When operating in packet mode, which two services are available on the SRX Series device? (Choose two.)
Which two statements are correct about IKE security associations? (Choose two.)
Which two statements about the Junos OS CLI are correct? (Choose two.)
Which two criteria should a zone-based security policy include? (Choose two.)
You are monitoring an SRX Series device that has the factory-default configuration applied.
In this scenario, where are log messages sent by default?
You have configured a UTM feature profile.
Which two additional configuration steps are required for your UTM feature profile to take effect? (Choose two.)
When are Unified Threat Management services performed in a packet flow?
What are two valid address books? (Choose two.)
You want to prevent other users from modifying or discarding your changes while you are also editing the configuration file.
In this scenario, which command would accomplish this task?
You are asked to configure your SRX Series device to block all traffic from certain countries. The solution must be automatically updated as IP prefixes become allocated to those certain countries.
Which Juniper ATP solution will accomplish this task?
Which statement about global NAT address persistence is correct?
Which two statements are correct about the default behavior on SRX Series devices? (Choose two.)
You are assigned a project to configure SRX Series devices to allow connections to your webservers. The webservers have a private IP address, and the packets must use NAT to be accessible from the Internet. The webservers must use the same address for both connections from the Internet and communication with update servers.
Which NAT type must be used to complete this project?
You want to verify the peer before IPsec tunnel establishment.
What would be used as a final check in this scenario?
Which two features are included with UTM on an SRX Series device? (Choose two.)
What are two characteristics of a null zone? (Choose two.)
Exhibit.
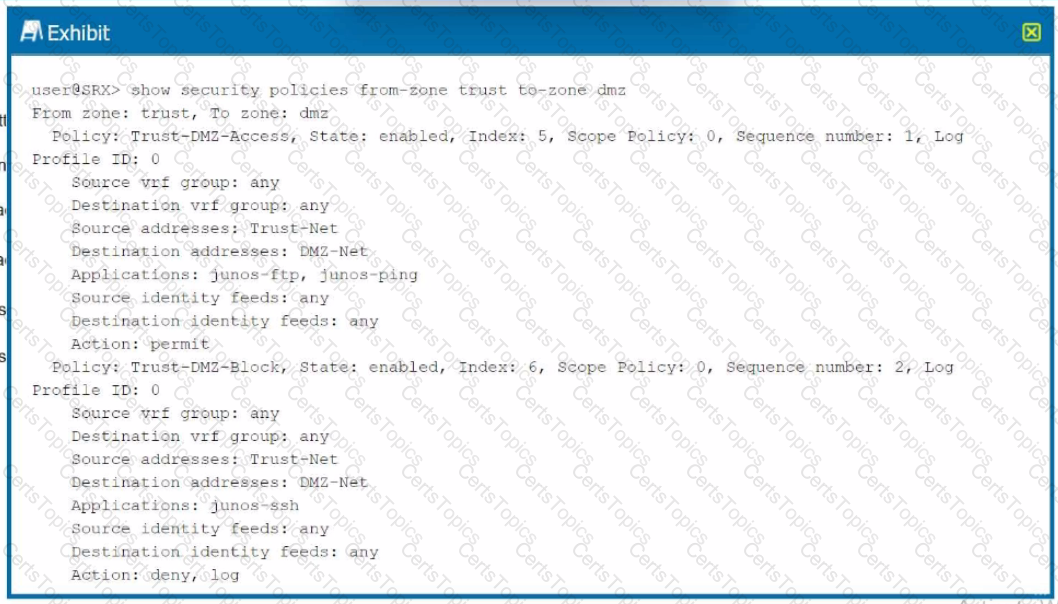
Which two statements are correct referring to the output shown in the exhibit? (Choose two.)
You are assigned a project to configure SRX Series devices to allow connections to your webservers. The webservers have a private IP address, and the packets must use NAT to be accessible from the
Internet. You do not want the webservers to initiate connections with external update servers on the Internet using the same IP address as customers use to access them.
Which two NAT types must be used to complete this project? (Choose two.)
Which two security features inspect traffic at Layer 7? (Choose two.)
In J-Web. the management and loopback address configuration option allows you to configure which area?
Which security policy type will be evaluated first?
Your company is adding IP cameras to your facility to increase physical security. You are asked to help protect these loT devices from becoming zombies in a DDoS attack.
Which Juniper ATP feature should you configure to accomplish this task?
What are two Juniper ATP Cloud feed analysis components? (Choose two.)
Which statement is correct about static NAT?
You are asked to verify that a license for AppSecure is installed on an SRX Series device.
In this scenario, which command will provide you with the required information?
What is the default timeout value for TCP sessions on an SRX Series device?
Which statement is correct about unified security policies on an SRX Series device?
What is the number of concurrent Secure Connect user licenses that an SRX Series device has by default?
Which statement is correct about global security policies on SRX Series devices?
Which two addresses are valid address book entries? (Choose two.)
The UTM features are performed during which process of the SRX Series device's packet flow?