Which two agents can validate endpoint compliance transparently to the end user? (Choose two.)
Which two device classification options can register a device automatically and transparently to the end user? (Choose two.)
View the output.
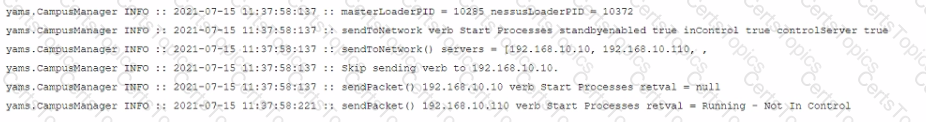
Examine the communication between a primary FortiNAC (192.168.10.10) and a secondary FortiNAC (192.166.10.110) configured as an HA pair What is the current state of the FortiNAC HA pair?
In which view would you find who made modifications to a Group?
With enforcement for network access policies and at-risk hosts enabled, what will happen if a host matches a network access policy and has a state of "at risk"?
Which two policy types can be created on a FortiNAC Control Manager? (Choose two.)
Refer to the exhibit.
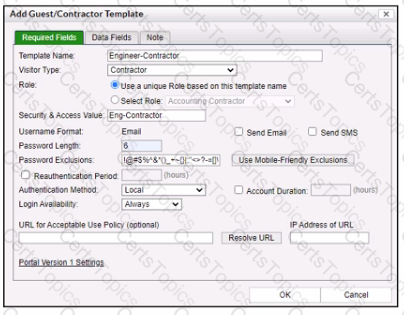
When a contractor account is created using this template, what value will be set in the accounts Rote field?
Refer to the exhibit.
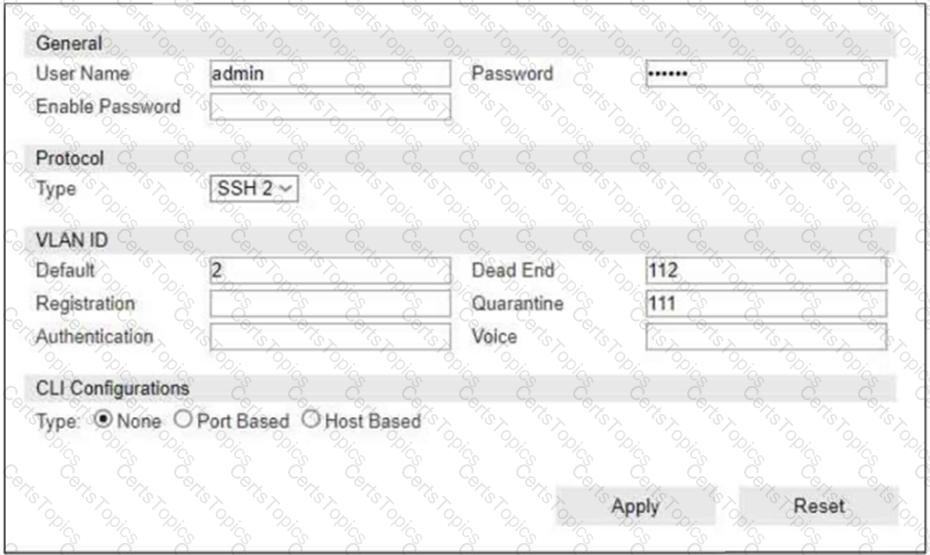
If you are forcing the registration of unknown (rogue) hosts, and an unknown (rogue) host connects to a port on the switch, what occurs?
Which connecting endpoints are evaluated against all enabled device profiling rules?
When FortiNAC is managing VPN clients connecting through FortiGate. why must the clients run a FortiNAC agent?
Which three of the following are components of a security rule? (Choose three.)
Which system group will force at-risk hosts into the quarantine network, based on point of connection?
Where are logical network values defined?
Which three circumstances trigger Layer 2 polling of infrastructure devices? (Choose three.)
Where do you look to determine when and why the FortiNAC made an automated network access change?
In a wireless integration, what method does FortiNAC use to obtain connecting MAC address information?
What capability do logical networks provide?