Which two technologies form a part of Netskope's Threat Protection module? (Choose two.)
You want to prevent Man-in-the-Middle (MITM) attacks on an encrypted website or application. In this scenario, which method would you use?
You want to use an out-of-band API connection into your sanctioned Microsoft 365 OneDrive for Business application to find sensitive content, enforce near real-time policy controls, and quarantine malware.
In this scenario, which primary function in the Netskope platform would you use to connect your application to Netskope?
Exhibit
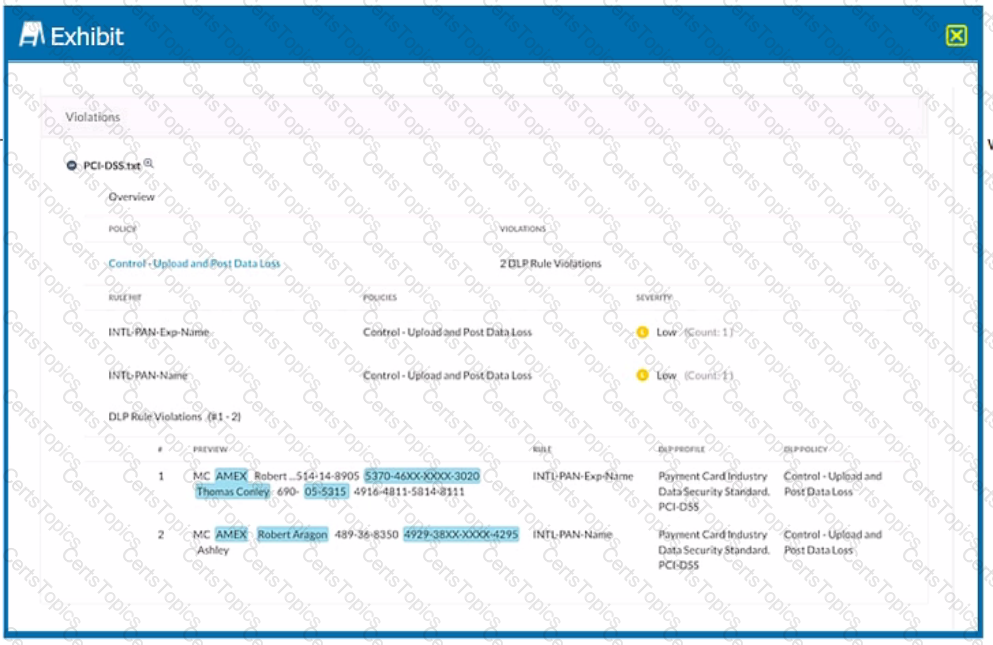
Which portion of the interface shown in the exhibit allows an administrator to set severity, assign ownership, track progress, and perform forensic analysis with excerpts of violating content?
You need to provide a quick view under the Skope IT Applications page showing only risky shadow IT cloud applications being used.
In this scenario, which two filter combinations would you use to accomplish this task? (Choose two.)
Which two statements describe a website categorized as a domain generated algorithm (DGA)? (Choose two.)
You want to set up a Netskope API connection to Box.
What two actions must be completed to enable this connection? (Choose two.)
You are required to mitigate malicious scripts from being downloaded into your corporate devices every time a user goes to a website. Users need to access websites from a variety of categories, including new websites.
Which two actions would help you accomplish this task while allowing the user to work? (Choose two.)
In which scenario would you use a SAML reverse proxy?
Which two cloud security and infrastructure enablement technologies does Secure Access Service Edge (SASE) combine into its unified platform? (Choose two.)
When using an out-of-band API connection with your sanctioned cloud service, what are two capabilities available to the administrator? (Choose two.)
Why would you want to define an App Instance?
Which three technologies describe the primary cloud service models as defined by the National Institute of Standards and Technology (NIST)? (Choose three.)
What correctly defines the Zero Trust security model?
You have an issue with the Netskope client connecting to the tenant.
In this scenario, what are two ways to collect the logs from the client machine? (Choose two.)
A company is attempting to steer traffic to Netskope using GRE tunnels. They notice that after the initial configuration, users cannot access external websites from their browsers.
What are three probable causes for this issue? (Choose three.)
You consume application infrastructure (middleware) capabilities by a third-party provider. What is the cloud service model that you are using in this scenario?
You are working with traffic from applications with pinned certificates. In this scenario, which statement is correct?