Your network infrastructure transports data, voice, and video traffic. Users are complaining that voice and video calls are not performing to their expectations.
In this scenario, which technology would you implement to improve voice and video performance on your network?
When considering routing policies, which two statements are correct? (Choose two.)
What are two functions of the Routing Engine? (Choose two.)
Which two actions happen when multiple users issue the configure exclusive command to enter configuration mode on a Junos device? (Choose two.)
Exhibit
{hold:node0}[edit]
root# set system root-authentication ?
Possible completions:
+ apply-groups Groups from which to inherit configuration data
+ apply-groups-except Don't inherit configuration data from these groups
encrypted-password Encrypted password string
load-key-file File (URL) containing one or more ssh keys
plain-text-password Prompt for plain text password (autoencrypted)
> ssh-dsa Secure shell (ssh) DSA public key string
> ssh-rsa Secure shell (ssh) RSA public key string
{hold:node0}[edit]
root# set system root-authentication plain-text-password
New password:
Retype new password:
{hold:node0}[edit]
root# commit and-quit
[edit interfaces]
'ge-0/0/0'
HA management port cannot be configured
error: configuration check-out failed
{hold:node0}[edit]
root#
You are unable to remotely access your Juniper device using the CLI.
Referring to the exhibit, which command would you add to the existing configuration to enable remote CLI access?
Which prompt indicates that you are using configuration mode?
What are two types of transit traffic that traverse the forwarding plane of a Layer 3 router? (Choose two.)
In the Junos OS, which keyboard shortcut allows you to move to the start of the line?
When considering routing tables and forwarding tables, which two statements are correct? (Choose two.)
Which two statements are correct about the empioyee@Ri> prompt? (Choose two.)
Which two statements are true about the candidate configuration? (Choose two.)
What information would you find using the CLI help command?
You have just increased the MTU size of interface ge-0/0/0 and committed the configuration.
Which command would help you identify the applied MTU change?
You need to recover the root password on a Junos router without losing the current configuration settings.
Which three statements describe what you should perform in this scenario? (Choose three.)
Which two statements are correct about a Routing Engine? (Choose two.)
You are asked to configure your device running Junos OS to automatically archive your configuration upon commit
In this scenario, which two methods are supported by the Junos OS? (Choose two)
Which two statements apply to the Routing Engine functions? (Choose two.)
Click the Exhibit button.
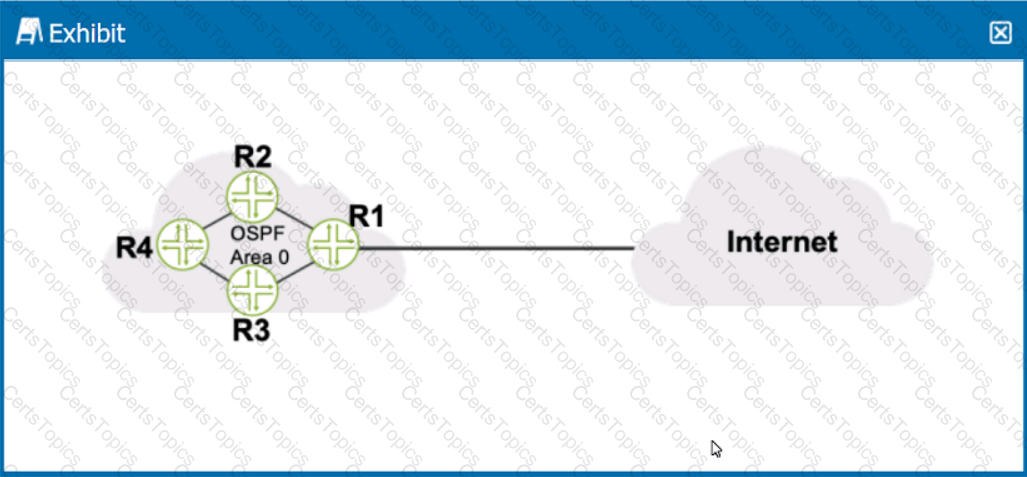
Referring to the exhibit, what should be configured on R1 to advertise a default static route into OSPF?
You configured your system authentication order using the set authentication-order tacplus radius password command.
Which statement is correct in this scenario?
Exhibit
term limit-icmp { from {
source-address {
172.25.11.0/24;
}
protocol icmp;
}
then {
count count-icmp; discard;
}
}
Referring to the exhibit, which two actions will occur when a packet matches the firewall filter? (Choose two.)
What are two physical interface properties? (Choose two.)
Exhibit
[edit]
user@routerl set interfaces ge-0/1/2 unit 0 family inet address 172.16.101.1/24 [edit]
user@router# commit check
configuration check succeeds
[edit]
user@router#
You need to configure interface ge-0/1/2 with an IP address of 172.16.100.1/24. You have accidentally entered 172.16.101.1/24 as shown in the exhibit.
Which command should you issue to solve the problem?
You are trying to diagnose packet loss at interface ge-0/0/3.
In this scenario, which command would help you view error statistics in real time?
You have logged on to a Junos device and are at the operational mode prompt.
Which two commands are used at this prompt? (Choose two.)
After the factory default configuration is loaded, which configuration object must be created prior to the first commit?
Which three benefits occur when operating an interior gateway protocol (IGP) in an autonomous system (AS)? (Choose three.)
What is a benefit of using J-Web?
What are two methods for navigating to configuration mode from an operational mode prompt? (Choose two.)
Which process in the Junos OS is responsible for maintaining routing protocols and tables?
Which two statements are correct about firewall filters? (Choose two.)