An administrator configured a FortiGate to act as a collector for agentless polling mode.
What must the administrator add to the FortiGate device to retrieve AD user group information?
Which statement is correct regarding the use of application control for inspecting web applications?
Refer to the exhibits, which show the system performance output and the default configuration of high memory usage thresholds in a FortiGate.
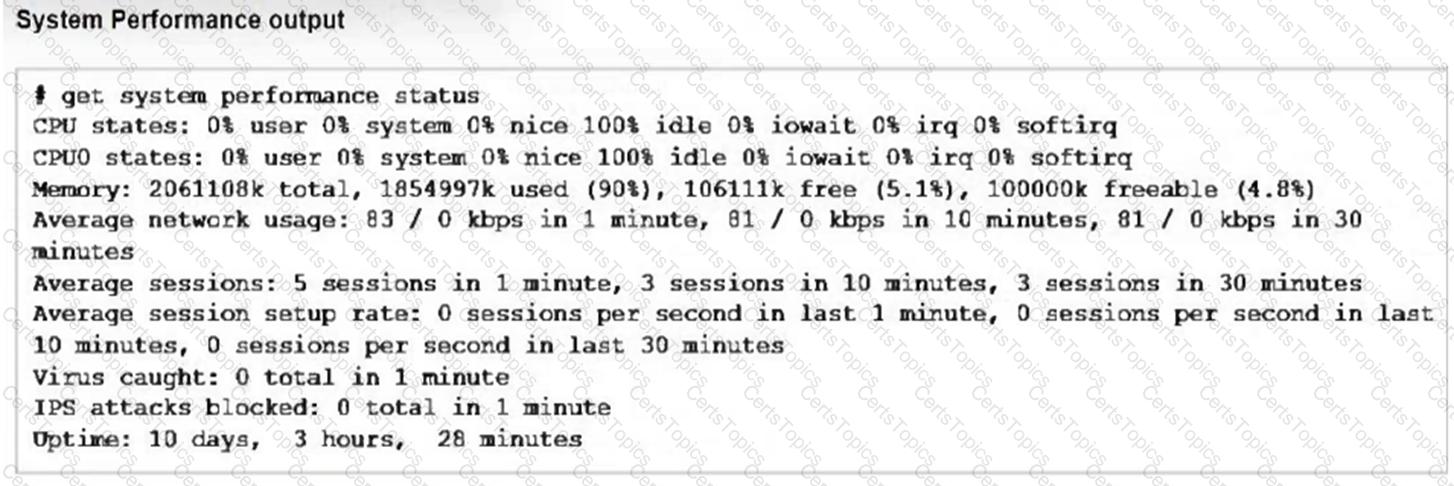
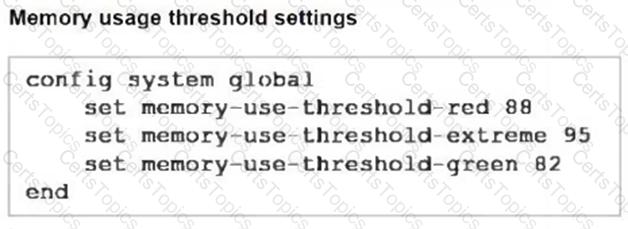
Based on the system performance output, what can be the two possible outcomes? (Choose two.)
Refer to the exhibit showing a debug flow output.
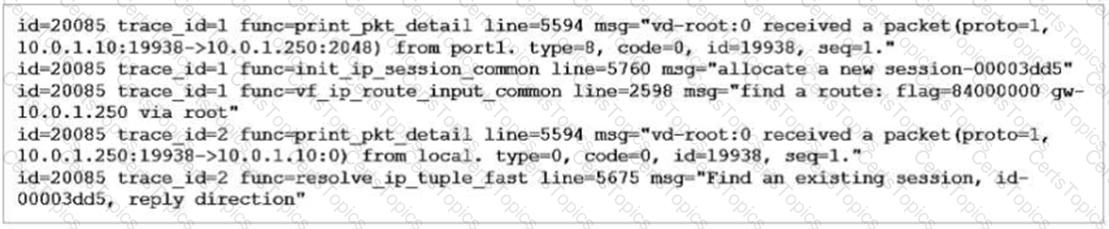
What two conclusions can you make from the debug flow output? (Choose two.)
Which two features of IPsec IKEv1 authentication are supported by FortiGate? (Choose two.)
What are three key routing principles in SD-WAN? (Choose three.)
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.
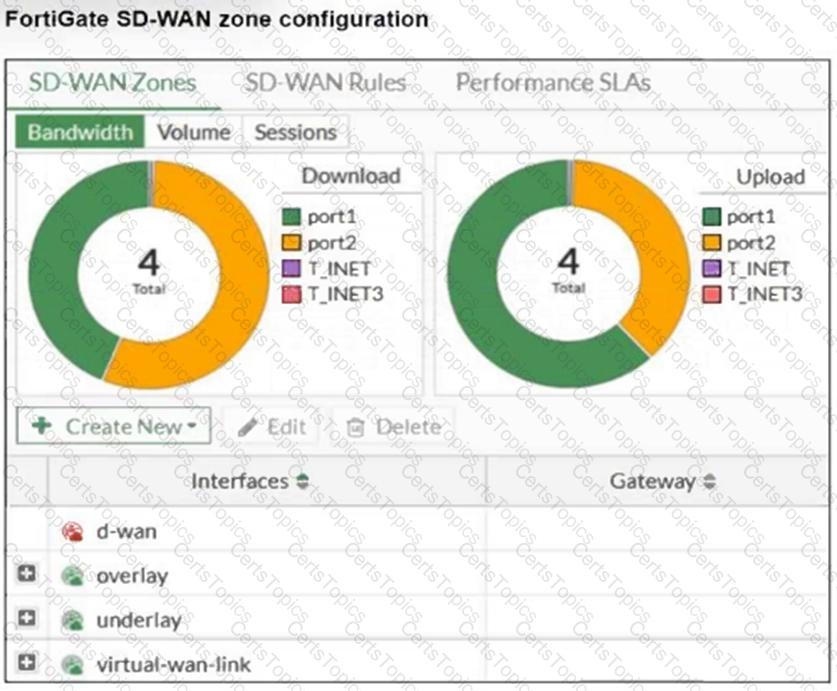
Based on the exhibit, which statement is true?
There are multiple dial-up IPsec VPNs configured in aggressive mode on the HQ FortiGate. The requirement is to connect dial-up users to their respective department VPN tunnels.
Which phase 1 setting you can configure to match the user to the tunnel?
Refer to the exhibit, which shows the IPS sensor configuration.
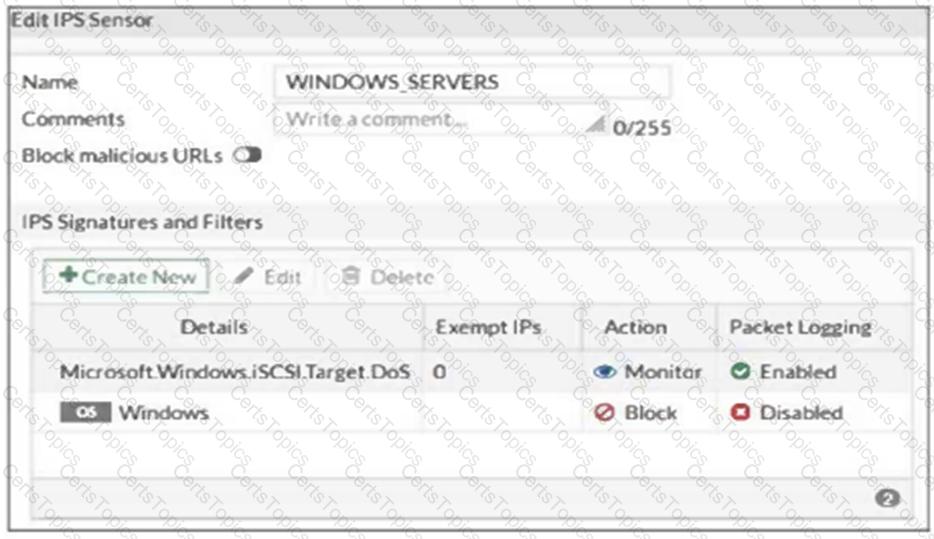
If traffic matches this IPS sensor, which two actions is the sensor expected to take? (Choose two.)
Refer to the exhibit.
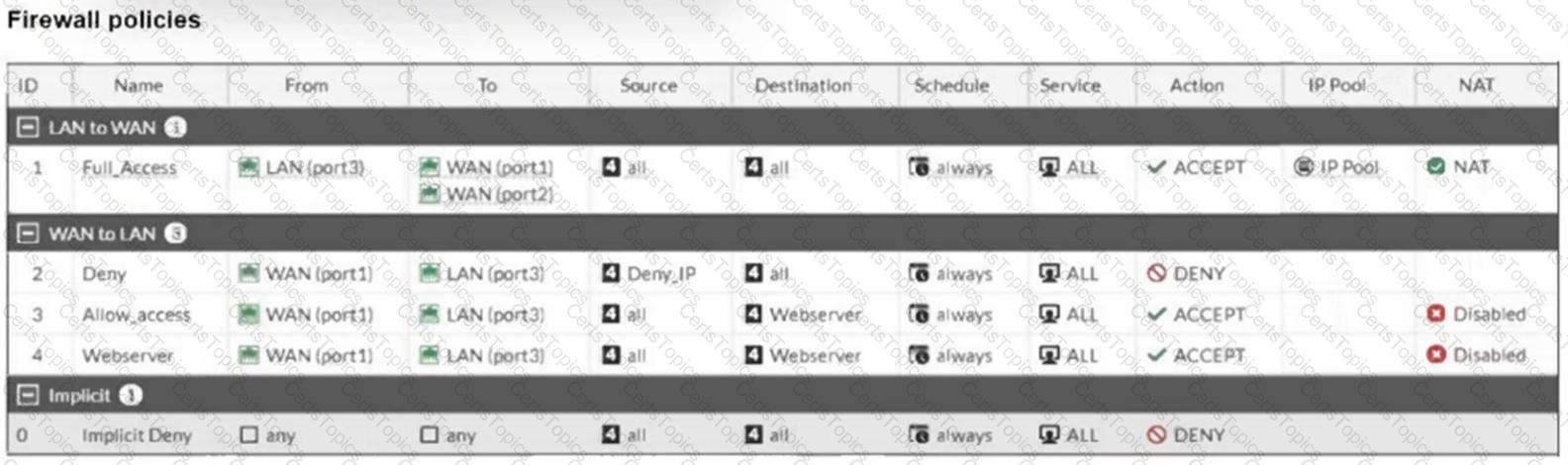
Which statement about this firewall policy list is true?
Refer to the exhibits.
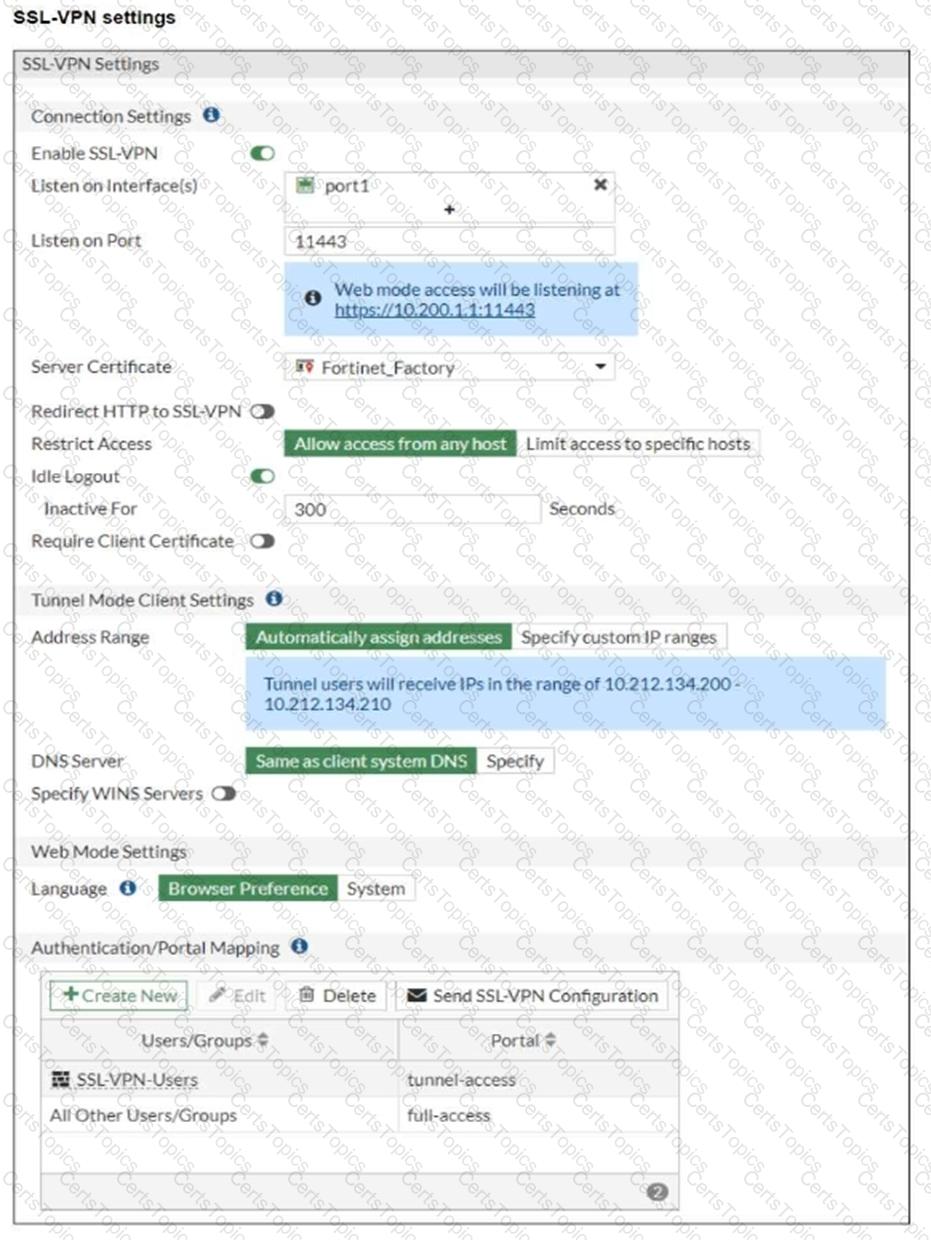
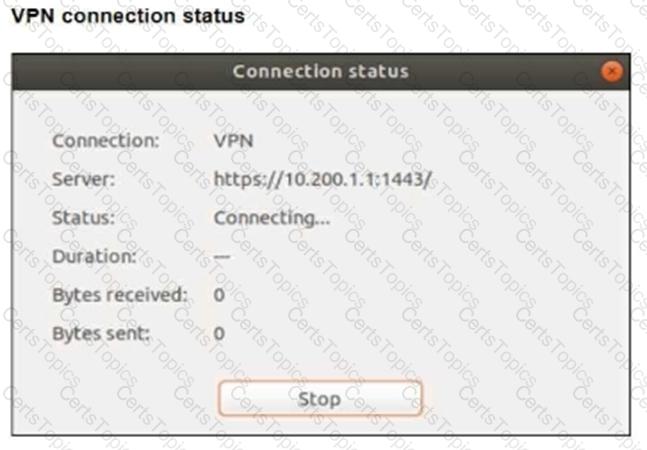
The SSL VPN connection fails when a user attempts to connect to it.
What should the user do to successfully connect to the SSL VPN?
Which two statements are true regarding FortiGate HA configuration synchronization? (Choose two.)
Which three strategies are valid SD-WAN rule strategies for member selection? (Choose three.)
Refer to the exhibits.
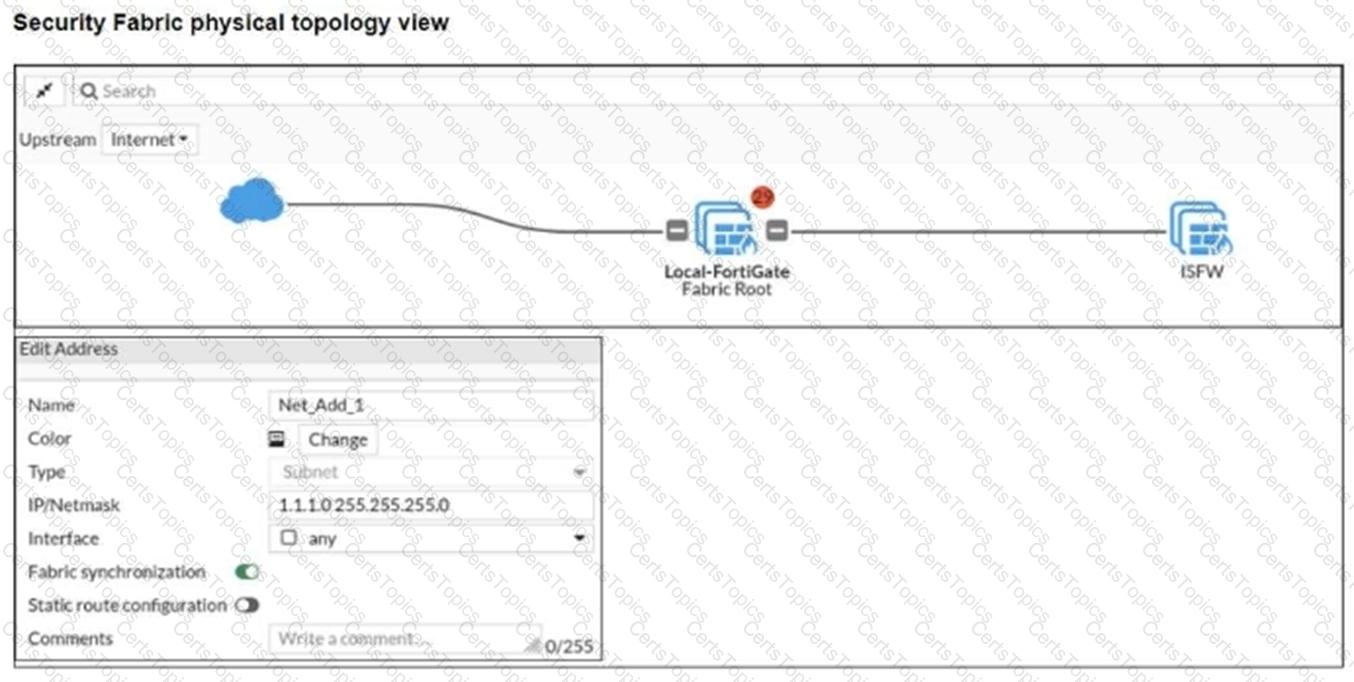
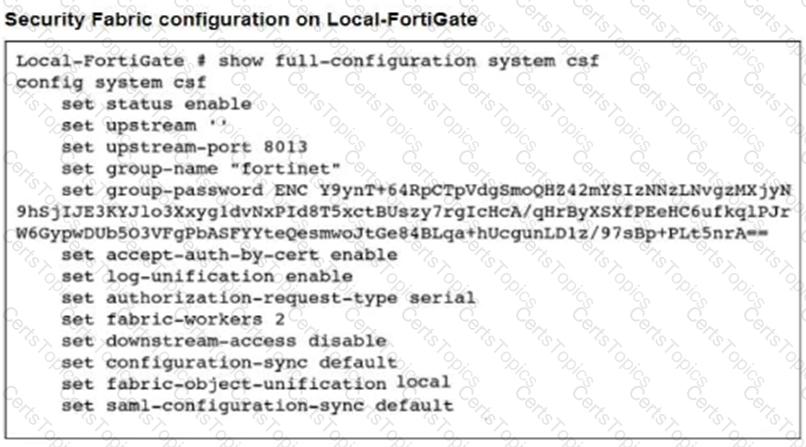
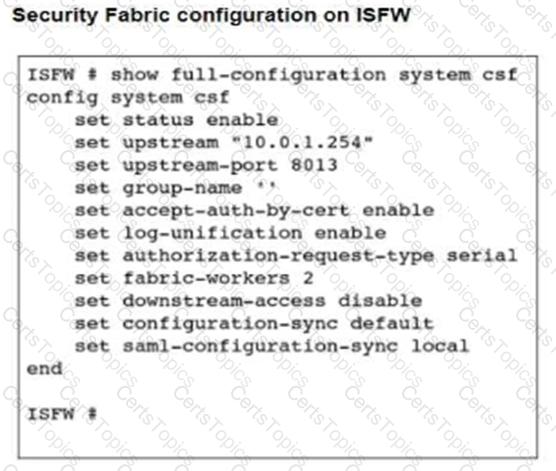
An administrator creates a new address object on the root FortiGate (Local-FortiGate) in the security fabric. After synchronization, this object is not available on the downstream FortiGate (ISFW).
What must the administrator do to synchronize the address object?
FortiGate is operating in NAT mode and has two physical interfaces connected to the LAN and DMZ networks respectively.
Which two statements are true about the requirements of connected physical interfaces on FortiGate? (Choose two.)
Which two statements are correct when FortiGate enters conserve mode? (Choose two.)
Which engine handles application control traffic on the next-generation firewall (NGFW) FortiGate?
Refer to the exhibits.
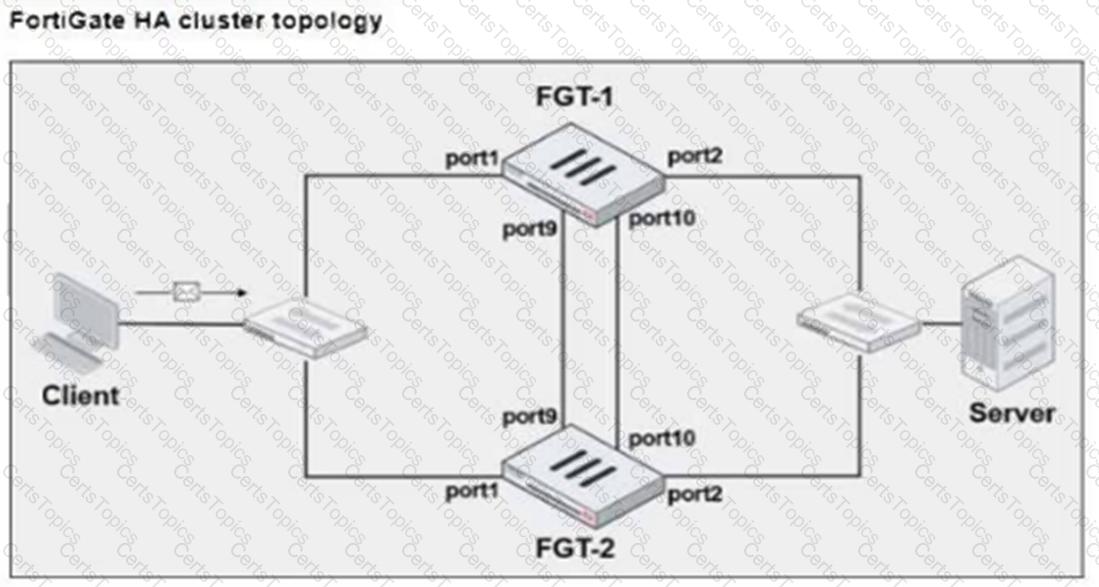
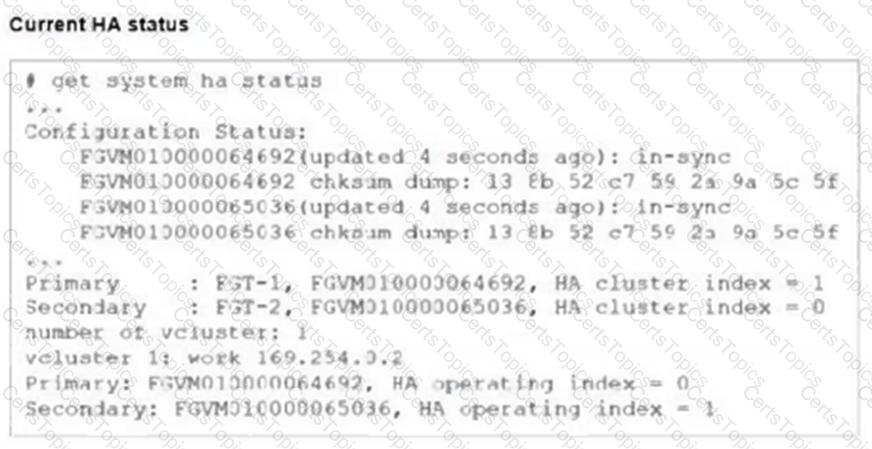
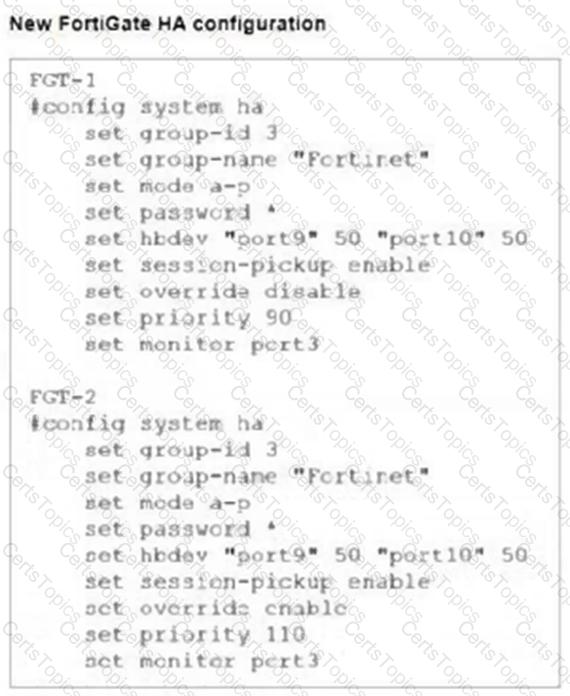
FGT-1 and FGT-2 are updated with HA configuration commands shown in the exhibit.
What would be the expected outcome in the HA cluster?
Which method allows management access to the FortiGate CLI without network connectivity?
An administrator is configuring an IPsec VPN between site A and site В. The Remote Gateway setting in both sites has been configured as Static IP Address.
For site A, the local quick mode selector is 192.168.1.0/24 and the remote quick mode selector is 192.168.2.0/24.
Which subnet must the administrator configure for the local quick mode selector for site B?
Which three statements about SD-WAN zones are true? (Choose three.)
Which two statements are true about the FGCP protocol? (Choose two.)
Refer to the exhibit.
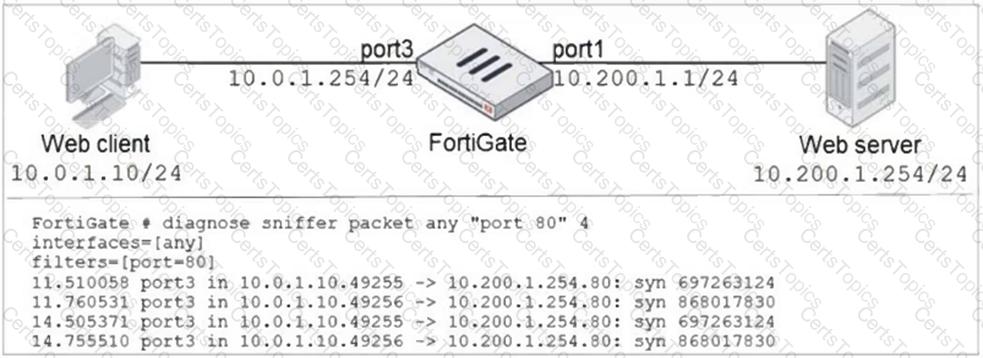
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
What should the administrator do next, to troubleshoot the problem?
Refer to the exhibit.
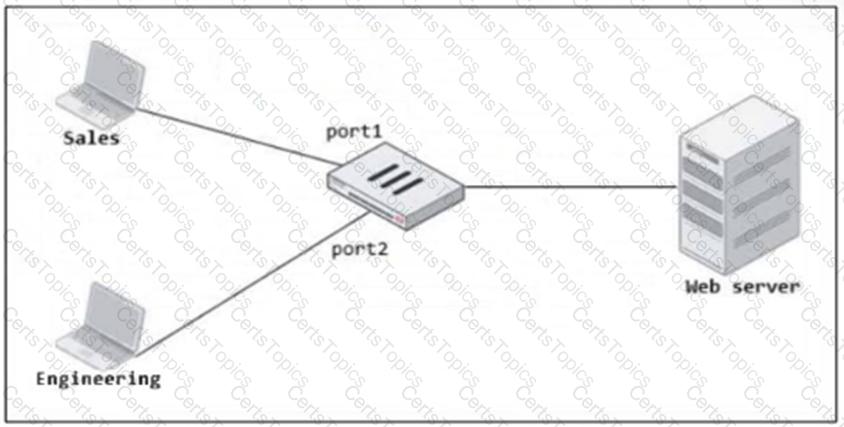
FortiGate has two separate firewall policies for Sales and Engineering to access the same web server with the same security profiles.
Which action must the administrator perform to consolidate the two policies into one?
An administrator wants to configure dead peer detection (DPD) on IPsec VPN for detecting dead tunnels. The requirement is that FortiGate sends DPD probes only when there is outbound traffic but no response from the peer.
Which DPD mode on FortiGate meets this requirement?
Refer to the exhibit.
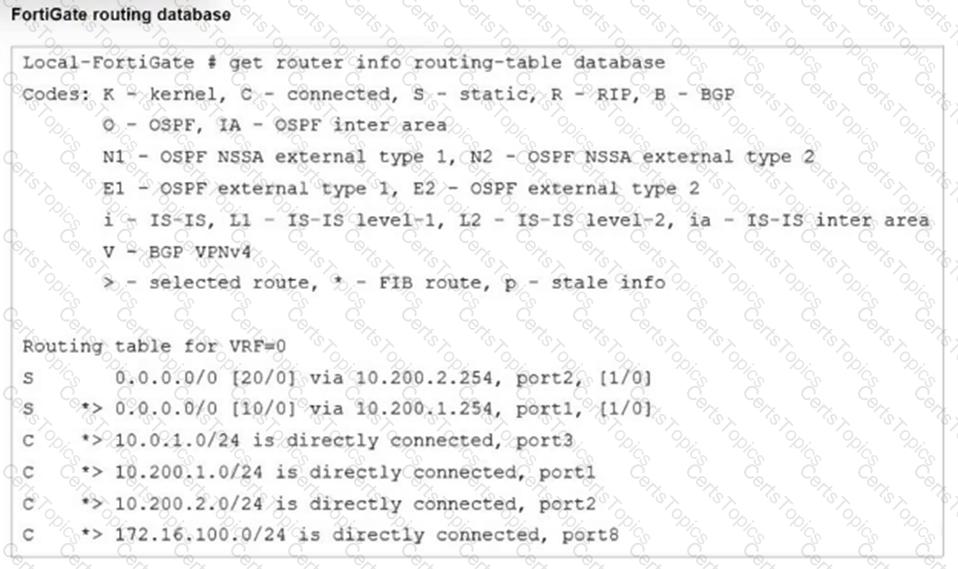
Which two statements are true about the routing entries in this database table? (Choose two.)