The password upload utility must run from the CPM server
Which tools are used during a CPM renaming process?
A new domain controller has been added to your domain. You need to ensure the CyberArk infrastructure can use the new domain controller for authentication.
Which locations must you update?
A new HTML5 Gateway has been deployed in your organization.
Where do you configure the PSM to use the HTML5 Gateway?
Which parameters can be used to harden the Credential Files (CredFiles) while using CreateCredFile Utility? (Choose three.)
You are installing HTML5 gateway on a Linux host using the RPM provided. After installing the Tomcat webapp, what is the next step in the installation process?
For an account attached to a platform that requires Dual Control based on a Master Policy exception, how would you configure a group of users to access a password without approval.
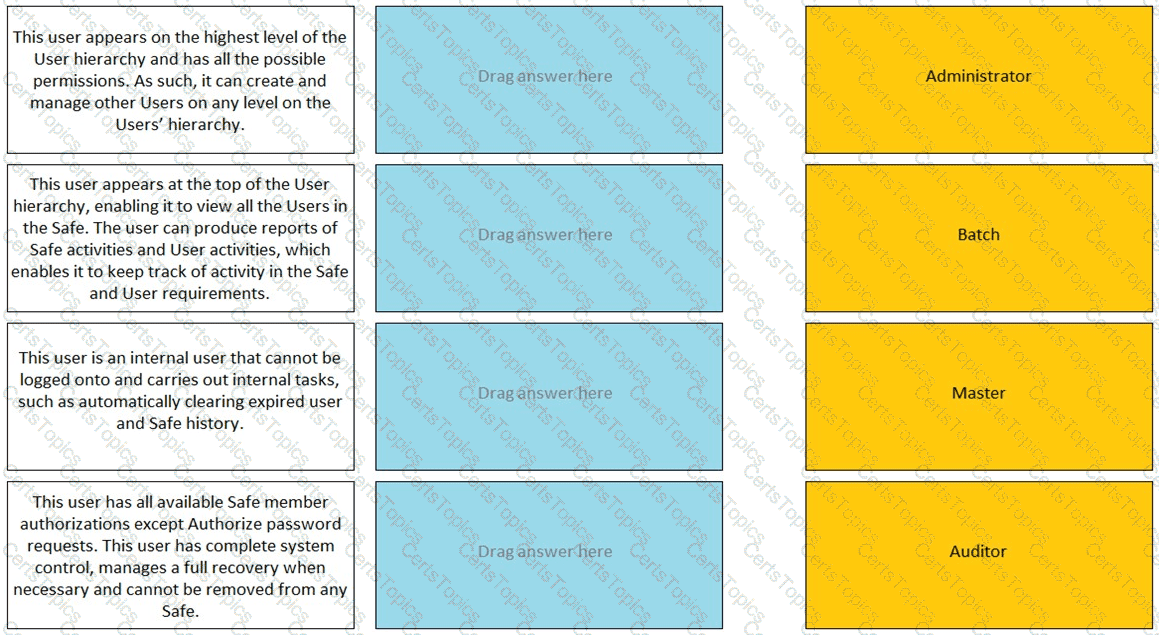
Match the built-in Vault User with the correct definition.
All of your Unix root passwords are stored in the safe UnixRoot. Dual control is enabled for some of the accounts in that safe. The members of the AD group UnixAdmins need to be able to use the show, copy, and connect buttons on those passwords at any time without confirmation. The members of the AD group Operations Staff need to be able to use the show, copy and connect buttons on those passwords on an emergency basis, but only with the approval of a member of Operations Managers never need to be able to use the show, copy or connect buttons themselves.
Which safe permission do you need to grant Operations Staff? Check all that apply.
You need to move a platform from using PMTerminal to using Terminal Plugin Controller (TPC) What must you do?
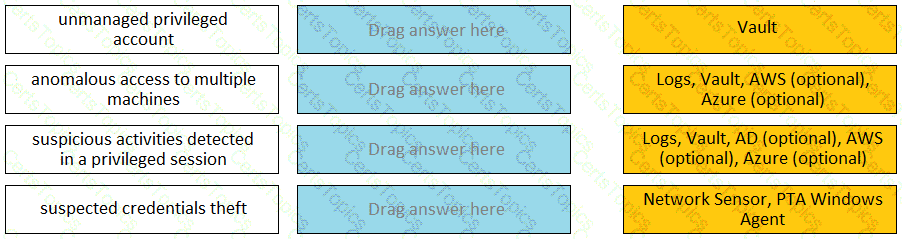
Match each PTA alert category with the PTA sensors that collect the data for it.
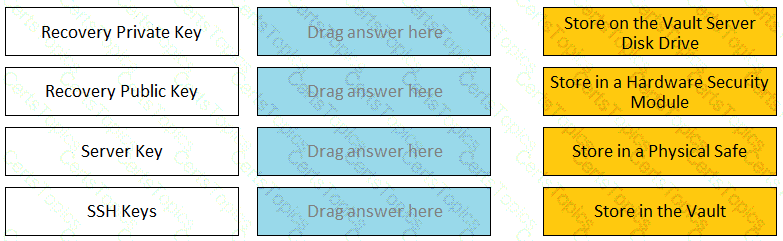
Match each key to its recommended storage location.
CyberArk user Neil is trying to connect to the Target Linux server 192.168.1.64 using a domain account ACME/linuxuser01 on Domain Acme.corp using PSM for SSH server 192.168.65.145. What is the correct syntax?
In addition to bit rate and estimated total duration of recordings per day, what is needed to determine the amount of storage required for PSM recordings?
You are creating a new Rest API user that utilizes CyberArk Authentication.
What is a correct process to provision this user?
Secure Connect provides the following. Choose all that apply.
Which step is required to register a Vault manually in Amazon Web Services using CAVaultManager?
In your organization the “click to connect” button is not active by default.
How can this feature be activated?
A user requested access to view a password secured by dual-control and is unsure who to contact to expedite the approval process. The Vault Admin has been asked to look at the account and identify who can approve their request.
What is the correct location to identify users or groups who can approve?
Users can be resulted to using certain CyberArk interfaces (e.g.PVWA or PACLI).
The Password upload utility can be used to create safes.
Accounts Discovery allows secure connections to domain controllers.
To ensure all sessions are being recorded, a CyberArk administrator goes to the master policy and makes configuration changes.
Which configuration is correct?
You are responsible for installing a CPM.
Which Vault authorizations will your CyberArk user need to install the CPM?
Assuming a safe has been configured to be accessible during certain hours of the day, a Vault Admin may still access that safe outside of those hours.
Which of the following Privileged Session Management solutions provide a detailed audit log of session activities?
Which is the primary purpose of exclusive accounts?
Which components support fault tolerance.
You are creating a shared safe for the help desk.
What must be considered regarding the naming convention?
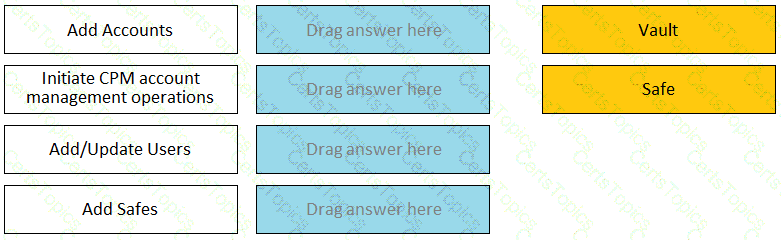
Match each permission to where it can be found.
Which components can connect to a satellite Vault in distributed Vault architecture?
The System safe allows access to the Vault configuration files.
A newly created platform allows users to access a Linux endpoint. When users click to connect, nothing happens.
Which piece of the platform is missing?
Which SMTP address can be set on the Notification Settings page to re-invoke the ENE setup wizard after the initial Vault installation.
You received a notification from one of your CyberArk auditors that they are missing Vault level audit permissions. You confirmed that all auditors are missing the Audit Users Vault permission.
Where do you update this permission for all auditors?
A logon account can be specified in the platform settings.
You have associated a logon account to one your UNIX cool accounts in the vault. When attempting to [b]change [/b] the root account’s password the CPM will…..
Which report shows the accounts that are accessible to each user?
In accordance with best practice, SSH access is denied for root accounts on UNIX/LINUX system. What is the BEST way to allow CPM to manage root accounts.
Which of the following components can be used to create a tape backup of the Vault?
When on-boarding account using Accounts Feed, Which of the following is true?
A Logon Account can be specified in the Master Policy.
What is a prerequisite step before CyberArk can be configured to support RADIUS authentication?
Due to network activity, ACME Corp’s PrivateArk Server became active on the OR Vault while the Primary Vault was also running normally. All the components continued to point to the Primary Vault.
Which steps should you perform to restore DR replication to normal?
Which user(s) can access all passwords in the Vault?
CyberArk recommends implementing object level access control on all Safes.
Which pre-requisite step must be completed before installing a Vault?
Vault admins must manually add the auditors group to newly created safes so auditors will have sufficient access to run reports.
Which of the Following can be configured in the Master Poky? Choose all that apply.
When Dual Control is enabled a user must first submit a request in the Password Vault Web Access (PVWA) and receive approval before being able to launch a secure connection via PSM for Windows (previously known as RDP Proxy).
Which PTA sensors are required to detect suspected credential theft?
You have been asked to design the number of PVWAs a customer must deploy. The customer has three data centers with a distributed vault in each, requires high availability, and wants to use all vaults, at all times. How many PVWAs does the customer need?
Which of the following options is not set in the Master Policy?
Which parameter controls how often the CPM looks for accounts that need to be changed from recently completed Dual control requests.
In addition to disabling Windows services or features not needed for PVWA operations, which tasks does PVWA Hardening.ps1 perform when run?
A customer's environment three data centers, consisting of 5,000 servers in Germany, 10,000 servers in Canada, 1,500 servers in Singapore. You want to manage target servers and avoid complex firewall rules. How many CPM's should you deploy?
By default, members of which built-in groups will be able to view and configure Automatic Remediation and Session Analysis and Response in the PVWA?
Platform settings are applied to _________.
What is the maximum number of levels of authorization you can set up in Dual Control?
Your customer has five main data centers with one PVWA in each center under different URLs. How can you make this setup fault tolerant?
Which option in the PrivateArk client is used to update users' Vault group memberships?
Users are unable to launch Web Type Connection components from the PSM server. Your manager asked you to open the case with CyberArk Support.
Which logs will help the CyberArk Support Team debug the issue? (Choose three.)
A user is receiving the error message “ITATS006E Station is suspended for User jsmith” when attempting to sign into the Password Vault Web Access (PVWA). Which utility would a Vault administrator use to correct this problem?
When creating Distributed Vault environment architecture, what is the maximum number of Vault servers that can be deployed''
Which of these accounts onboarding methods is considered proactive?