How is internet access provided to a WAN edge router that is connected to a MPLS transport link?
A customer requires QoS to support multimedia conferencing over MPLS. The network architect chooses to use per-hop behavior. Which solution must the architect use to classify and mark traffic traveling between branch sites?
An architect is designing a network for an enterprise site. The design must use an active/backup design for the WAN. It must guarantee the SLA for several applications regardless of which connection is used. Which deployment model should the architect choose?
A customer plans to deploy WoL in the enterprise with these high-level design requirements:
Which two solutions must the customer select to have a successful deployment? (Choose two.) 3 A. IP directed broadcast and forward-protocol must be enabled on all the SVI or routed interlaces where the client subnets reside.
B. IP helper-addresses for the client ranges must be enabled on the SVI or routed interface where the WoL server subnet resides.
C. IP helper-addresses for the client ranges must be disabled on the SVI or routed interface where the WoL server subnet resides
D. IP helper-addresses for the WoL server must be enabled on the SVI or routed interface where the client subnets reside
E. IP directed broadcast and forward-protocol must be disabled on all the SVI or routed interfaces where the client subnets reside.
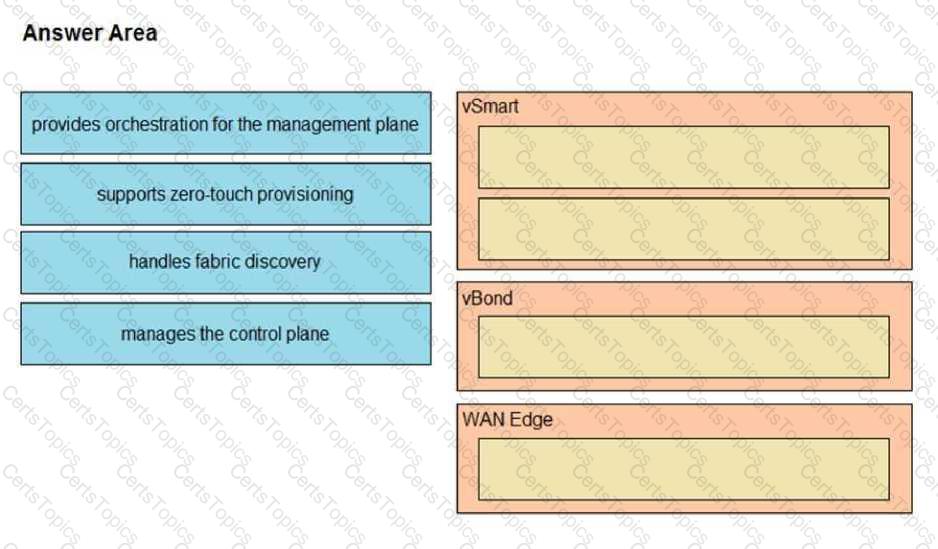
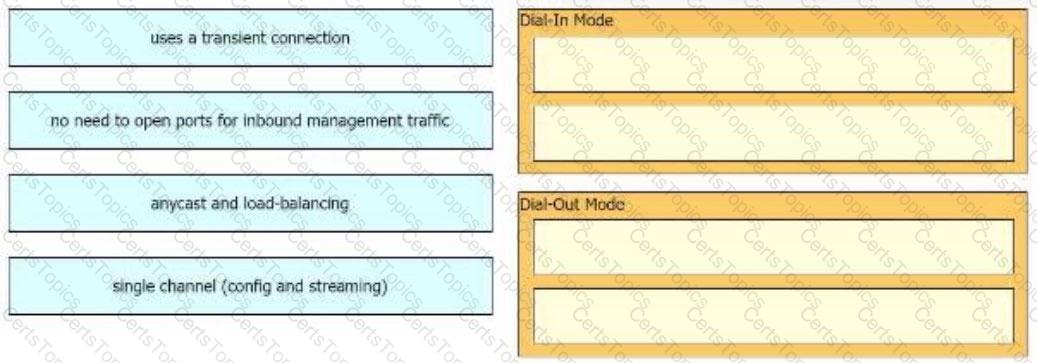
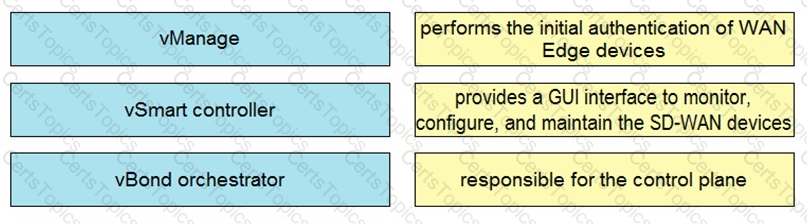
Drag and drop the properties from the left onto the Cisco SD-WAN components that perform them on the right.
An architect must design a QoS model for a business-critical application that Is delay-sensitive and requires high bandwidth. The company's head office hosts the application, and DMVPN tunnels protected with IPsec provide connectivity between the head office and branches. Which solution must the architect choose?

Refer to the exhibit. Customers report low video quality and delays when having point-to-point telepresence video calls between the two locations. An architect must optimize a design so that traffic follows the same path for egress and ingress traffic flows. Which technique optimizes the design?
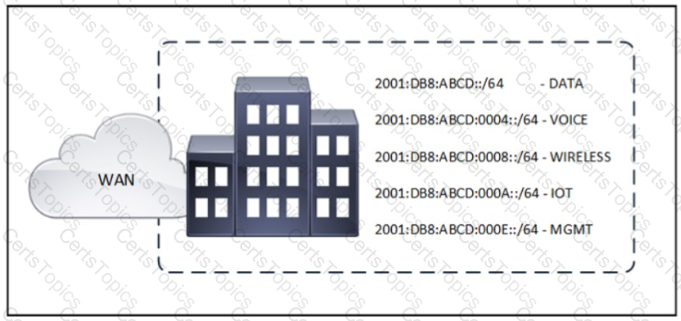
Refer to the exhibit A network administrator plans to announce the site subnets to the WAN using route summarization instead of announcing every subnet. What is the smallest summary route that should be used to encompass all subnets at the site?
Which design consideration must be made when using IPv6 overlay tunnels?
Which two statements about VRRP advertisements are true? (Choose two.)
Which design consideration must be made when dual WAN Edge routers are deployed at a branch site?
An engineer is designing a BGP solution supporting a VXLAN environment over a Layer 3 IPv4 network fabric with these requirements
provide Layer 2 adjacency
allow VM migration of workloads between sites
IGP is OSPF
Which BGP address family must the engineer choose?
A)

B)

C)

D)

Which two considerations must be made regarding the overlay network for a Cisco SD-Access architecture? (Choose two.)
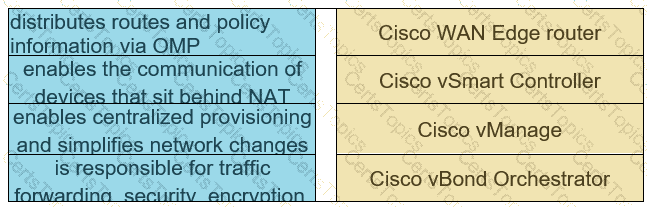
Drag and drop the descriptions from the left onto the Cisco SD-WAN component they describe on the right.
Refer to the exhibit. A network architect is preparing a network design based on the EIGRR Routers are connected using a cat6a cable type and the inter-router connection speed is limited to 10 Mbps due to distance. During the pilot phase, a DUAL-3-SIA error message is visible. Which action must the engineer take to create a stable design?
Which nonproprietary mechanism can be used to automate rendezvous point distribution in a large PIM domain?
What are two benefits of designing an SD-WAN network fabric with direct Internet access implemented at
every site? (Choose two.)
When a network is designed using IS-IS protocol, which two circuit types are supported? (Choose two.)
Prior to establishing full-mesh iPsec tunnels in a typical Cisco SD-WAN deployment, which mechanism do WAN Edge routers use to exchange Key information for data plane encryption?
A customer is discussing QoS requirements with a network consultant. The customer has specified that end-to-end path verification is a requirement. Which QoS solution meets this requirement?
Exhibit:
An architect must design an IPv6 migration solution for a corporation with remote offices to support:
* The customer has IPv4 peering with their service provider.
* IPv6 users need access to IPv4 and IPv6 resources.
* Existing content providers will migrate to IPv6 in the next two years.
* Users will be migrated in a phase-by-phase approach.
Which migration solution must the architect choose?
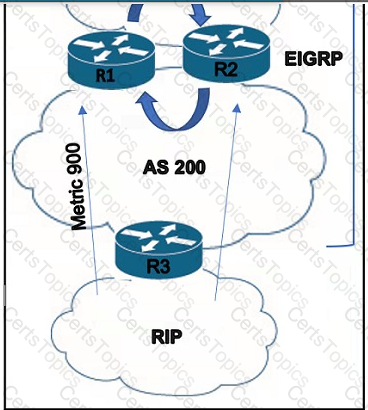
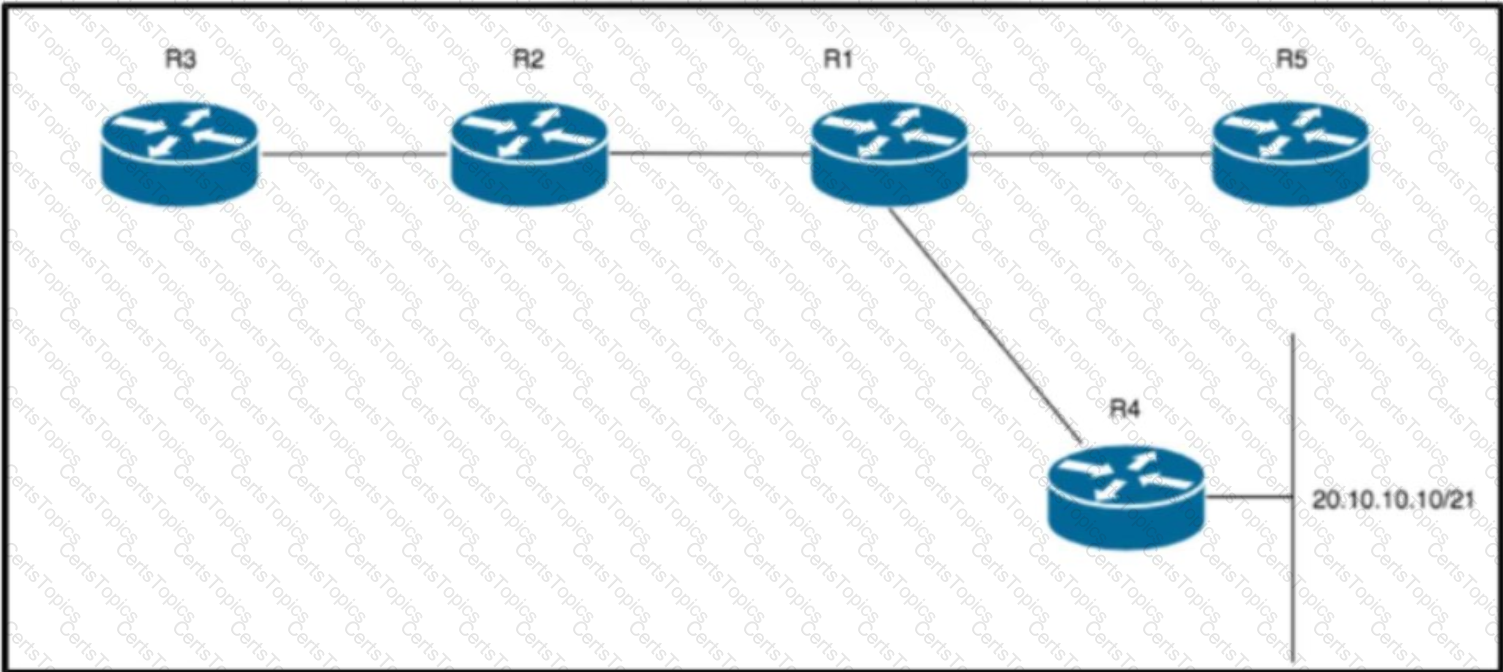
Refer to the exhibit. An architect must design a solution to connect the network behind R3 with the EIGRP network. Which mechanism should be included to avoid routing loops?
An engineer must design an in-band management solution for a customer with branch sites. The solution must allow remote management of the branch sites using management protocols over an MPLS WAN. Queueing is implemented at the remote sites using these classes:

How must the solution prioritize the management traffic over the WAN?
A network administrator is troubleshooting a DMVPN setup between the hub and the spoke. Which action should the administrator take before troubleshooting the IPsec configuration?
Drag and drop the elements from the left onto the YANG models where they and used on the right.
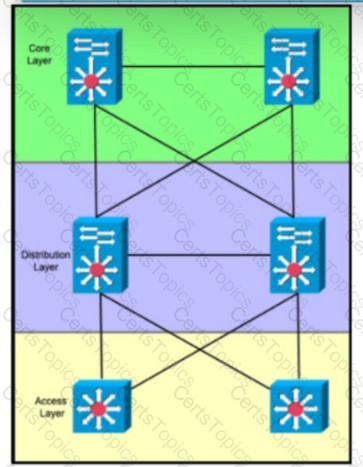
Refer to the exhibit. An engineer Is designing a multicampus Layer 3 Infrastructure using EIGRP as the routing protocol. The design must provide quick replies to queries In the event of a downlink, prevent unnecessary queries, and ensure that traffic does not unnecessarily transit the access layer. Which two actions must the engineer take for the network design? (Choose two.)
An engineer is designing a network for a customer running a wireless network with a common VLAN for all APs. The customer is experiencing unicast flooding in the Layer 2 network between the aggregation and access layers. The customer wants to reduce the flooding and improve convergence time. Which solution meets these requirements?
An enterprise customer has these requirements:
end-to-end QoS for the business-critical applications and VoIP services based on CoS marking.
flexibility to offer services such as IPv6 and multicast without any reliance on the service provider.
support for full-mesh connectivity at Layer 2.
Which WAN connectivity option meets these requirements?
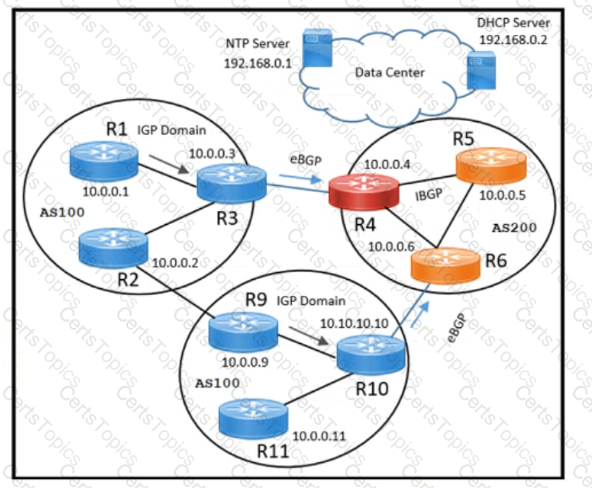
Refer to the exhibit. A network engineer working for a private service provider with an employee ID: 4670:71:451 must design a BGP solution based on:
All traffic originating from AS100 must pass through AS200 to reach the NTP and DHCP server
When a link failure occurs between R3 and R4, traffic must follow the R2-R9 link to reach the NTP and DHCP server.
Which solution must the design include?
How do endpoints inside an SD-Access network reach resources outside the fabric?
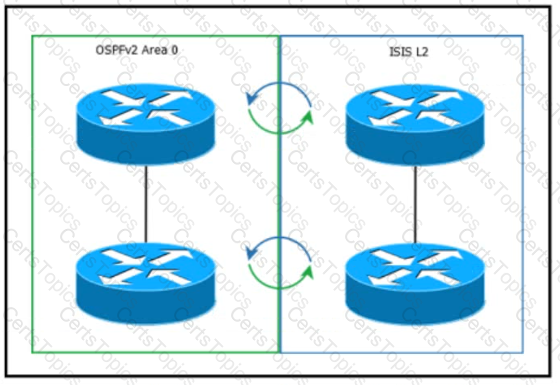
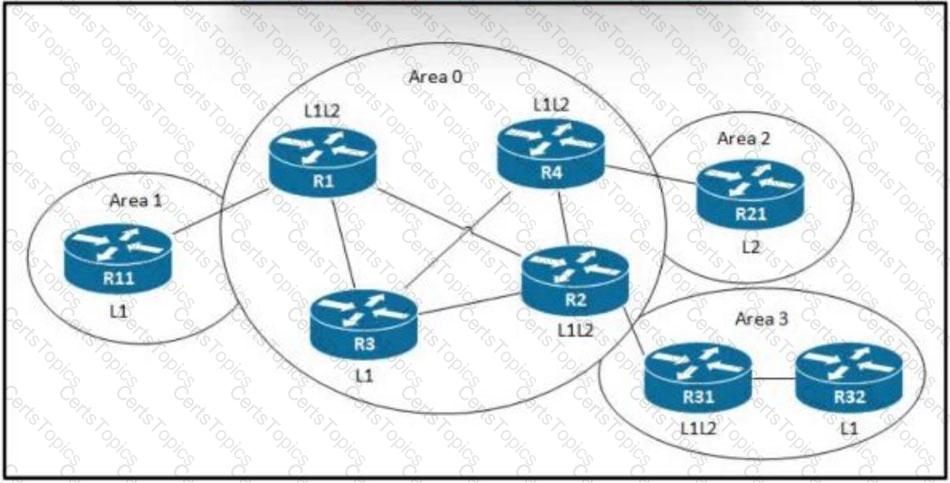
Refer to the exhibit. An architect is designing a network that requires route redistribution. The design must prevent route feedback and the creation of routing loops. The OSPF domain is using default metrics, and the IS-IS domain is using narrow metrics. Which solution must the architect select?
An engineer is designing a QoS solution for a customer The customer's internet connection has a bandwidth of 10 Mbps. The design must ensure that traffic bursts of data do not exceed the bandwidth of the connection and that received traffic does not starve out business-critical traffic Which solution must the engineer choose?
Which WAN connectivity technology is optimal for edge computing compared to others and why?
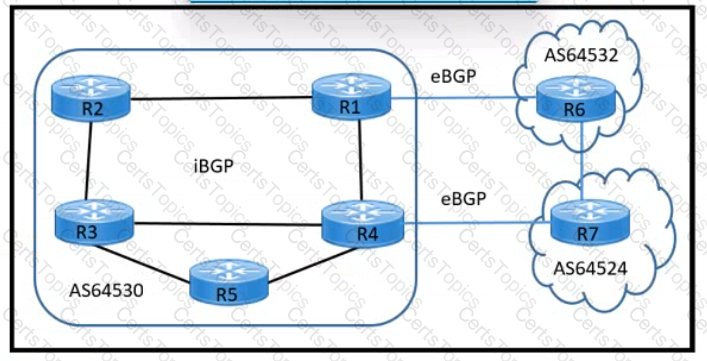
Refer to the exhibit. A network engineer must design a BGP solution based on:
The route reflector must have one or more direct physical connections to the core routers (R3 and R4).
The route reflector must have full redundancy and avoid a single point of failure.
R2 to R1 link utilization is 90%. and the remaining links are less than 50% utilized.
Which two solutions must the design Include? (Choose two.)
What is the main purpose of the Cisco SD-Access underlay design?

Refer to the exhibit. A Cisco Catalyst switch is configured to.. only one MAC address to be learned manually on interface gkjO/2. Which command must be run to dynamically learn the devices that are connected to the switch port?

A company's security policy requires that all connections between sites be encrypted in a manner that does not
require maintenance of permanent tunnels. The sites are connected through a private MPLS-based service that
uses a dynamically changing key and spoke-to-spoke communication. Which type of transport encryption must
be used in this environment?
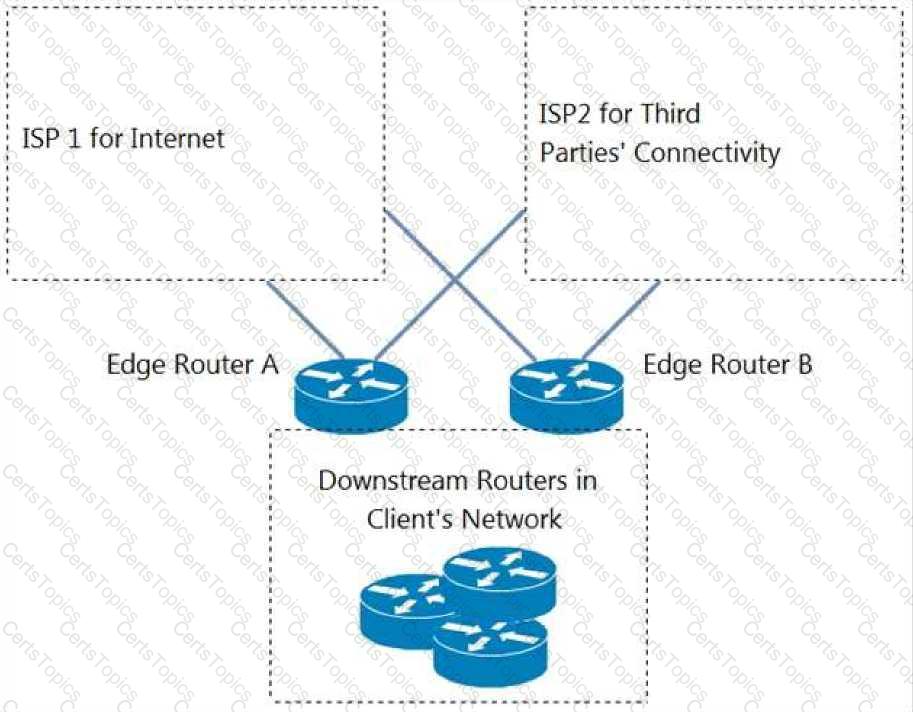
Refer to the exhibit. An engineer is designing a BGP solution for a client that peers with ISP1 for full Internet connectivity and with ISP2 for direct exchange of routes for several third parties. Which action, when implemented on the edge routers, enables the client network to reach the Internet through ISP1?
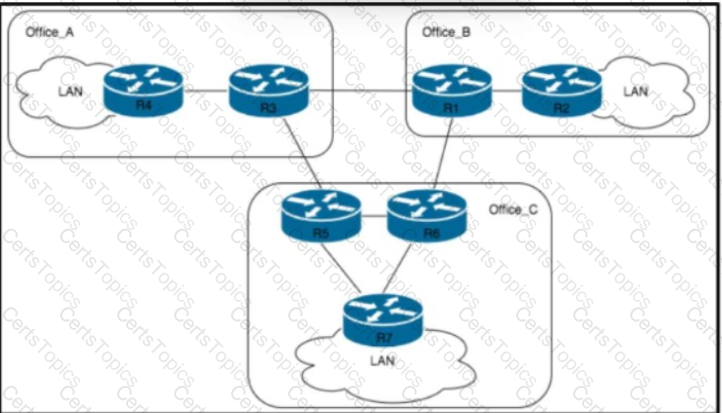
Refer to the exhibit. A company has some offices that are connected via dark fiber in New York. A network architect must optimize the network design based on the EIGRP routing protocol. The network has hierarchical addressing between 10 and 12 routers in each office. Routing convergence time must be at the minimum. What must the network architect do to reduce the query range?
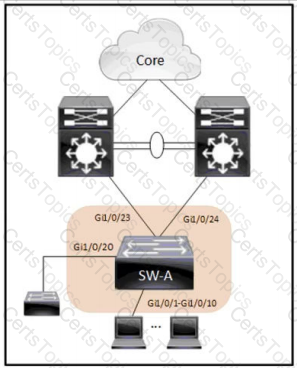
Refer to the exhibit. An architect reviews the low-level design of a company's enterprise network and advises optimizing the STP convergence time. Which functionality must be to Gi1/0/1-10 to follow the architect's recommendation?
In a Cisco SD-Access fabric, switch node Is equivalent to an access layer switch In a traditional three-tier campus network design?
What are two valid scaling techniques when an EIGRP network is designed that consists of more than 1000 routers? (Choose two.)
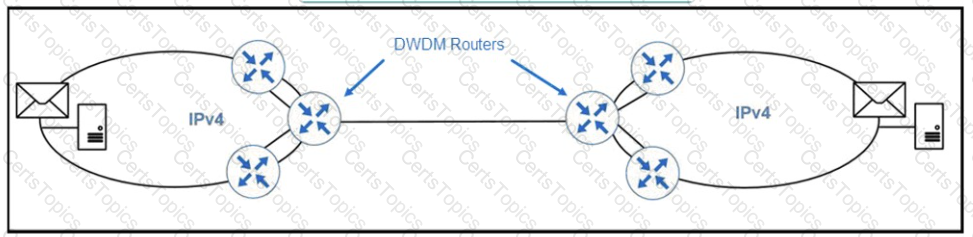
Refer to the exhibit. An engineer is planning an IPv4 to IPv6 migration solution for a customer. The routers in the network can support IPv4 and IPv6, except for the DWDM routers. The DWDM routers provide a Layer 2 link in which the routers peer directly with each other across a DWDM circuit. The circuit also provides connectivity between the mail servers. Which IPv6 migration technique must the engineer deploy?
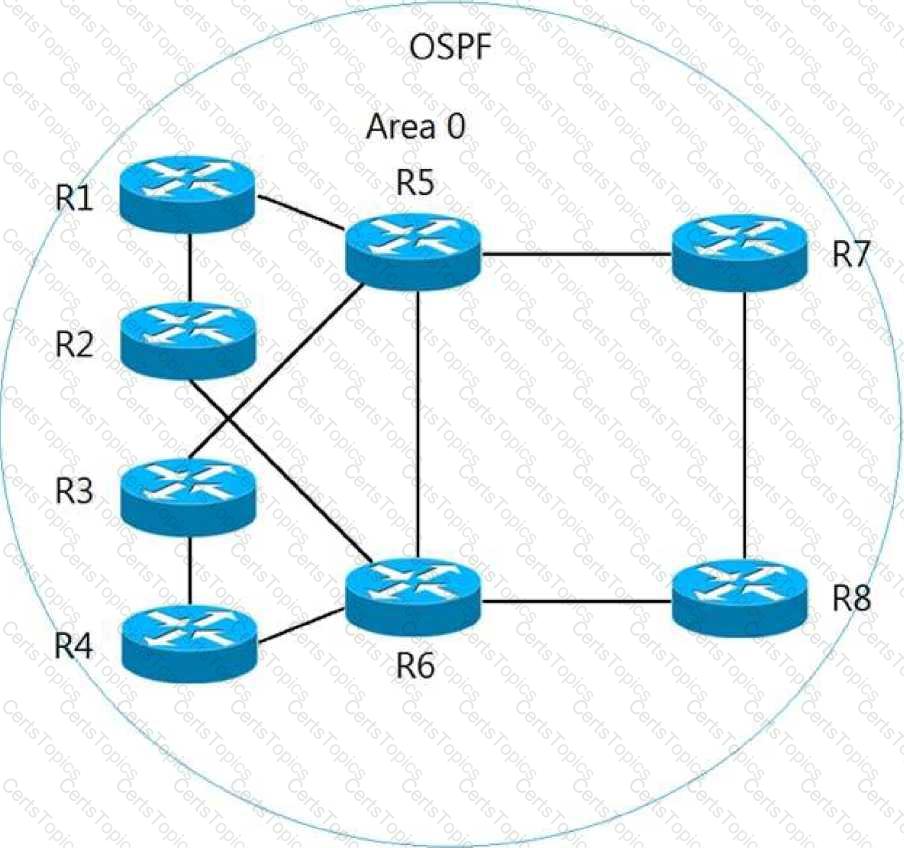
Refer to the exhibit. All routers currently reside in OSPF area 0. The network manager recently used R1 and R2 as aggregation routers for remote branch locations and R3 and R4 for aggregation routers for remote office locations. The network has since been suffering from outages, which are causing frequent SPF runs. To enhance stability and introduce areas to the OSPF network with the minimal number of ABRs possible, which two solutions should the network manager recommend? (Choose two.)
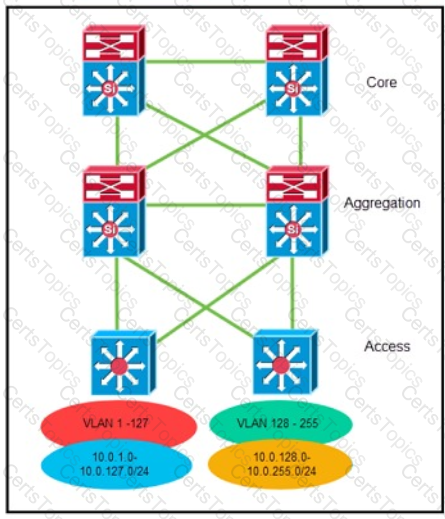
Refer to the exhibit. An architect is designing a Layer 3 campus network The design must hide network instability, reduce network overhead, and conserve critical device memory Which route summarization solution must the architect select?
An engineer must design a VPN solution for a company that has multiple branches connecting to a main office. What are two advantages of using DMVPN instead of IPsec tunnels to accomplish this task? (Choose
two.)
A company needs to increase access port capacity on one floor of a building. They want to leverage the existing catalyst access switch. There is no problem with uplink bandwidth capacity. However, no additional uplinks can be added because no ports are available on the distribution switches. Which solution must the company choose to provide additional access ports?
Which PIM mode uses a shared tree only?
Refer to the exhibit.
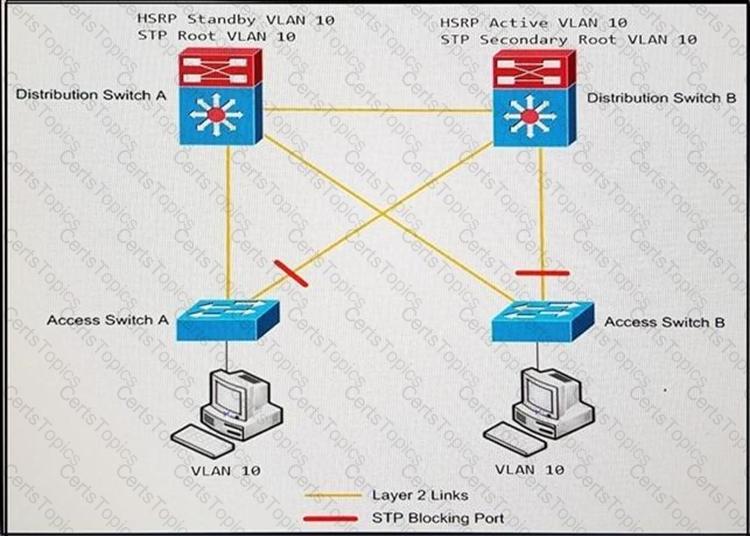
An engineer must optimize the traffic flow of the network. Which change provides a more
efficient design between the access and the distribution layer?
Which design element should an engineer consider when multicast is included in a Cisco SD-Access architecture?
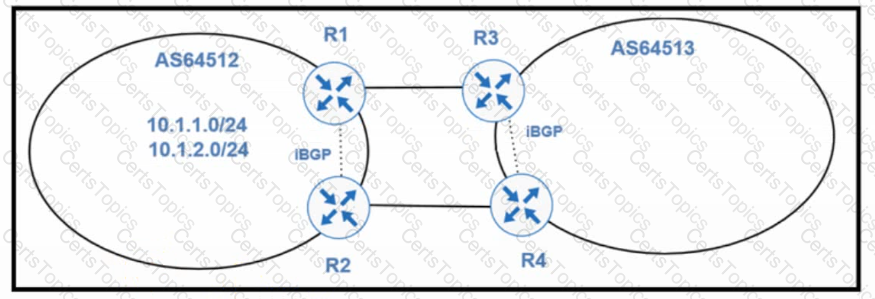
Refer to the exhibit. An architect designs a BGP policy for a customer that requires load sharing of the links that connect with the upstream service provider. The customer has these requirements: • The inbound traffic destined to network 10.1.1.0/24 must transit the R3-R1 link, and if the link fails, all inbound traffic must transit the R4-R2 link.
• The inbound traffic destined to network 10.1.2.0/24 must transit the R4-R2 link, and if the link fails, all inbound traffic should transit the R3-R1 link.
Which solution must the architect choose?
Which two functions does the control plane node provide in a Cisco SD-Access architecture? (Choose two.)
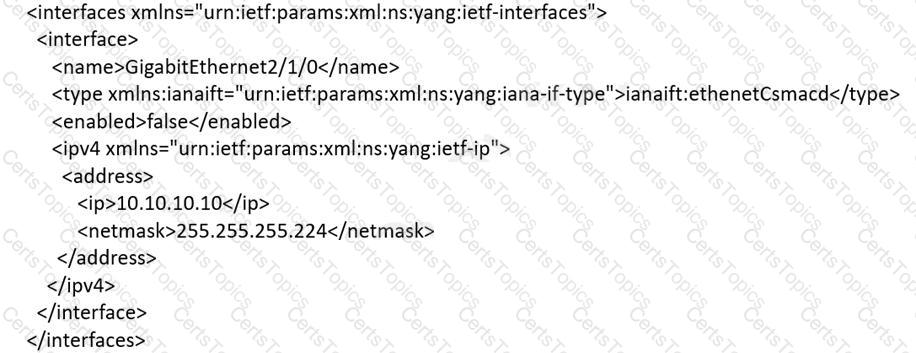
An engineer must use YANG with an XML representation to configure a Cisco IOS XE switch with these specifications:
IP address 10.10.10.10/27 configured on the interface GigabitEthernet2/1/0
connectivity from a directly connected host 10.10.10.1/27
Which YANG data model set must the engineer choose?
A)
B)
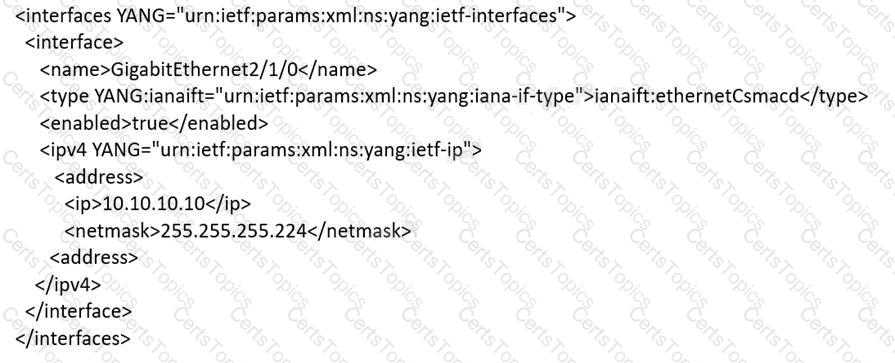
C)
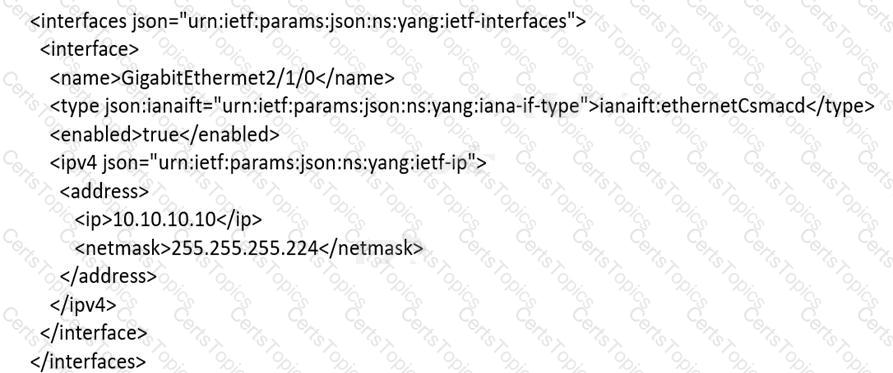
D)
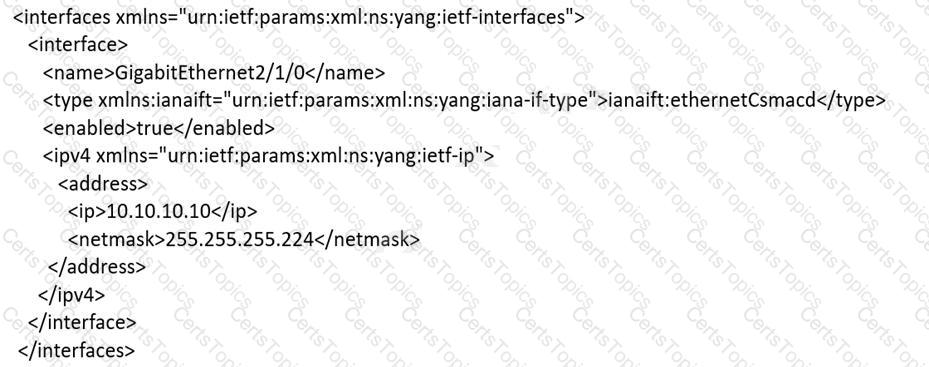
Refer to the exhibit.
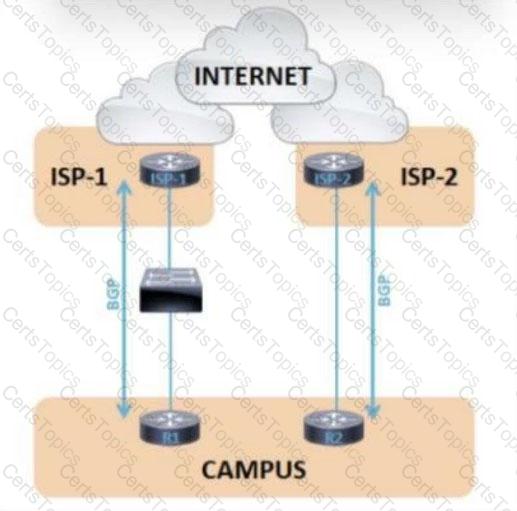
The failover time of ISP-2 is significantly shorter than ISP-1 when an interface on the ISP router toward the campus network fails. Which solution minimizes the downtime to the sub-second?
A customer with an IPv4 only network topology wants to enable IPv6 connectivity while preserving the IPv4 topology services. The customer plans to migrate IPv4 services to the IPv6 topology, then decommission the IPv4 topology. Which topology supports these requirements?
An engineer must establish a direct connection between two remote offices. The new connection must be established using a logical path, share a common broadcast domain, connect over private WAN, and have as little overhead as possible. Which technology must the engineer choose?
An engineer must design a solution to provide backup connectivity between two sites. The engineer plans to use an Internet connection but company policy requires the connection to be encrypted. Additionally, there are several applications that utilize multicast to deliver video streams between the sites. Which technology should the design include?
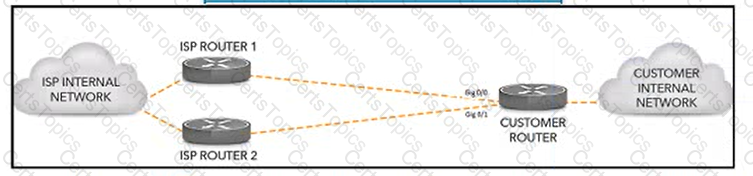
Refer to the exhibit. A customer has two eBGP peerings from a single CE router toward two service providers. The customer has hired an architect to design a solution to ensure certain traffic enters the customer's network through interface g¡g0/0. Which solution must the architect include in the design?
A network engineer is redesigning a company's QoS solution. The company is currently using IP Precedence, but the engineer plans to move to DiffServ. It is important that the new solution provide backward compatibility with the current solution. Which technology should the design include?
A company has many spoke sites with two data centers. The company wants to exchange the routing information between the data centers and the spoke sites using EIGRP. All locations belong to a single AS. and auto-summarization Is disabled. Which two actions must the company choose? (Choose two.)
Refer to the exhibit.
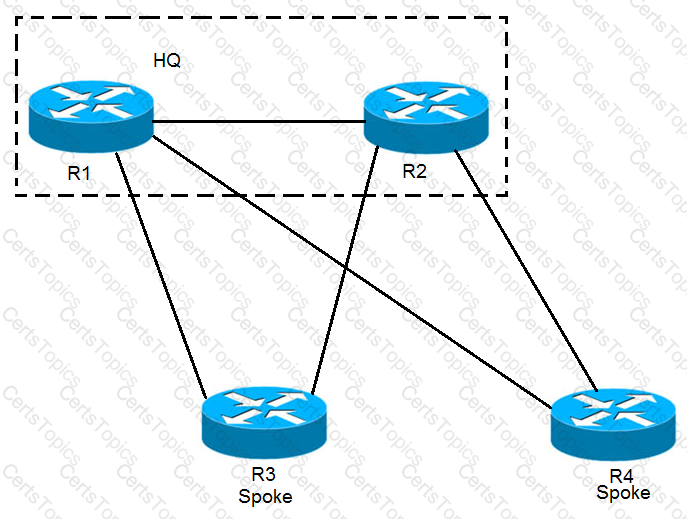
EIGRP has been configured on all links. The spoke nodes have been configured as EIGRP stubs, and the WAN links to R3 have higher bandwidth and lower delay than the links to R4. When a link failure occurs at the R1-R2 link, what happens to traffic on R1 that is destined for a subnet attached to R2?
A company requested that an architect propose a new IPv4 and IPv6 deployment strategy. The company wants a solution that is straightforward, with no information hiding or forwarding overhead. Which solution meets these requirements?
Refer to the exhibit.
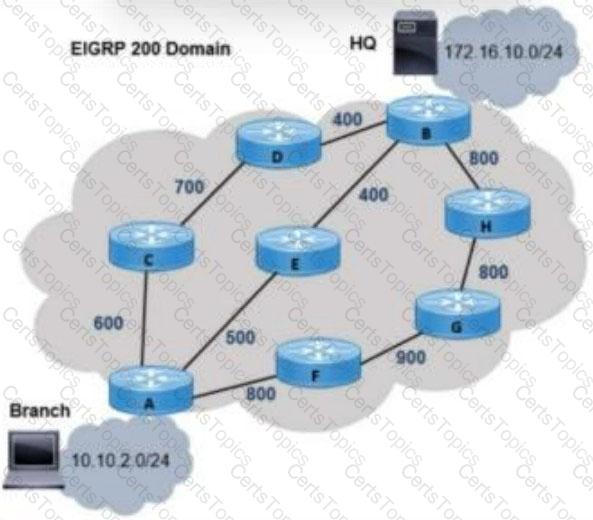
An architect is designing an EIGRP solution based on these requirements:
* Traffic forwarding should use the best two paths while all links are available
* Single path failure must not impact traffic between branch and HQ
Which solution must the architect select?
Which type of rendezvous point deployment is standards-based and supports dynamic RP discovery?
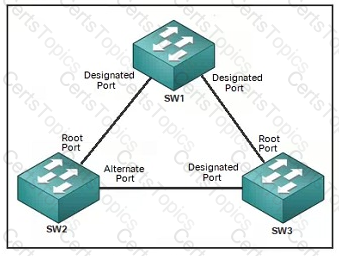
Refer to the exhibit. The connection between SW2 and SW3 is fiber and occasionally experiences unidirectional link failure. An architect must optimize the network to reduce the change of layer2 forwarding loops when the link fails. Which solution should the architect include?
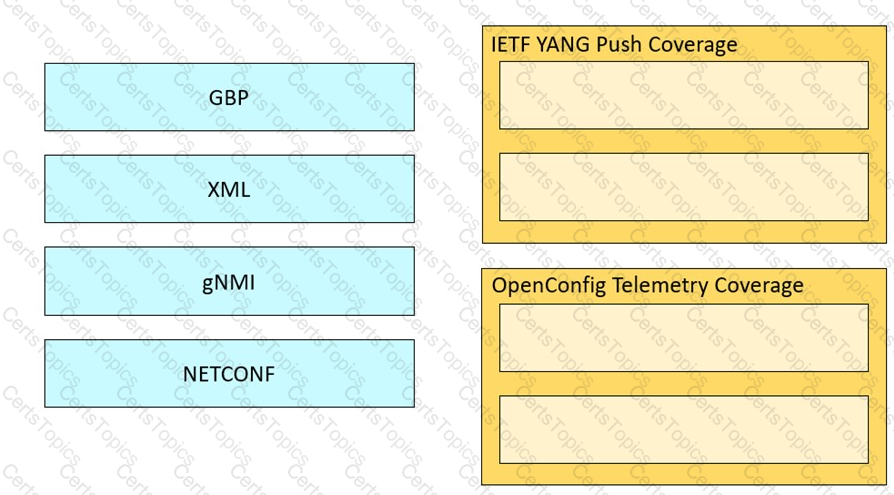
Drag and drop the model-driven telemetry considerations from the left onto the modes they apply to on the right.

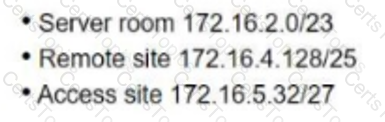
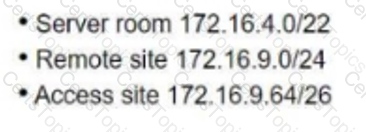
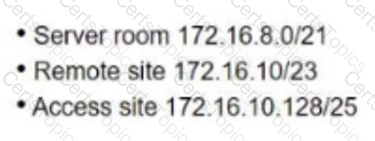
Refer to the exhibit. An architect is designing an IPv4 plan using the 172.16.0.0/16. The design must maximize the number of subnets while meeting these requirements:
500 hosts within the server room
100 hosts at the remote site
25 hosts at the access site
Which plan must the architect choose?
A)

B)
C)
D)
What is one function of the vSmart controller in an SD-WAN deployment?
An engineer uses Postman and YANG to configure a router with:
OSPF process ID 200
network 172.16.10.128/26 enabled for Area 0
Which get-config reply verifies that the model set was designed correctly?
Which design consideration should be observed when EIGRP is configured on Data Center switches?
A global organization with several branches hired a network architect to design an overlay VPN solution. The branches communicate with each other frequently. The customer expects to add more branches in the future. To meet the customer's security requirements, the architect plans to provide traffic protection using dynamic IPsec tunnels. Which solution should the architect choose?
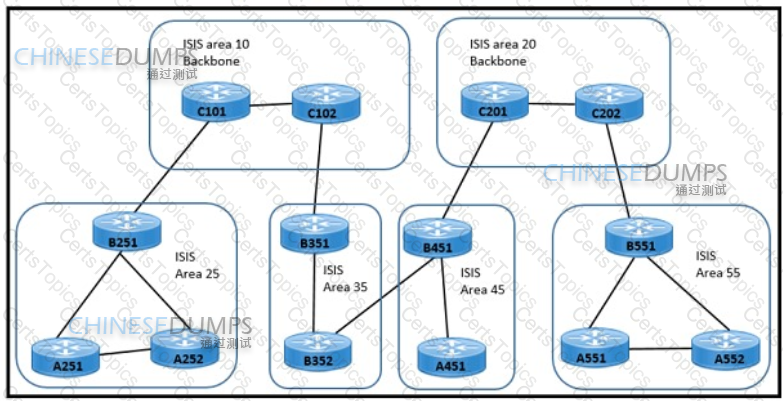
Refer to the exhibit An engineer is designing a hierarchical ISIS solution for an enterprise customer with these requirements
Users in areas 25 and 55 send and receive traffic from both backbone areas
Link flaps in areas 35 and 45 must not impact other areas
Routers will double within the next 12 months in areas 35 and 45
Which design must the engineer select?
An architect is designing a network that will utilize the spanning tree protocol to ensure a loop-free topology. The network will support an engineering environment where it is necessary for end users to connect their own network switches for testing purposes. Which feature should the architect include in the design to ensure the spanning tree topology is not affected by these rogue switches?
An engineer is designing a multicast network for a company specializing in VoD content. Receivers are across the Internet, and for performance reasons, the multicast framework close to the receivers within each AS. For high availability, if the sources in one AS are no longer available, the receivers of that AS must be able to receive the VoD content from sources in another AS. Which feature must the design include?
An existing network solution is using BFD in echo mode. Several of the network devices are experiencing high CPU utilization which an engineer has determined is related to the BFD feature. Which solution should the engineer leverage to reduce the CPU load?
Which OSPF area blocks LSA Type 3, 4 and 5, but allows a default summary route?
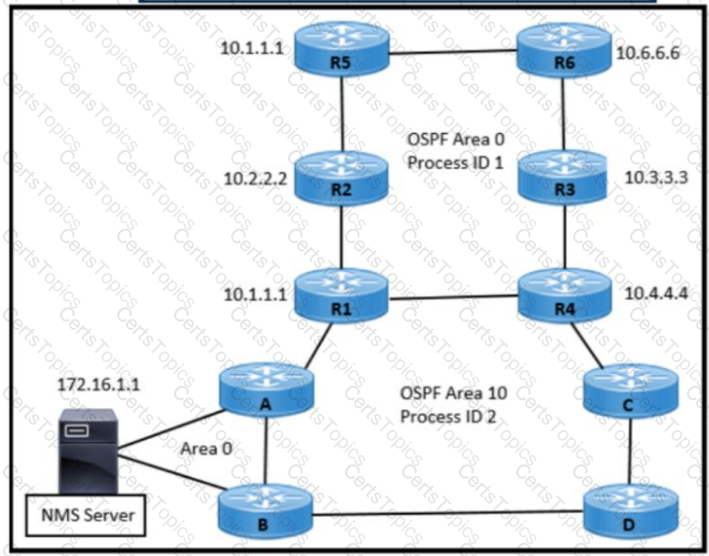
Refer to the exhibit An engineer is designing an OSPF solution with these requirements:
NMS server will manage R5 and R6.
Upon failure of R1. all NMS traffic should be routed through R4.
Upon failure of the link between R5 and R6. all traffic destined for 10.6.6.6 should be routed through R4
Which solution must the engineer choose?
What is the purpose of a Cisco SD-Access underlay network?
An engineer must peer with an ISP for internet connectivity using BGP, initially, the engineer wants to receive only specific prefixes from the ISP and a default route. However, the solution must provide the flexibility to add prefixes in the future at short notice. The ISP has a two-week change process in place. Which route filtering solution must the engineer employ?
Which two overlay network design considerations must be made for a Cisco SD-Access network? (Choose two.)
A company must automate a set of complex changes aligned with DR testing in the network. These changes are specific, and the DR playbook will be adjusted in the future. The playbook has diverse routing and switching assets in scope as well as multiple vendor and hardware platforms. A developer will create a thin, web front-end microservice and integrate with an Open daylight controller to push changes to the network. Which YANG model should be used?
Which function are fabric intermediate nodes responsible for in an SD-Access Architecture?
A company plans to transition to IPv6. They will link their IPv4 addresses to the lowest significant bits of the new Ipv6 addresses. A network administrator with an employee id: 4264:42:116 is preparing a mapping schema for the new IPv6 addresses. Which address does the 172.16.10.0/24 network translate to?
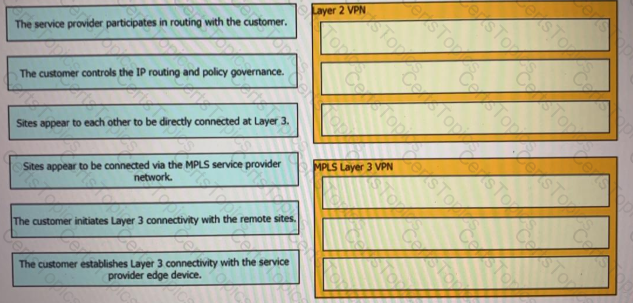
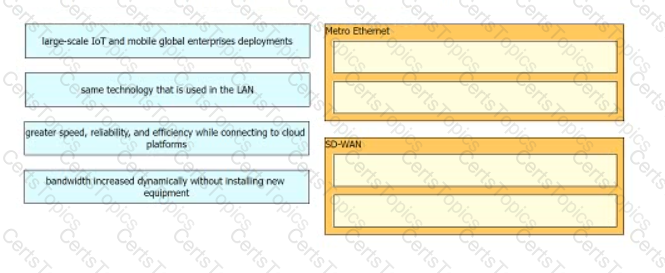
Drag and drop the descriptions from the left onto the corresponding VPN types on the rights.
Drag and drop the properties from the left onto the protocols they describe on the right.
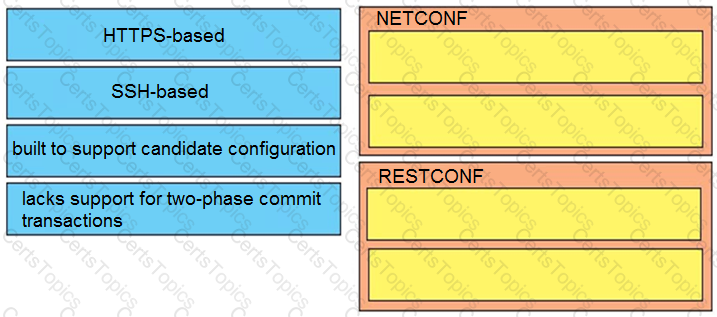
Drag and drop the descriptions from the left onto the categories they apply to on the right.
When vEdge router redundancy is designed, which FHRP is supported?
An engineer is designing a Layer 3 campus network running EIGRP between the core, aggregation, and access layers. The access layer switches will be connected to the aggregation layer using Layer 3 copper connections. The engineer wants to improve convergence time for access layer switch failures. Which technique must the design include?
Which node performs the LISP Map-Server and Map-Resolver functions in the Cisco SD-Access network architecture?
Refer to the exhibit.
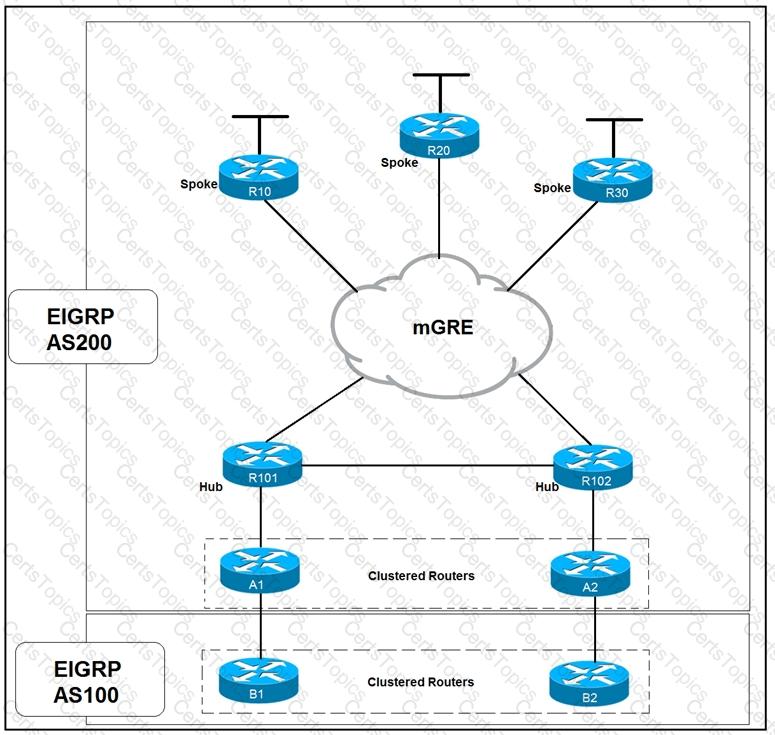
Which solution decreases the EIGRP convergence time?
An engineer is looking for a standards-driven YANG model to manage a multivendor network environment. Which model must the engineer choose?
How is redundancy achieved among Cisco vBond Orchestrators in a Cisco SD-WAN deployment?
When is it advisable to provide dedicated control plane nodes within a Cisco SD-Access design?
What is the purpose of an edge node in an SD-Access network fabric?
An engineer uses Postman and YANG to configure a router with:
OSPF process ID 400
network 192.168.128.128/25 enabled for Area 0
Which get-config reply verifies that the model set was designed correctly?
An architect is creating a migration strategy for a large organization in which the choice made by the application between IPv6 and IPv4 is based on the DNS request. Which migration strategy does the architect choose?
Drag and drop the elements from the left onto the functions they perform in the Cisco SD-WAN architecture on the right.
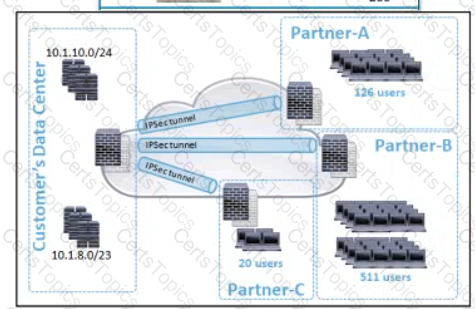
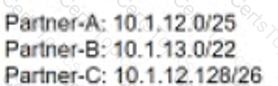
Refer to the exhibit. A customer is planning to onboard three new VPN partner connections in the data center. The new subnets must not overlap with the existing data center network, and the subnet size must not be bigger than necessary. The customer dedicated 10.1.8.0/21 for this design. Ho1// must the subnets be divided to meet these requirements?
A)

B)

C)

D)
An engineer is designing a multicast network for a financial application Most of the multicast sources also receive multicast traffic (many-to-many deployment model). To better routing tables, the design must not use source trees. Which multicast protocol satisfies these requirements?