You work as an IT Technician for XYZ CORP. You have to take security measures for the wireless network of the company. You want to prevent other computers from accessing the company's wireless network. On the basis of the hardware address, which of the following will you use as the best possible method to accomplish the task?
RAS
MAC Filtering
SSID
WEP
MAC filtering is a security access control technique that allows specific network devices to access, or prevents them from accessing, the network. MAC filtering can also be used on a wireless network to prevent certain network devices from accessing the wireless network. MAC addresses are allocated only to hardware devices, not to persons.
Which of the following protocols are used to provide secure communication between a client and a server over the Internet? (Choose two)
TLS
SSL
HTTP
SNMP
SSL and TLS protocols are used to provide secure communication between a client and a server over the Internet.
You have made a program secure.c to display which ports are open and what types of services are running on these ports. You want to write the program's output to standard output and simultaneously copy it into a specified file. Which of the following commands will you use to accomplish the task?
cat
more
less
tee
You will use the tee command to write its content to standard output and simultaneously copy it into the specified file. The tee command is used to split the output of a program so that it can be seen on the display and also be saved in a file. It can also be used to capture intermediate output before the data is altered by another command or program. The tee command reads standard input, then writes its content to standard output, and simultaneously copies it into the specified file(s) or variables. The syntax of the tee command is as follows: tee [-a] [-i] [File] where, the -a option appends the output to the end of File instead of writing over it and the -i option is used to ignore interrupts. Answer: A is incorrect. The concatenate (cat) command is used to display or print the contents of a file. Syntax: cat filename For example, the following command will display the contents of the /var/log/dmesg file: cat /var/log/dmesg Note: The more command is used in conjunction with the cat command to prevent scrolling of the screen while displaying the contents of a file. Answer: C is incorrect. The less command is used to view (but not change) the contents of a text file, one screen at a time. It is similar to the more command. However, it has the extended capability of allowing both forwarB, Dackward navigation through the file. Unlike most Unix text editors/viewers, less does not need to read the entire file before starting; therefore, it has faster load times with large files. The command syntax of the less command is as follows: less [options] file_name Where,
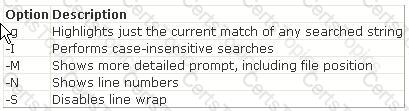 C:\Documents and Settings\user-nwz\Desktop\1.JPG
C:\Documents and Settings\user-nwz\Desktop\1.JPG
Answer: B is incorrect. The more command is used to view (but not modify) the contents of a text file on the terminal screen at a time. The syntax of the more command is as follows: more [options] file_name Where,
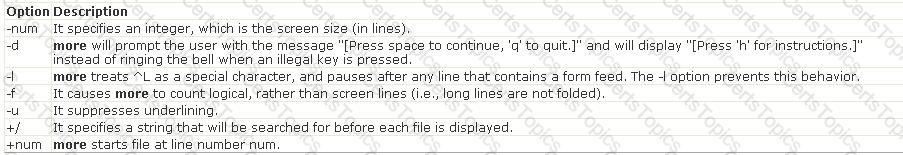 C:\Documents and Settings\user-nwz\Desktop\1.JPG
C:\Documents and Settings\user-nwz\Desktop\1.JPG
Which of the following services are provided by the proxy servers?
Intrusion detection
Logging
Hiding network resources
Caching
A proxy server is a very important element for firewall applications. The services that it provides are as follows: Hide network resources: Proxy replaces the network IP address with a single IP address. Multiple systems can use a single IP address. Logging: A proxy server can log incoming and outgoing access, allowing a user to see every possible details of successful and failed connections. Cache: A proxy server can save information obtained from the Internet. It regularly updates these copies and automatically shows these pages, and will thus not need to access the Internet to view them.
Which of the following statements about Secure Sockets Layer (SSL) are true? (Choose two)
It provides connectivity between Web browser and Web server.
It provides mail transfer service.
It provides communication privacy, authentication, and message integrity.
It uses a combination of public key and symmetric encryption for security of data.
Secure Sockets Layer (SSL) is a protocol used to transmit private documents via the Internet. SSL uses a combination of public key and symmetric encryption to provide communication privacy, authentication, and message integrity. Using the SSL protocol, clients and servers can communicate in a way that prevents eavesdropping and tampering of data on the Internet. Many Web sites use the SSL protocol to obtain confidential user information, such as credit card numbers. By convention, URLs that require an SSL connection start with https: instead of http:. By default, SSL uses port 443 for secured communication. For a SSL connection between a Web browser and Web server, you must enter https, for example, " ", instead of http as the protocol type in the URL. This will instruct the Web browser to use a different port for communication. SSL uses TCP port 443 for communication.
In which of the following attacking methods does an attacker distribute incorrect IP address?
DNS poisoning
IP spoofing
Mac flooding
Man-in-the-middle
In DNS poisoning attack, an attacker distributes incorrect IP address. DNS cache poisoning is a maliciously created or unintended situation that provides data to a caching name server that did not originate from authoritative Domain Name System (DNS) sources. Once a DNS server has received such non-authentic datA, Caches it for future performance increase, it is considered poisoned, supplying the non-authentic data to the clients of the server. To perform a cache poisoning attack, the attacker exploits a flaw in the DNS software. If the server does not correctly validate DNS responses to ensure that they are from an authoritative source, the server will end up caching the incorrect entries locally and serve them to other users that make the same request. Answer: B is incorrect. IP (Internet Protocol) address spoofing is an attack in which an attacker creates the IP packets with a forged (spoofed) source IP address with the purpose of concealing the identity of the sender or impersonating another computing system. The basic protocol for sending data over the Internet and many other computer networks is the Internet Protocol ("IP"). The header of each IP packet contains, among other things, the numerical source and destination address of the packet. The source address is normally the address that the packet was sent from. By forging the header so it contains a different address, an attacker can make it appear that the packet was sent by a different machine. The machine that receives spoofed packets will send response back to the forged source address, which means that this technique is mainly used when the attacker does not care about the response or the attacker has some way of guessing the response. Answer: D is incorrect. Man-in-the-middle attacks occur when an attacker successfully inserts an intermediary software or program between two communicating hosts. The intermediary software or program allows attackers to listen to and modify the communication packets passing between the two hosts. The software intercepts the communication packets and then sends the information to the receiving host. The receiving host responds to the software, presuming it to be the legitimate client. Answer: C is incorrect. MAC flooding is a technique employed to compromise the security of network switches. In a typical MAC flooding attack, a switch is flooded with packets, each containing different source MAC addresses. The intention is to consume the limited memory set aside in the switch to store the MAC address-to-physical port translation table. The result of this attack causes the switch to enter a state called failopen mode, in which all incoming packets are broadcast out on all ports (as with a hub), instead of just down the correct port as per normal operation. A malicious user could then use a packet sniffer (such as Wireshark) running in promiscuous mode to capture sensitive data from other computers (such as unencrypted passwords, e-mail and instant messaging conversations), which would not be accessible were the switch operating normally.
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of He has successfully completed the following pre-attack phases while testing the security of the server: Footprinting Scanning Now he wants to conduct the enumeration phase. Which of the following tools can John use to conduct it?
PsPasswd
WinSSLMiM
PsFile
UserInfo
John can use the UserInfo, PsFile, and PsPasswd tools in the enumeration phase. UserInfo is a utility that retrieves all available information about any known user from any Windows 2000/NT operating system (accessible by TCP port 139). UserInfo returns mainly the following information: SID and Primary group Logon restrictions and smart card requirements Special group Password expiration Note: UserInfo works as a NULL user even if the RestrictedAnonymous value in the LSA key is set to 1 to specifically deny anonymous enumeration. PsFile is a command-line utility that shows a list of files on a system that are opened remotely. It also allows a user to close opened files either by name or by a file identifier. The command syntax for PsFile is as follows: psfile [\\RemoteComputer [-u Username [-p Password]]] [Id | path] [-c] -u specifies the optional user name for logging in to a remote computer. -p specifies a password for a user name. If this is omitted, the user is prompted to enter the password without it being echoed to the screen. Id is the identifier of the file about which the user wants to display information. -c closes the files identifed by the ID or path. PsPasswd is a tool that helps Network Administrators change an account password on the local or remote system. The command syntax of PsPasswd is as follows: pspasswd [\\computer[,computer[,..] | @file [-u user [-p psswd]] Username [NewPassword]
The following output is generated by running the show ip route command: RouterA#show ip route < - - Output Omitted for brevity - -> Which next hop address will RouterA use in forwarding traffic to 10.10.100.0/24?
192.168.10.0
172.18.60.1
172.18.50.1
172.18.1.1
The routing table displays various RIP and Connected routes. There is no routing entry for 10.10.100.0/24, but there is a default route in the routing table using 172.18.1.1 as the next hop router. Given that 10.10.100.0/24 does not have a direct entry in the routing table, RouterA will forward traffic to the default route next hop address of 172.18.1.1. Answer: A is incorrect. The address does not appear in the routing table as a next hop router, in addition to being an actual subnet number for 192.168.10.0/24. Answer: C is incorrect. 172.18.50.1 is the next hop for reaching 192.168.11.0. Answer: B is incorrect. 172.18.60.1 is the next hop for reaching 192.168.12.0.
Which of the following recovery plans includes specific strategies and actions to deal with specific variances to assumptions resulting in a particular security problem, emergency, or state of affairs?
Disaster recovery plan
Continuity of Operations Plan
Business continuity plan
Contingency plan
A contingency plan is a plan devised for a specific situation when things could go wrong. Contingency plans include specific strategies and actions to deal with specific variances to assumptions resulting in a particular problem, emergency, or state of affairs. They also include a monitoring process and triggers for initiating planned actions. Answer: A is incorrect. Disaster recovery is the process, policies, and procedures related to preparing for recovery or continuation of technology infrastructure critical to an organization after a natural or human-induced disaster. Answer: C is incorrect. It deals with the plans and procedures that identify and prioritize the critical business functions that must be preserved. Answer: B is incorrect. It includes the plans and procedures documented that ensure the continuity of critical operations during any period where normal operations are impossible.
John works as a professional Ethical Hacker. He has been assigned a project to test the security of He performs Web vulnerability scanning on the We-are-secure server. The output of the scanning test is as follows: C.\whisker.pl -h target_IP_address -- whisker / v1.4.0 / rain forest puppy / -- = - = - = - = - = = Host: target_IP_address = Server: Apache/1.3.12 (Win32) ApacheJServ/1.1 mod_ssl/2.6.4 OpenSSL/0.9.5a mod_perl/1.22 + 200 OK: HEAD /cgi-bin/printenv John recognizes /cgi-bin/printenv vulnerability ( 'Printenv' vulnerability) in the We_are_secure server. Which of the following statements about 'Printenv' vulnerability are true?
With the help of 'printenv' vulnerability, an attacker can input specially crafted links and/or other malicious scripts.
'Printenv' vulnerability maintains a log file of user activities on the Website, which may be useful for the attacker.
The countermeasure to 'printenv' vulnerability is to remove the CGI script.
This vulnerability helps in a cross site scripting attack.
'Printenv' vulnerability allows an attacker to input specially crafted links and/or other malicious scripts. For example, <script>alert (An attacker can misuse it!)</script> Since 'printenv' is just an example CGI script (It comes with various versions of the Apache Web server.) that has no real use and has its own problems, there is no problem in removing it. Answer: B is incorrect. 'Printenv' does not maintain any log file of user activities.
Adam works as a Security Analyst for Umbrella Inc. He is retrieving large amount of log data from syslog servers and network devices such as Router and switches. He is facing difficulty in analyzing the logs that he has retrieved. To solve this problem, Adam decides to use software called Sawmill. Which of the following statements are true about Sawmill?
It incorporates real-time reporting and real-time alerting.
It is used to analyze any device or software package, which produces a log file such as Web servers, network devices (switches & routers etc.), syslog servers etc.
It is a software package for the statistical analysis and reporting of log files.
It comes only as a software package for user deployment.
Sawmill is a software package for the statistical analysis and reporting of log files, with dynamic contextual filtering, 'live' data zooming, user interface customization, and custom calculated reports. Sawmill incorporates real-time reporting and real-time alerting. Sawmill also includes a page tagging server and JavaScript page tag for the analysis of client side clicks (client requests) providing a total view of visitor traffic and on-site behavioral activity. Sawmill Analytics is offered in three forms, as a software package for user deployment, as a turnkey on-premise system appliance, and as a SaaS service. Sawmill analyzes any device or software package producing a log file and that includes Web servers, firewalls, proxy servers, mail servers, network devices (switches & routers etc.), syslog servers, databases etc. Its range of potential uses by knowledge workers is essentially limitless. Answer: D is incorrect. Sawmill Analytics software is available in three different forms; as a software package for user deployment, as a turnkey on-premise system appliance, and as a SaaS service.
Choose the benefits of deploying switches over hubs in your infrastructure. (Choose two)
Layer 2 switches allow for the creation of Virtual LANs providing options for further segmentation and security.
Switches lower the number of collisions in the environment.
Switches create an environment best suited for half duplex communications. This improves network performance and the amount of available bandwidth.
Layer 2 switches increase the number of broadcast domains in the environment.
Switches differ from hubs in that they break up Collision Domains. Each port on a switch equals one Collision Domain. Therefore, a switch will lower the number of collisions within the infrastructure. Managed switches typically offer the ability to create Virtual LANs. Virtual LANs allow the switch to create multiple LANs/network segments that are Virtual. This allows the switch to create additional environments where needed.
You are the Security Administrator for an Internet Service Provider. From time to time your company gets subpoenas from attorneys and law enforcement for records of customers' access to the internet. What policies must you have in place to be prepared for such requests?
Group access policies
Backup policies
User access policies
Storage and retention policies
Storage and retention policies will determine how long you keep records (such as records of customers Web activity), how you will store them, and how you will dispose of them. This will allow you to know what records you should still have on hand should a legal request for such records come in. Answer: C is incorrect. User policies might determine what a customer has access to, but won't help you identify what they actually did access. Answer: A is incorrect. Group policies are usually pertinent to network administration, not the open and uncontrolled environment of an ISP. Answer: B is incorrect. Backup policies dictate how data is backed up and stored.
A Cisco router can have multiple connections to networks. These connections are known as interfaces for Cisco Routers. For naming each interface, Cisco generally uses the type of interface as part of the name. Which of the following are true about the naming conventions of Cisco Router interfaces?
An interface connected to a serial connection always starts with an S.
An interface connected to a Token Ring segment always starts with To.
An Ethernet interface that is fast always starts with an F.
An interface connected to an Ethernet segment of the network always starts with an En.
A Cisco router can have multiple connections to networks. These connections are known as interfaces for Cisco Routers. For naming each interface, Cisco generally uses the type of interface as part of the name. Following are some of the naming conventions of Cisco Router interfaces: An Ethernet interface that is fast always starts with an F. An interface connected to a serial connection always starts with an S. An interface connected to an Ethernet segment of the network always starts with an E. An interface connected to a Token Ring segment always starts with To.
A Web developer with your company wants to have wireless access for contractors that come in to work on various projects. The process of getting this approved takes time. So rather than wait, he has put his own wireless router attached to one of the network ports in his department. What security risk does this present?
None, adding a wireless access point is a common task and not a security risk.
It is likely to increase network traffic and slow down network performance.
This circumvents network intrusion detection.
An unauthorized WAP is one way for hackers to get into a network.
Any unauthorized Wireless Access Point (WAP) is a serious security breach. Its configuration might be very unsecure. For example it might not use encryption or MAC filtering, thus allowing anyone in range to get on the network.
Which of the following techniques are used after a security breach and are intended to limit the extent of any damage caused by the incident?
Safeguards
Detective controls
Corrective controls
Preventive controls
Corrective controls are used after a security breach. After security has been breached, corrective controls are intended to limit the extent of any damage caused by the incident, e.g. by recovering the organization to normal working status as efficiently as possible. Answer: D is incorrect. Before the event, preventive controls are intended to prevent an incident from occurring, e.g. by locking out unauthorized intruders. Answer: B is incorrect. During the event, detective controls are intended to identify and characterize an incident in progress, e.g. by sounding the intruder alarm and alerting the security guards or the police. Answer: A is incorrect. Safeguards are those controls that provide some amount of protection to an asset.
You work as a Network Administrator for XYZ CORP. The company has a Linux-based network. The company needs to provide secure network access. You have configured a firewall to prevent certain ports and applications from forwarding the packets to the company's intranet. What does a firewall check to prevent these ports and applications from forwarding the packets to the intranet?
The network layer headers and the session layer port numbers
The application layer port numbers and the transport layer headers
The transport layer port numbers and the application layer headers
The presentation layer headers and the session layer port numbers
A firewall stops delivery of packets that are not marked safe by the Network Administrator. It checks the transport layer port numbers and the application layer headers to prevent certain ports and applications from forwarding the packets to an intranet. Answer: D, A, and B are incorrect. These are not checked by a firewall.
You are the security manager of Microliss Inc. Your enterprise uses a wireless network infrastructure with access points ranging 150-350 feet. The employees using the network complain that their passwords and important official information have been traced. You discover the following clues: The information has proved beneficial to an other company. The other company is located about 340 feet away from your office. The other company is also using wireless network. The bandwidth of your network has degraded to a great extent. Which of the following methods of attack has been used?
A piggybacking attack has been performed.
A DOS attack has been performed.
The information is traced using Bluebugging.
A worm has exported the information.
Piggybacking refers to access of a wireless Internet connection by bringing one's own computer within the range of another's wireless connection, and using that service without the subscriber's explicit permission or knowledge. It is a legally and ethically controversial practice, with laws that vary in jurisdictions around the world. While completely outlawed in some jurisdictions, it is permitted in others. The process of sending data along with the acknowledgment is called piggybacking. Answer: C is incorrect. Bluebugging is an attack used only in a Bluetooth network. Bluebugging is a form of bluetooth attack often caused by a lack of awareness. Bluebugging tools allow attacker to "take control" of the victim's phone via the usage of the victim's Bluetooth phone headset. It does this by pretending to be the users bluetooth headset and therefore "tricking" the phone to obey its call commands. Answer: D is incorrect. A worm is a software program that uses computer networks and security holes to replicate itself from one computer to another. It usually performs malicious actions, such as using the resources of computers as well as shutting down computers. Answer: B is incorrect. A Denial-of-Service (DoS) attack is mounted with the objective of causing a negative impact on the performance of a computer or network. It is also known as a network saturation attack or bandwidth consumption attack. Attackers perform DoS attacks by sending a large number of protocol packets to the network. The effects of a DoS attack are as follows: Saturates network resources Disrupts connections between two computers, thereby preventing communications between services Disrupts services to a specific computer Causes failure to access a Web site Results in an increase in the amount of spam A Denial-of-Service attack is very common on the Internet because it is much easier to accomplish. Most of the DoS attacks rely on the weaknesses in the TCP/IP protocol.
Which of the following attacks allows the bypassing of access control lists on servers or routers, and helps an attacker to hide? (Choose two)
DNS cache poisoning
DDoS attack
IP spoofing attack
MAC spoofing
Either IP spoofing or MAC spoofing attacks can be performed to hide the identity in the network. MAC spoofing is a hacking technique of changing an assigned Media Access Control (MAC) address of a networked device to a different one. The changing of the assigned MAC address may allow the bypassing of access control lists on servers or routers, either hiding a computer on a network or allowing it to impersonate another computer. MAC spoofing is the activity of altering the MAC address of a network card. Answer: A is incorrect. DNS cache poisoning is a maliciously created or unintended situation that provides data to a caching name server that did not originate from authoritative Domain Name System (DNS) sources. Once a DNS server has received such non-authentic datA, Caches it for future performance increase, it is considered poisoned, supplying the non-authentic data to the clients of the server. To perform a cache poisoning attack, the attacker exploits a flaw in the DNS software. If the server does not correctly validate DNS responses to ensure that they are from an authoritative source, the server will end up caching the incorrect entries locally and serve them to other users that make the same request. Answer: B is incorrect. In a distributed denial of service (DDOS) attack, an attacker uses multiple computers throughout the network that has been previously infected. Such computers act as zombies and work together to send out bogus messages, thereby increasing the amount of phony traffic. The major advantages to an attacker of using a distributed denial-of-service attack are that multiple machines can generate more attack traffic than one machine, multiple attack machines are harder to turn off than one attack machine, and that the behavior of each attack machine can be stealthier, making it harder to track down and shut down. TFN, TRIN00, etc. are tools used for a DDoS attack.
eBox Platform is an open source unified network server (or a Unified Network Platform) for SMEs. In which of the following forms can eBox Platform be used?
Unified Communications Server
Network Infrastructure Manager
Gateway
Sandbox
eBox Platform is an open source unified network server (or a Unified Network Platform) for SMEs. eBox Platform can act as a Gateway, Network Infrastructure Manager, Unified Threat Manager, Office Server, Unified Communications Server or a combination of them. Besides, eBox Platform includes a development framework to ease the development of new Unix-based services. Answer: D is incorrect. eBox Platform cannot act as a sandbox. A sandbox is a security mechanism for separating running programs. It is often used to execute untested code, or untrusted programs, from unverified third-parties, suppliers, and untrusted users.
Which of the following terms related to risk management represents the estimated frequency at which a threat is expected to occur?
Single Loss Expectancy (SLE)
Annualized Rate of Occurrence (ARO)
Exposure Factor (EF)
Safeguard
The Annualized Rate of Occurrence (ARO) is a number that represents the estimated frequency at which a threat is expected to occur. It is calculated based upon the probability of the event occurring and the number of employees that could make that event occur. Answer: C is incorrect. The Exposure Factor (EF) represents the % of assets loss caused by a threat. The EF is required to calculate the Single Loss Expectancy (SLE). Answer: A is incorrect. The Single Loss Expectancy (SLE) is the value in dollars that is assigned to a single event. SLE = Asset Value ($) X Exposure Factor (EF) Answer: D is incorrect. Safeguard acts as a countermeasure for reducing the risk associated with a specific threat or a group of threats.
Anonymizers are the services that help make a user's own Web surfing anonymous. An anonymizer removes all the identifying information from a user's computer while the user surfs the Internet. It ensures the privacy of the user in this manner. After the user anonymizes a Web access with an anonymizer prefix, every subsequent link selected is also automatically accessed anonymously. Which of the following are limitations of anonymizers?
ActiveX controls
Plugins
Secure protocols
Java applications
JavaScript
xplanation: Anonymizers have the following limitations: 1.HTTPS: Secure protocols such as 'https:' cannot be properly anonymized, as the browser needs to access the site directly to properly maintain the secure encryption. 2.Plugins: If an accessed site invokes a third-party plugin, there is no guarantee of an established independent direct connection from the user computer to a remote site. 3.Java: Any Java application accessed through an anonymizer will not be able to bypass the Java security wall. 4.ActiveX: ActiveX applications have almost unlimited access to the user's computer system. 5.JavaScript: The JavaScript scripting language is disabled with URL-based anonymizers.
What are the different categories of PL/SQL program units?
Default
Unnamed
Primary
Named
A named block is a PL/SQL block that Oracle stores in the database and can be called by name from any application. A named block is also known as a stored procedure. Named blocks can be called from any PL/SQL block. It has a declaration section, which is known as a header. The header may include the name of a block, type of the block, and parameter. The name and list of formal parameters are known as the signature of a subroutine. Once a named PL/SQL block is compiled, it gets permanently stored as p-code after compilation in the shared pool of the system global area. Therefore, the named block gets compiled only once. An anonymous block is a PL/SQL block that appears in a user's application and is neither named nor stored in the database. This block does not allow any mode of parameter. Anonymous block programs are effective in some situations. They are basically used when building scripts to seed data or perform one-time processing activities. They are also used when a user wants to nest activity in another PL/SQL block's execution section. Anonymous blocks are compiled each time they are executed.
Which of the following statements is true about a relational database?
It is difficult to extend a relational database.
The standard user and application program interface to a relational database is Programming Language (PL).
It is a collection of data items organized as a set of formally-described tables.
It is a set of tables containing data fitted into runtime defined categories.
A relational database is a collection of data items organized as a set of formally-described tables from which data can be accessed or reassembled in many different ways without having to reorganize the database tables. Answer: B is incorrect. The standard user and application program interface to a relational database is the structured query language (SQL). Answer: A is incorrect. In addition to being relatively easy to create and access, a relational database has the important advantage of being easy to extend. Answer: D is incorrect. A relational database is a set of tables containing data fitted into predefined categories. Each table (which is sometimes called a relation) contains one or more data categories in columns. Each row contains a unique instance of data for the categories defined by the columns.
John works as a professional Ethical Hacker. He is assigned a project to test the security of He is working on the Linux operating system. He wants to sniff the we-are-secure network and intercept a conversation between two employees of the company through session hijacking. Which of the following tools will John use to accomplish the task?
IPChains
Tripwire
Hunt
Ethercap
In such a scenario, John will use Hunt which is capable of performing both the hacking techniques, sniffing and session hijacking. Answer: D is incorrect. Ethercap is a network sniffer and packet generator. It may be an option, but John wants to do session hijacking as well. Hence, he will not use Ethercap. Answer: A is incorrect. IPChains is a firewall. Answer: B is incorrect. Tripwire is a file and directory integrity checker.
Which of the following are HTML tags, used to create a table?
tags. The
|
