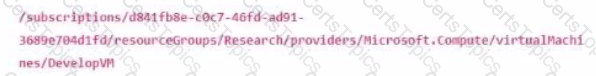
The Azure URI for the Develop VM is shown below. What will change in the notation when referencing the VM's OS disk?
A company using PaaS to host and develop their software application is experiencing a DOS attack. What challenge will a DFIR analyst experience when investigating this attack?
Which is a limitation when adding GPUs to Google cloud VMs?
Which AWS policy type specifies the maximum resource permissions for in organization or organizational unit (OU)?
An analyst successfully authenticated to Microsoft 365 using the following command. What would cause the analyst to be unable to search UAL events for a specific time period?
Ps> connect fxrhangeOnline userPrincipalName sysanalystatexanpteco.com
An investigator his successfully installed the ExchangeOnlineManagement module on their investigation system and is attempting to search a client's Microsoft 365 Unified Audit Log using PowerShell. PowerShell returns a "command not found" error each time they try to execute the Search-UnifiedAuditLog cmdlet. How should the investigator troubleshoot this issue?
Which AWS authentication method provides temporary, limited privilege credentials for 1AM users or federated users?
The attack technique "Access Kubelet API" falls under which Mitre ATT&CK tactic?
Microsoft.Key Vault is an example of which component of Azure's structure?
An investigator is evaluating a client's Microsoft 365 deployment using the web portals and has identified that the Purview compliance portal states that the Unified Audit Logs are not enabled. Based on the additional Information gathered below, what is most likely the cause of this configuration message?
Subscription creation date: December 4, 2021 Number of administrators: 2 Number of non-administrative user accounts: 74 Last tenant administration change: December 4,2021
What is the example AWS data below an example of?

Access Kibana via and use the *ws-* index pattern. Use the time range 2021-03-0100:00 UTC to 2021 04 U 00:00 UTC. How many ec2 DescribMnstantp*; events were performed by the root user?
Use Kibana to analyze the Azure AD sign-in logs in the azure-* index. On March 31st, 2021, what is the timestamp of the earliest failed login attempt for the accountdcr0ss5pymtechlabs.com?
ViewVM
At what organizational level are EC2 services managed by customers?
Which AW5 1AM policy element indicates the API that is in scope?
An analyst investigating a malicious application determines that it runs using AVVS Lambda. What challenge will the analyst likely encounter during the Investigation?
A client was responsible for their environment's OS, then they delegated this responsibility to their cloud provider. Which of the following migrations could describe this scenario?
What Amazon EC2 instance prefix should be monitored to detect potential crypto mining?
Which statement describes a zld.metal EC2 instance?
Which cloud service provider produces sampled flow logs?
What is shown in the screenshot?
At what point of the OAuth delegation process does the Resource Owner approve the scope of access to be allowed?
Using the SOF-ELK instance at 10.0.1.7:5601, inspect the netflow logs related to the ip 5.62.19.62.
Which of the ports seen in the netflow logs associated with the ip 5.62.19.62 has the lowest count?
Hint: Use a wide time frame such as 20 years to ensure all the relevant data is in the scope.
An engineer is looking for the log of API calls recorded by CloudTrail for the past 6 months. Where should they look for the oldest data?