Which three statements about SD-WAN zones are true? (Choose three.)
Which two statements are true about the FGCP protocol? (Choose two.)
Refer to the exhibit.
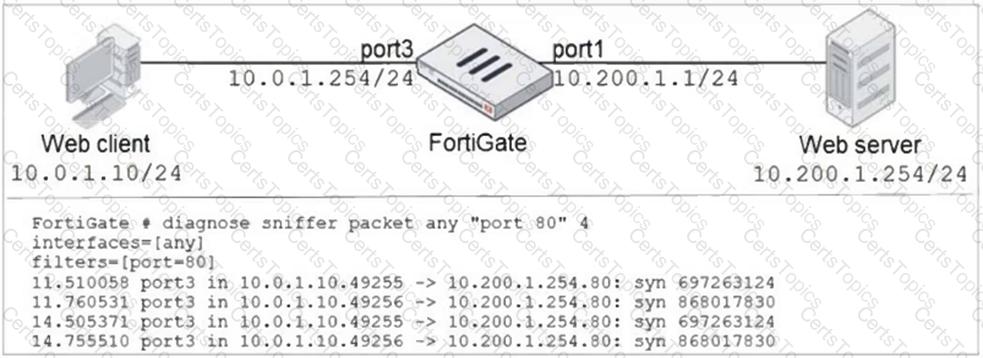
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
What should the administrator do next, to troubleshoot the problem?
Refer to the exhibit.
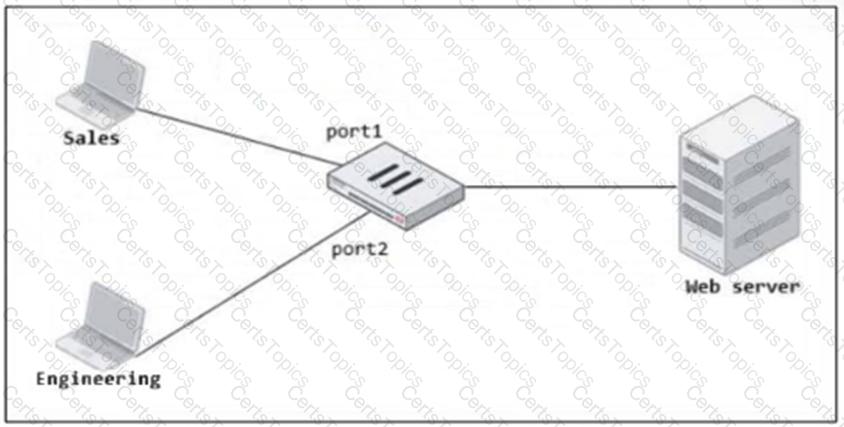
FortiGate has two separate firewall policies for Sales and Engineering to access the same web server with the same security profiles.
Which action must the administrator perform to consolidate the two policies into one?