What are three core characteristics of VMware’s Intrinsic Security solution? (Choose three.)
Which is a common solution to implement for inbound network attacks?
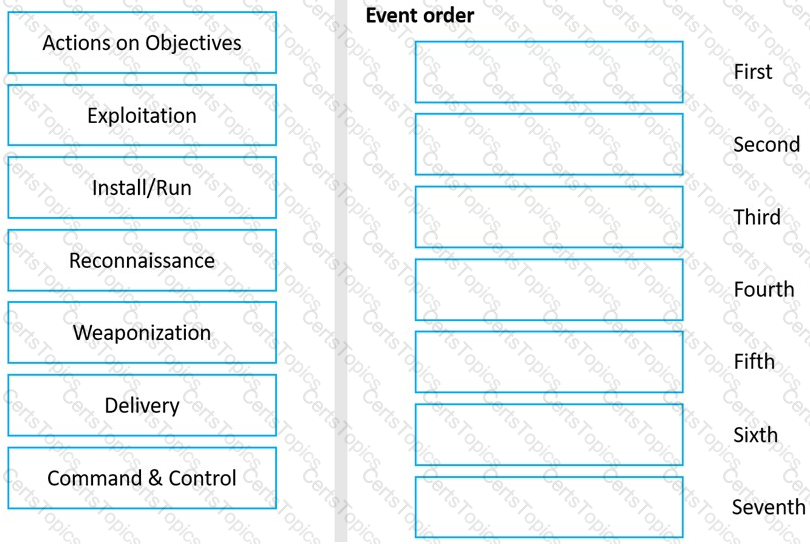
Drag and drop the Cyber Kill events on the left into their proper sequential order on the right.
Which Workspace ONE feature incorporates network range, device platform, and authentication method into decision making when evaluating an access request from a user?
Refer to the exhibit.
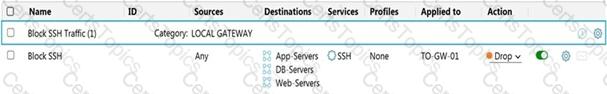
Whichstatement is true about the firewall rule?
Which three are industry best practices of Zero Trust framework? (Choose three.)
Which of the following is true about VMware Carbon Black Cloud Enterprise EDR watchlists?
When filtering firewall rules after selecting an object to filter by,which four columns does the filter search? (Choose four.)