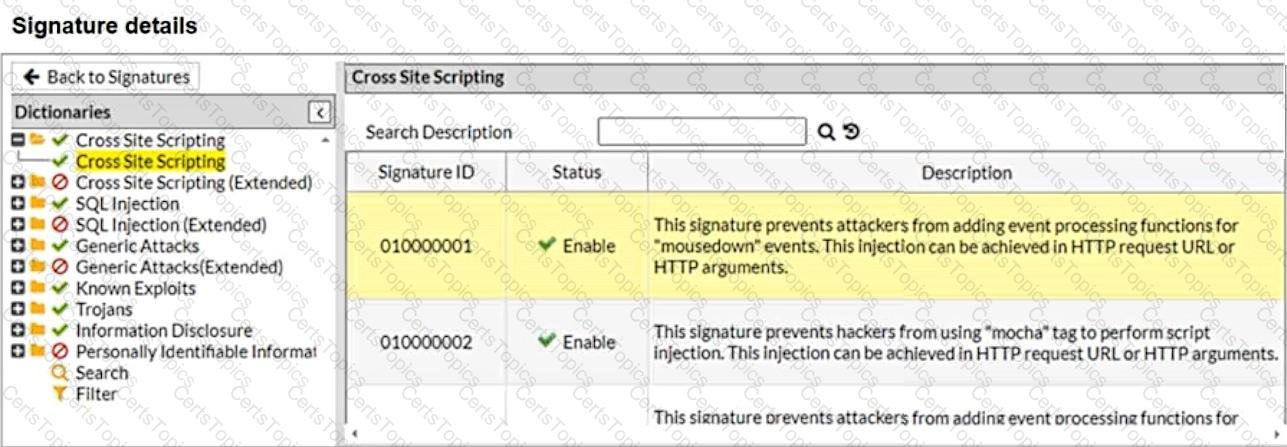
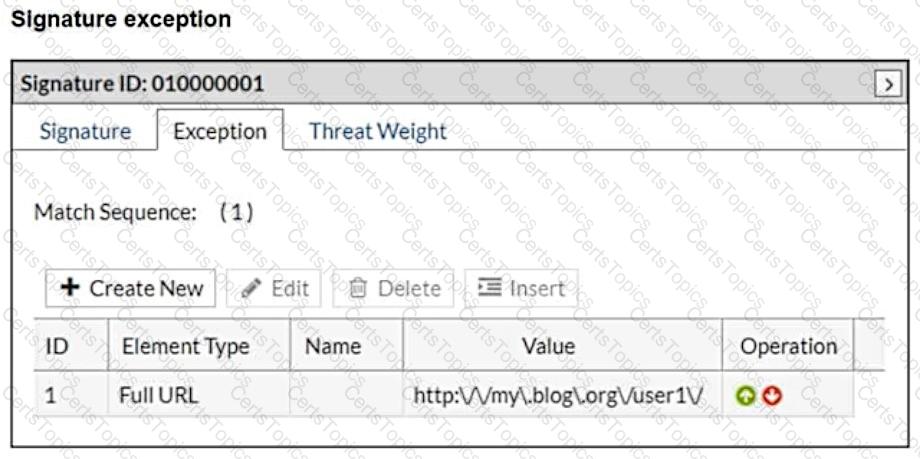
What will happen when a client attempts a mousedown cross-site scripting (XSS) attack against the site and FortiWeb is enforcing the highlighted signature?
Refer to the exhibit.
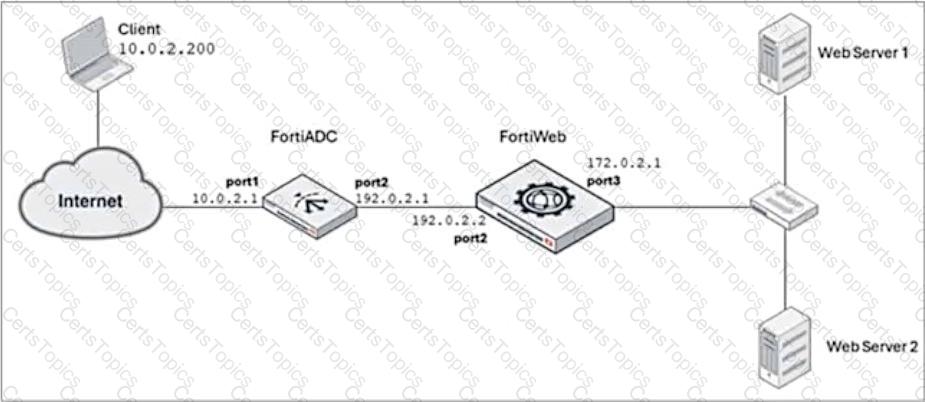
FortiADC is applying SNAT to all inbound traffic going to the servers.
When an attack occurs, FortiWeb blocks traffic based on the192.0.2.1source IP address, which belongs to FortiADC. This setup is breaking all connectivity and genuine clients are not able to access the servers.
What can the administrator do to avoid this problem? (Choose two.)
A customer wants to be able to index your websites for search and advertisement purposes.
What is the easiest way to allow this on a FortiWeb?
Which Layer 7 routing method does FortiWeb support?
Refer to the exhibit.
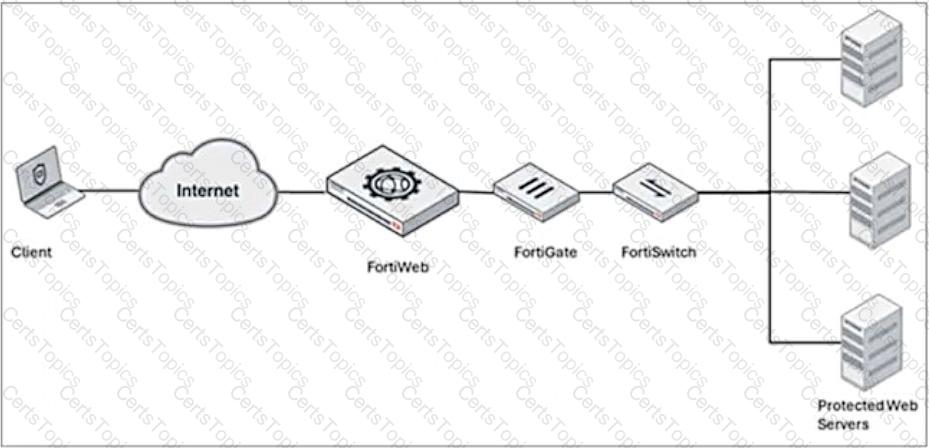
A FortiWeb device is deployed upstream of a device performing source network address translation (SNAT) or load balancing.
What configuration must you perform on FortiWeb to preserve the original IP address of the client?
What is the difference between an API gateway protection schema and a machine learning (ML) API protection schema?
In SAML deployments, which server contains user authentication credentials (username/password)?
When is it possible to use a self-signed certificate, rather than one purchased from a commercial certificate authority?
Refer to the exhibit.
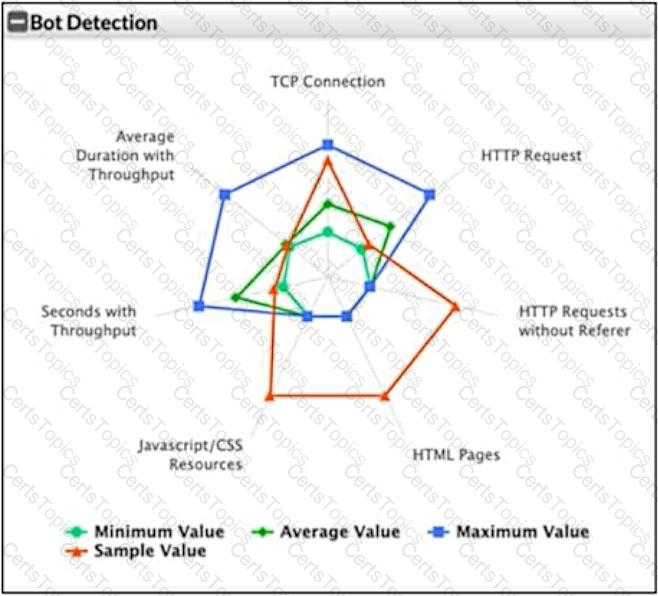
What can you conclude from this support vector machine (SVM) plot of a potential bot connection?