Which part of SmartConsole allows administrators to add, edit delete, and clone objects?
CPU-level of your Security gateway is peaking to 100% causing problems with traffic. You suspect that the problem might be the Threat Prevention settings.
The following Threat Prevention Profile has been created.
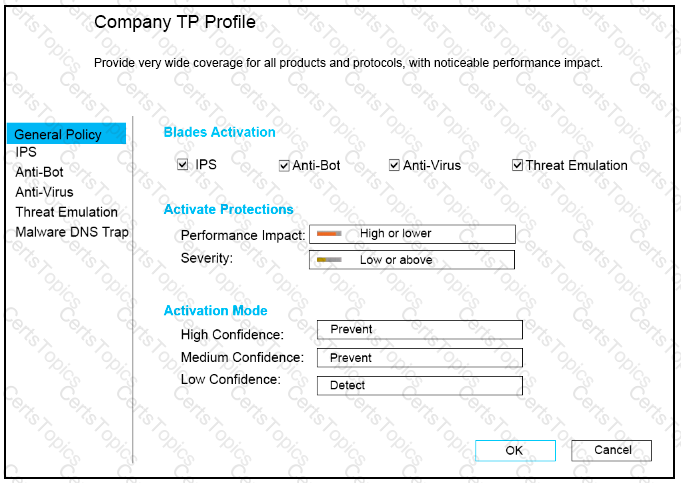
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
In SmartConsole, objects are used to represent physical and virtual network components and also some logical components. These objects are divided into several categories. Which of the following is NOT an objects category?
When a SAM rule is required on Security Gateway to quickly block suspicious connections which are not restricted by the Security Policy, what actions does the administrator need to take?
Fill in the blank: Permanent VPN tunnels can be set on all tunnels in the community, on all tunnels for specific gateways, or__________.
When doing a Stand-Alone Installation, you would install the Security Management Server with which other Check Point architecture component?
Which option in tracking allows you to see the amount of data passed in the connection?
You want to set up a VPN tunnel to a external gateway. You had to make sure that the IKE P2 SA will only be established between two subnets and not all subnets defined in the default VPN domain of your gateway.
Is it possible to have more than one administrator connected to a Security Management Server at once?
True or False: In R80, more than one administrator can login to the Security Management Server with write permission at the same time.
To increase security, the administrator has modified the Core protection ‘Host Port Scan’ from ‘Medium’ to ‘High’ Predefined Sensitivity. Which Policy should the administrator install after Publishing the changes?
In the Check Point Security Management Architecture, which component(s) can store logs?
Fill in the blanks: Gaia can be configured using _______ the ________.
Which of the following is used to initially create trust between a Gateway and Security Management Server?
SmartConsole provides a consolidated solution for everything that is necessary for the security of an organization, such as the following
One of major features in R80.x SmartConsole is concurrent administration. Which of the following is NOT possible considering that AdminA, AdminB, and AdminC are editing the same Security Policy?
When a Security Gateway sends its logs to an IP address other than its own, which deployment option is installed?
If the Active Security Management Server fails or if it becomes necessary to change the Active to Standby, the following steps must be taken to prevent data loss. Providing the Active Security Management Server is responsible, which of these steps should NOT be performed:
URL Filtering cannot be used to:
View the rule below. What does the pen-symbol in the left column mean?
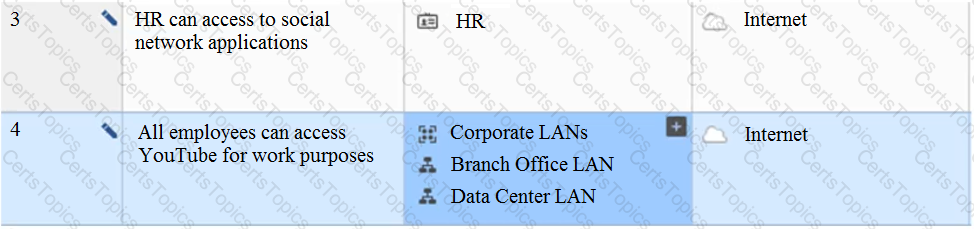
What is the main objective when using Application Control?
At what point is the Internal Certificate Authority (ICA) created?
Fill in the blank: Back up and restores can be accomplished through_________.
Access roles allow the firewall administrator to configure network access according to:
Fill in the blanks: Gaia can be configured using the ____ or ____
Fill in the blank: ____________ is the Gaia command that turns the server off.
Which SmartConsole tab shows logs and detects security threats, providing a centralized display of potential attack patterns from all network devices?
In ____________ NAT, the ____________ is translated.
Phase 1 of the two-phase negotiation process conducted by IKE operates in ______ mode.
By default, which port does the WebUI listen on?
Fill in the blank RADIUS Accounting gets_____data from requests generated by the accounting client
Choose what BEST describes users on Gaia Platform.
You are the Check Point administrator for Alpha Corp with an R80 Check Point estate. You have received a call by one of the management users stating that they are unable to browse the Internet with their new tablet connected to the company Wireless. The Wireless system goes through the Check Point Gateway. How do you review the logs to see what the problem may be?
Which option will match a connection regardless of its association with a VPN community?
Which tool allows you to monitor the top bandwidth on smart console?
What is the BEST command to view configuration details of all interfaces in Gaia CLISH?
How many layers make up the TCP/IP model?
John is the administrator of a R80 Security Management server managing r R77.30 Check Point Security Gateway. John is currently updating the network objects and amending the rules using SmartConsole. To make John’s changes available to other administrators, and to save the database before installing a policy, what must John do?
What is the Transport layer of the TCP/IP model responsible for?
What is the main difference between Static NAT and Hide NAT?
With URL Filtering, what portion of the traffic is sent to the Check Point Online Web Service for analysis?
In what way is Secure Network Distributor (SND) a relevant feature of the Security Gateway?
Fill in the blanks: A ____ license requires an administrator to designate a gateway for attachment whereas a _____ license is automatically attached to a Security Gateway.
When a Security Gateway communicates about its status to an IP address other than its own, which deployment option was chosen?
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
Which of the following is true about Stateful Inspection?
The competition between stateful inspection and proxies was based on performance, protocol support, and security. Considering stateful Inspections and Proxies, which statement is correct?
To view the policy installation history for each gateway, which tool would an administrator use?
Due to high CPU workload on the Security Gateway, the security administrator decided to purchase a new multicore CPU to replace the existing single core CPU. After installation, is the administrator required to perform any additional tasks?
Which is NOT an encryption algorithm that can be used in an IPSEC Security Association (Phase 2)?
What data MUST be supplied to the SmartConsole System Restore window to restore a backup?
Which Threat Prevention Software Blade provides comprehensive protection against malicious and unwanted network traffic, focusing on application and server vulnerabilities?
Your internal networks 10.1.1.0/24, 10.2.2.0/24 and 192.168.0.0/16 are behind the Internet Security Gateway. Considering that Layer 2 and Layer 3 setup is correct, what are the steps you will need to do in SmartConsole in order to get the connection working?
Which key is created during Phase 2 of a site-to-site VPN?
Which option in a firewall rule would only match and allow traffic to VPN gateways for one Community in common?
Which is a main component of the Check Point security management architecture?
Both major kinds of NAT support Hide and Static NAT. However, one offers more flexibility. Which statement is true?
The purpose of the Communication Initialization process is to establish a trust between the Security Management Server and the Check Point gateways. Which statement best describes this Secure Internal
Communication (SIC)?
Full synchronization between cluster members is handled by Firewall Kernel. Which port is used for this?
A SAM rule Is implemented to provide what function or benefit?
Which path below is available only when CoreXL is enabled?
Which two Identity Awareness daemons are used to support identity sharing?
Fill in the blank: An identity server uses a ___________ for user authentication.
What is the default tracking option of a rule?
An administrator is creating an IPsec site-to-site VPN between his corporate office and branch office. Both offices are protected by Check Point Security Gateway managed by the same Security Management Server (SMS). While configuring the VPN community to specify the pre-shared secret, the administrator did not find a box to input the pre-shared secret. Why does it not allow him to specify the pre-shared secret?
Which of the following describes how Threat Extraction functions?
Fill in the blank: When a policy package is installed, ________ are also distributed to the target installation Security Gateways.
What is the most complete definition of the difference between the Install Policy button on the SmartConsole’s tab, and the Install Policy within a specific policy?
Which of the completed statements is NOT true? The WebUI can be used to manage Operating System user accounts and
When connected to the Check Point R80 Management Server using the SmartConsole the first administrator to connect has a lock on:
Consider the Global Properties following settings:
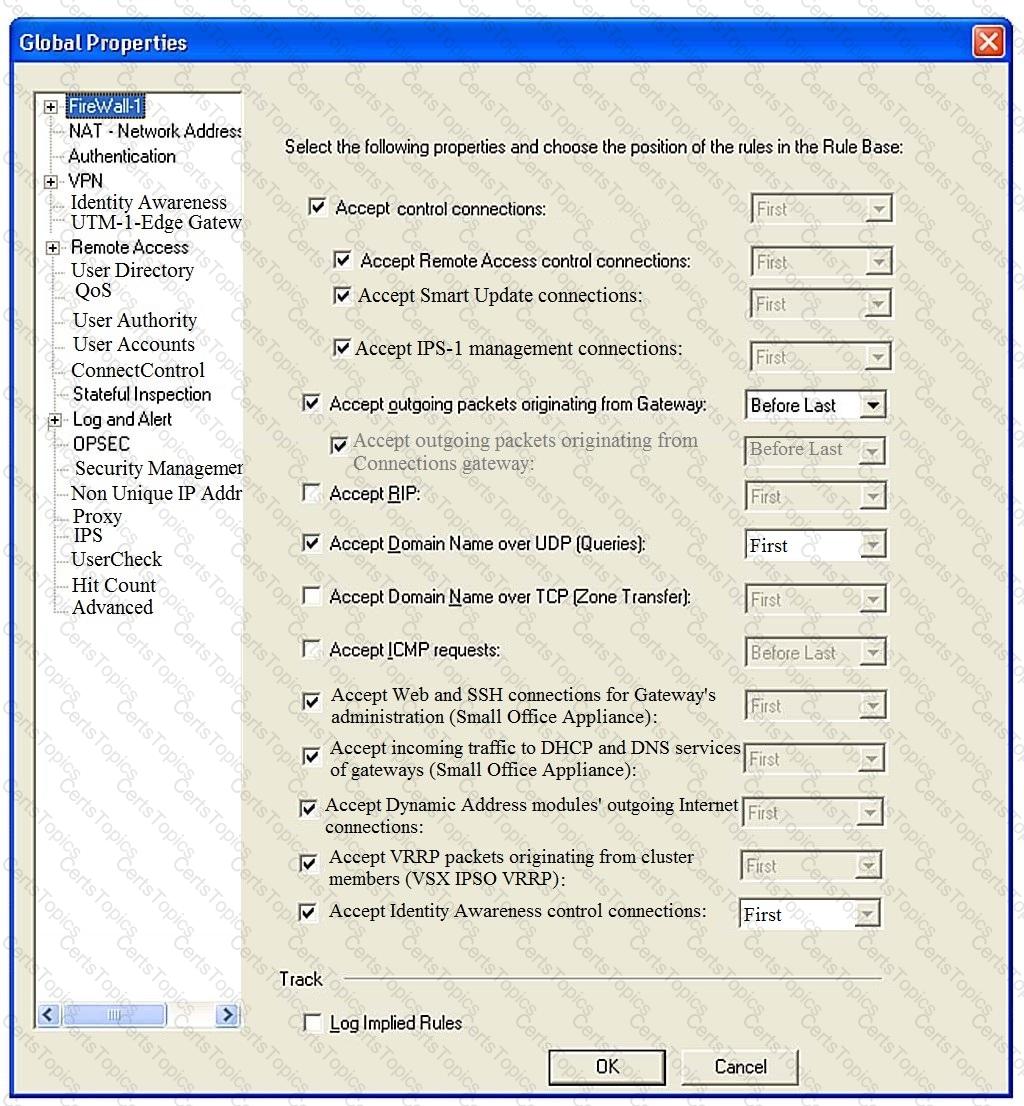
The selected option “Accept Domain Name over UDP (Queries)” means:
A security zone is a group of one or more network interfaces from different centrally managed gateways. What is considered part of the zone?
Which default Gaia user has full read/write access?
What is the purpose of the Clean-up Rule?
Which type of Check Point license ties the package license to the IP address of the Security Management Server?
Check Point ClusterXL Active/Active deployment is used when:
Using R80 Smart Console, what does a “pencil icon” in a rule mean?
What Check Point technologies deny or permit network traffic?
Which statement is NOT TRUE about Delta synchronization?
What is the SOLR database for?
Bob and Joe both have Administrator Roles on their Gaia Platform. Bob logs in on the WebUI and then Joe logs in through CLI. Choose what BEST describes the following scenario, where Bob and Joe are both logged in:
Fill in the blank: An Endpoint identity agent uses a ___________ for user authentication.
If an administrator wants to restrict access to a network resource only allowing certain users to access it, and only when they are on a specific network what is the best way to accomplish this?
Name the utility that is used to block activities that appear to be suspicious.
What is required for a certificate-based VPN tunnel between two gateways with separate management systems?
You want to store the GAiA configuration in a file for later reference. What command should you use?
Fill in the blank: The _____ feature allows administrators to share a policy with other policy packages.
Which method below is NOT one of the ways to communicate using the Management API’s?
What Identity Agent allows packet tagging and computer authentication?
Which of the following licenses are considered temporary?
In SmartEvent, a correlation unit (CU) is used to do what?
When an encrypted packet is decrypted, where does this happen?
What is NOT an advantage of Packet Filtering?
In R80 Management, apart from using SmartConsole, objects or rules can also be modified using:
Which tool provides a list of trusted files to the administrator so they can specify to the Threat Prevention blade that these files do not need to be scanned or analyzed?
Check Point licenses come in two forms. What are those forms?
Fill in the blank: An identity server uses a______________to trust a Terminal Server Identity Agent.
What command would show the API server status?
What are the three main components of Check Point security management architecture?
Where is the “Hit Count” feature enabled or disabled in SmartConsole?
Which command shows detailed information about VPN tunnels?
Which one of the following is TRUE?
What are the three types of UserCheck messages?
The Online Activation method is available for Check Point manufactured appliances. How does the administrator use the Online Activation method?
How can the changes made by an administrator before publishing the session be seen by a superuser administrator?
In the Check Point Security Management Architecture, which component(s) can store logs?
Fill in the blank Once a license is activated, a___________should be installed.
A stateful inspection firewall works by registering connection data and compiling this information. Where is the information stored?
Which encryption algorithm is the least secured?
Which type of attack can a firewall NOT prevent?
Which of the following is NOT a tracking log option in R80.x?
Which of the following is considered to be the more secure and preferred VPN authentication method?
Which tool is used to enable cluster membership on a Gateway?
Where can alerts be viewed?
Can you use the same layer in multiple policies or rulebases?
When should you generate new licenses?
How do you manage Gaia?
The CDT utility supports which of the following?
What needs to be configured if the NAT property ‘Translate destination on client side’ is not enabled in Global properties?
In which scenario will an administrator need to manually define Proxy ARP?
You are going to perform a major upgrade. Which back up solution should you use to ensure your database can be restored on that device?
Tom has connected to the Management Server remotely using SmartConsole and is in the process of making some Rule Base changes, when he suddenly loses connectivity. Connectivity is restored shortly afterward. What will happen to the changes already made?
Under which file is the proxy arp configuration stored?