You are configuring the failover settings on a FortiGate active-passive SDN connector solution in Microsoft Azure. Which two mandatory settings are required after the initial deployment? (Choose two)
What is the main advantage of using SD-WAN Transit Gateway Connect over traditional SD-WAN?
An administrator is looking for a solution that can provide insight into users and data stored in major SaaS applications in the multicloud environment Which product should the administrator deploy to have secure access to SaaS applications?
You are automating configuration changes on one of the FortiGate VMS using Linux Red Hat Ansible.
How does Linux Red Hat Ansible connect to FortiGate to make the configuration change?
Refer to the exhibit.
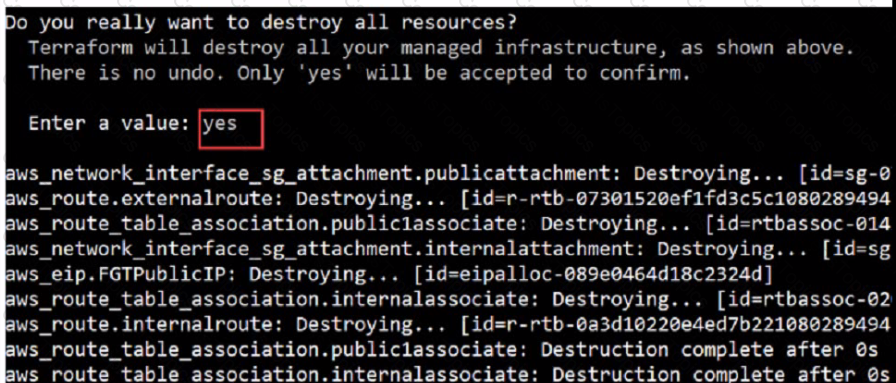
What would be the impact of confirming to delete all the resources in Terraform?
A Network security administrator is searching for a solution to secure traffic going in and out of the container infrastructure.
In which two ways can Fortinet container security help secure container infrastructure? (Choose two.)
Refer to the exhibit
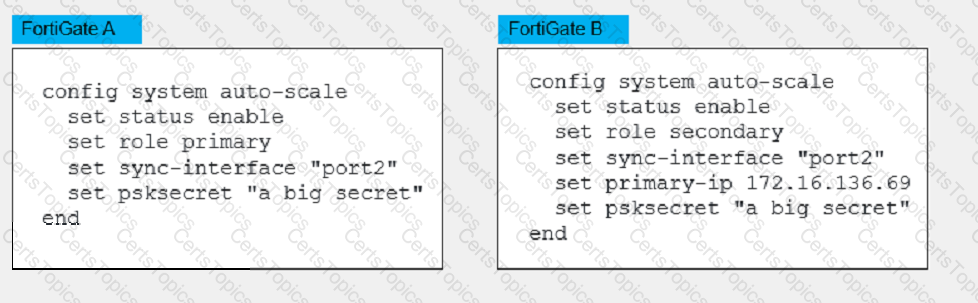
An administrator deployed an HA active-active load balance sandwich in Microsoft Azure. The setup requires configuration synchronization between devices-
What are two outcomes from the configured settings? (Choose two.)
Refer to the exhibit.
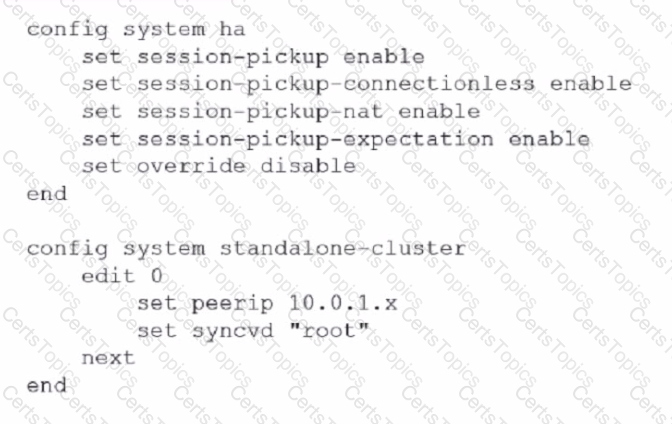
You deployed an HA active-active load balance sandwich with two FortiGate VMs in Microsoft Azure.
After the deployment, you prefer to use FGSP to synchronize sessions, and allow asymmetric return traffic In the environment, FortiGate port 1 and port 2 are facing external and internal load balancers respectively
What IP address must you use in the peerip configuration?
Your goal is to deploy resources in multiple places and regions in the public cloud using Terraform.
What is the most efficient way to deploy resources without changing much of the Terraform code?
Refer to the exhibit

You deployed an HA active-passive FortiGate VM in Microsoft Azure.
Which two statements regarding this particular deployment are true? (Choose two.)
Your administrator instructed you to deploy an Azure vWAN solution to create a connection between the main company site and branch sites to the other company VNETs.
What are the two best connection solutions available between your company headquarters, branch sites, and the Azure vWAN hub? (Choose two.)
You are adding a new spoke to the existing transit VPC environment using the AWS Cloud Formation template. Which two components must you use for this deployment? (Choose two.)
What kind of underlying mechanism does Transit Gateway Connect use to send traffic from the virtual private cloud (VPC) to the transit gateway?
Which two Amazon Web Services (AWS) features do you use for the transit virtual private cloud (VPC) automation process to add new spoke N/PCs? (Choose two )
What are two main features in Amazon Web Services (AWS) network access control lists (ACLs)? (Choose two.)
Refer to Exhibit:
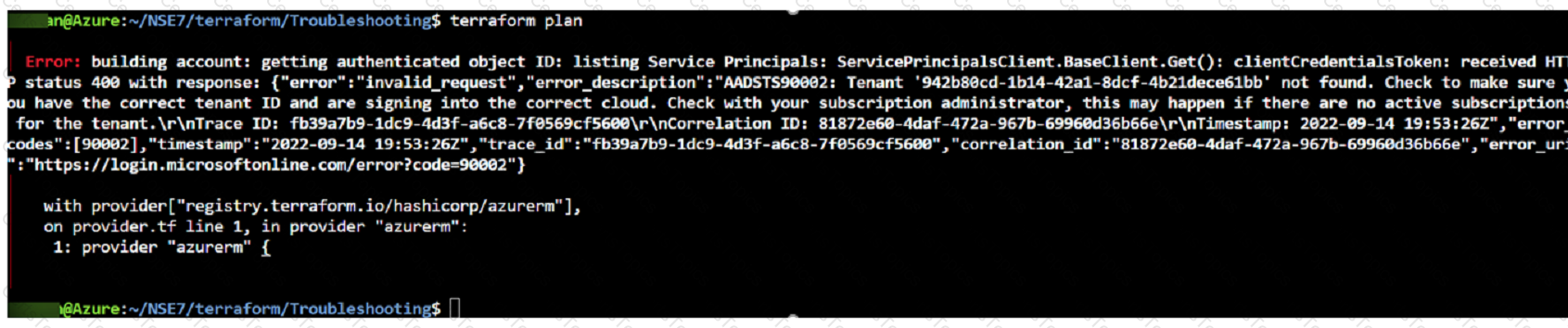
After the initial Terraform configuration in Microsoft Azure, the terraform plan command is run Which two statements about running the plan command are true? (Choose two.)
Which statement about immutable infrastructure in automation is true?