Which two security approaches help build a strong authentication scheme? (Choose two.)
Refer to the exhibit.
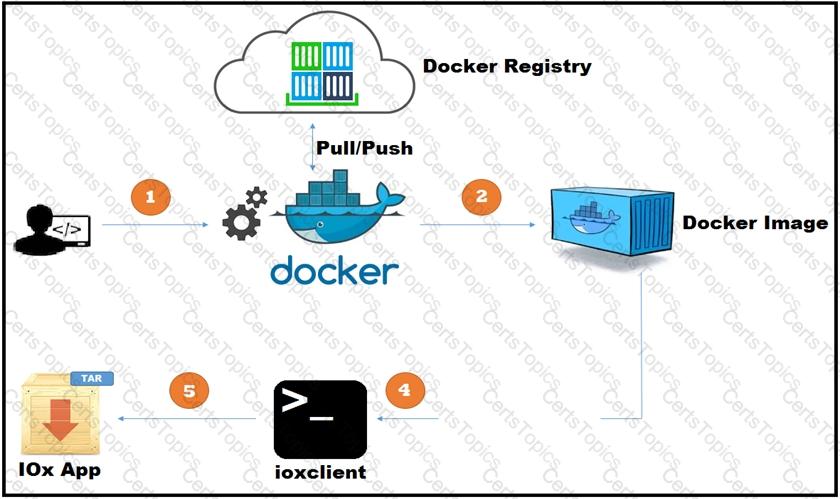
A new application has just been developed as a Docker container. What is the missing step for packaging the container ready for deployment in IOx?
Which data visualization technique should be used to represent an important single metric on a dashboard?
Which element ensures that PKI is used to establish the identity of IoT devices?