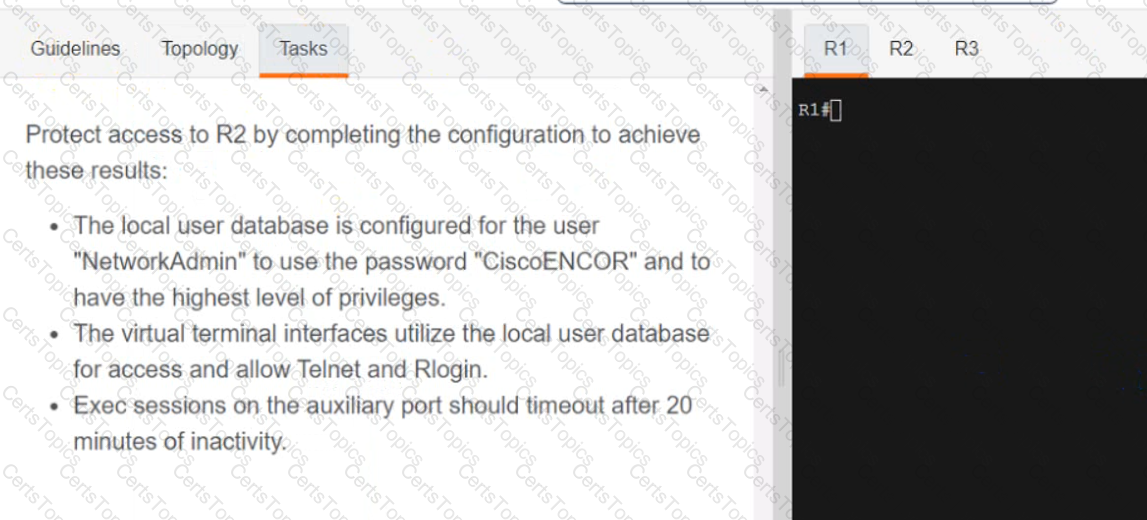
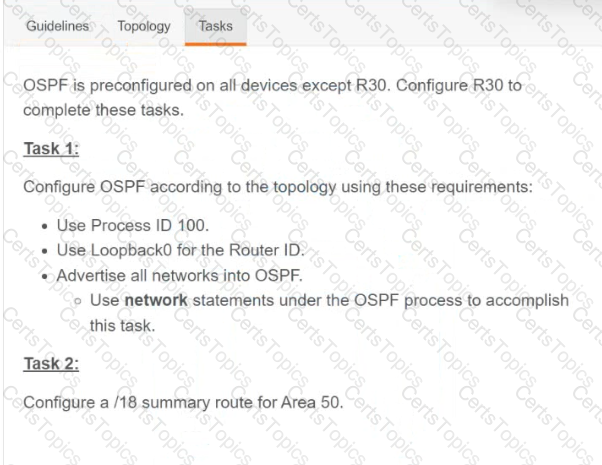
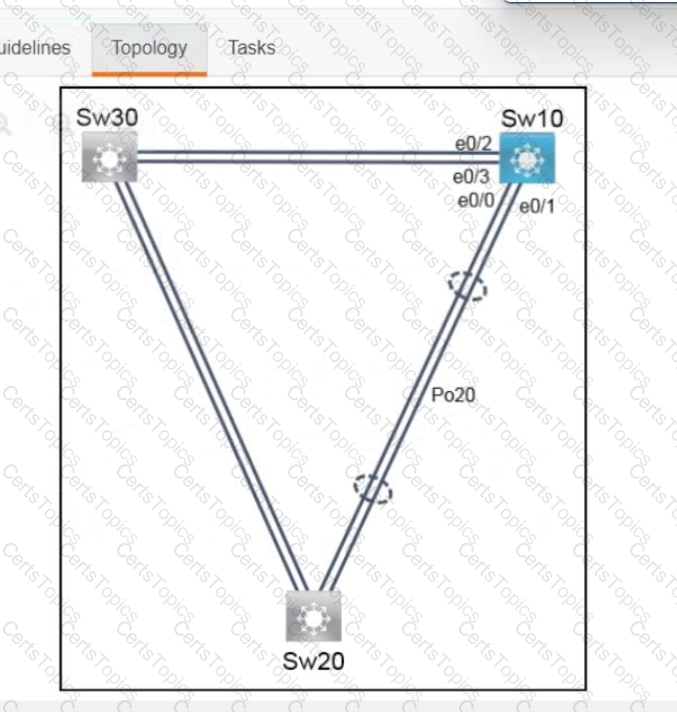
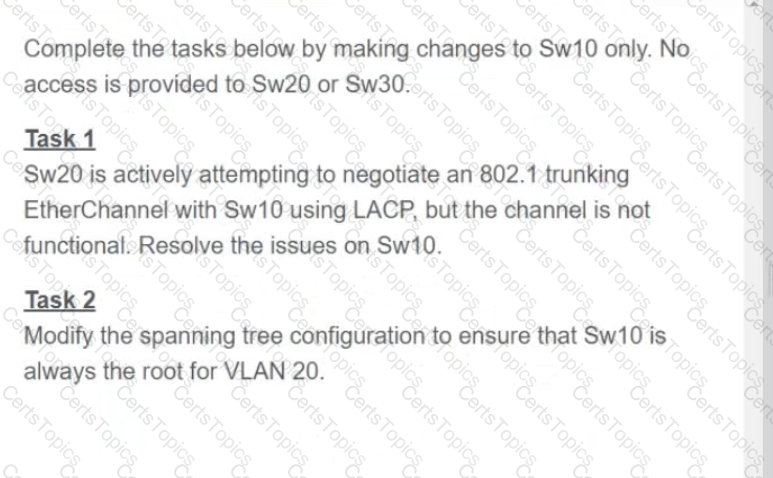
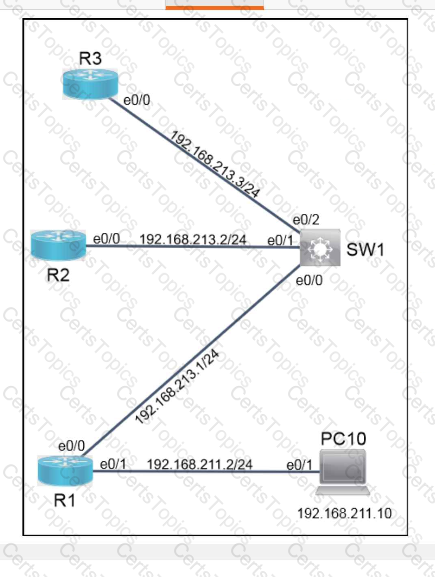
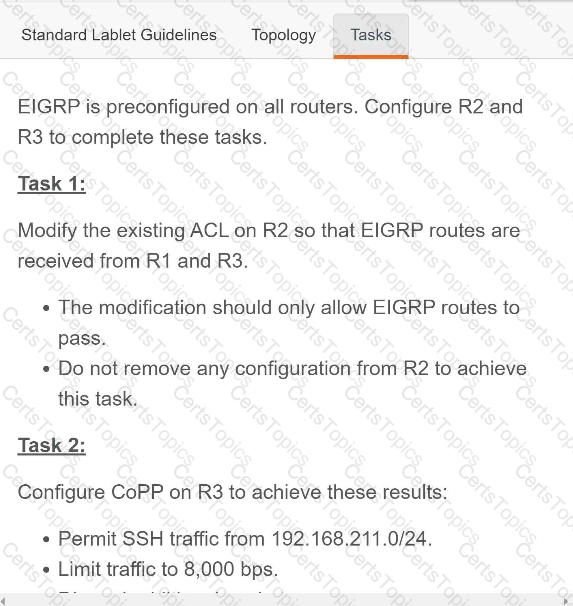
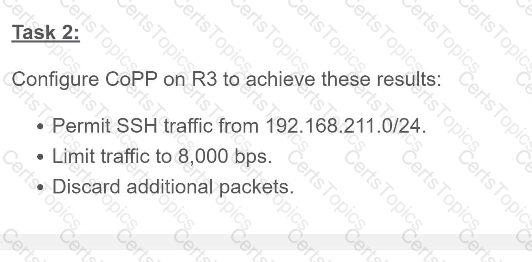
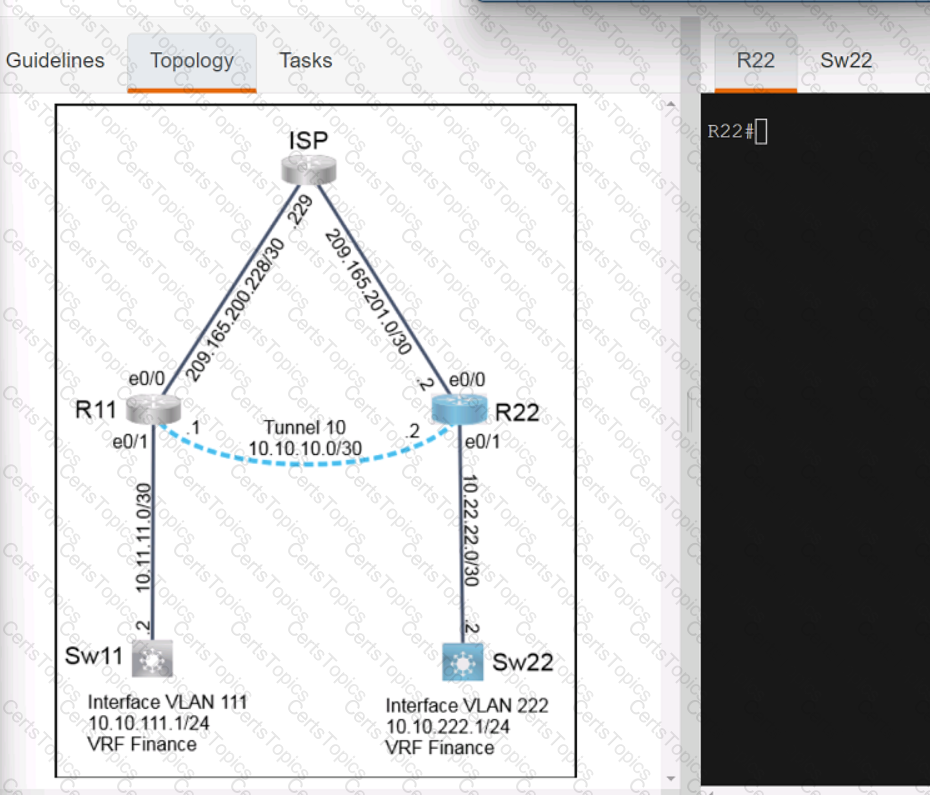
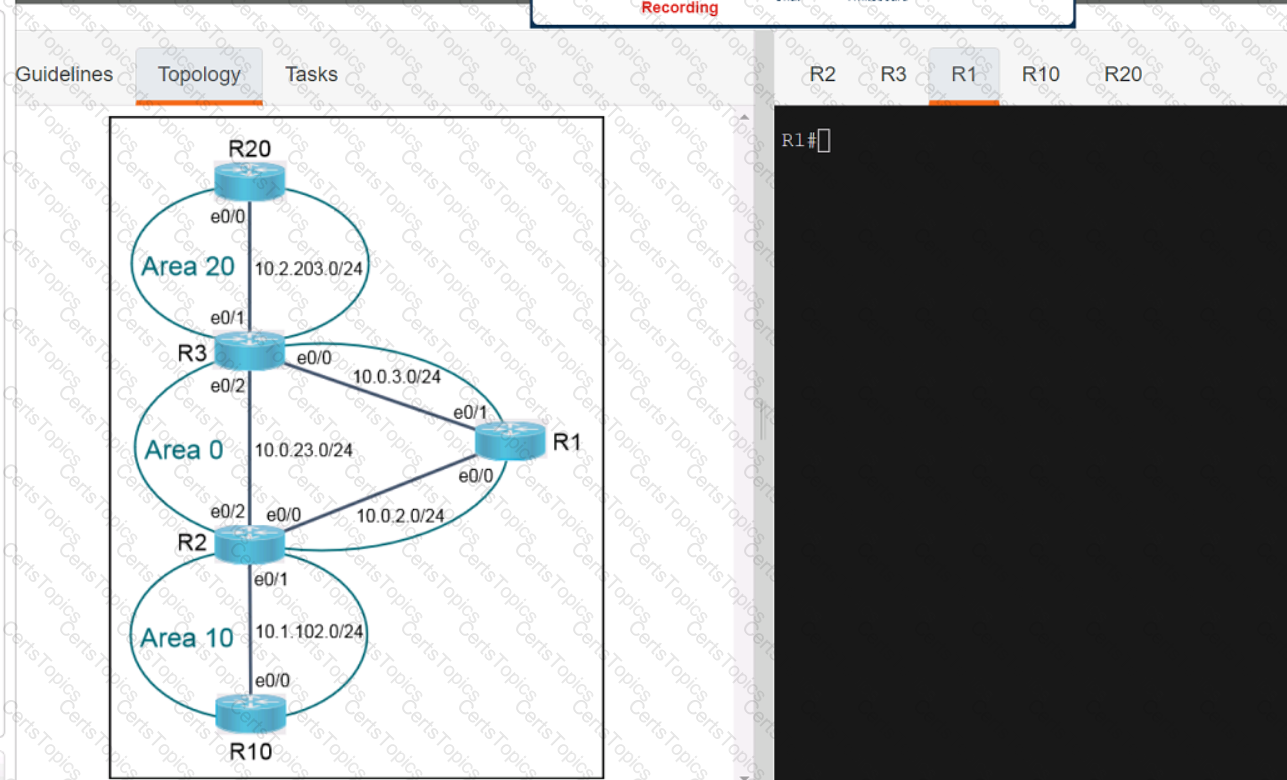
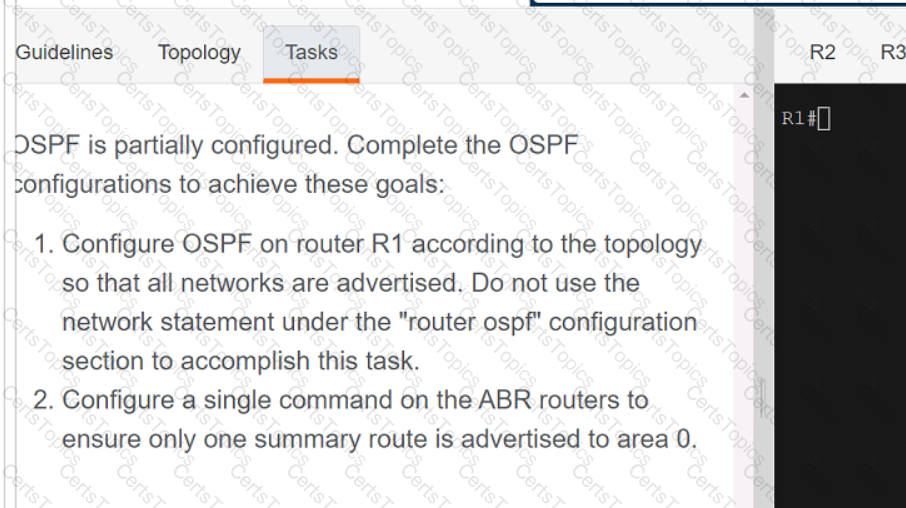
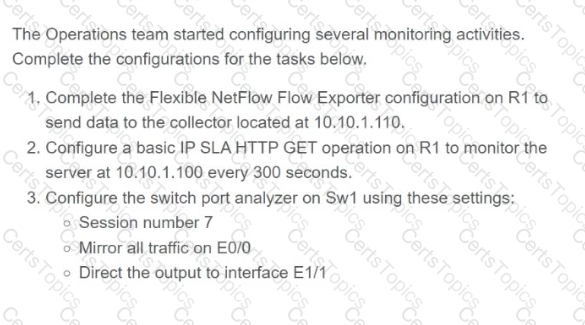
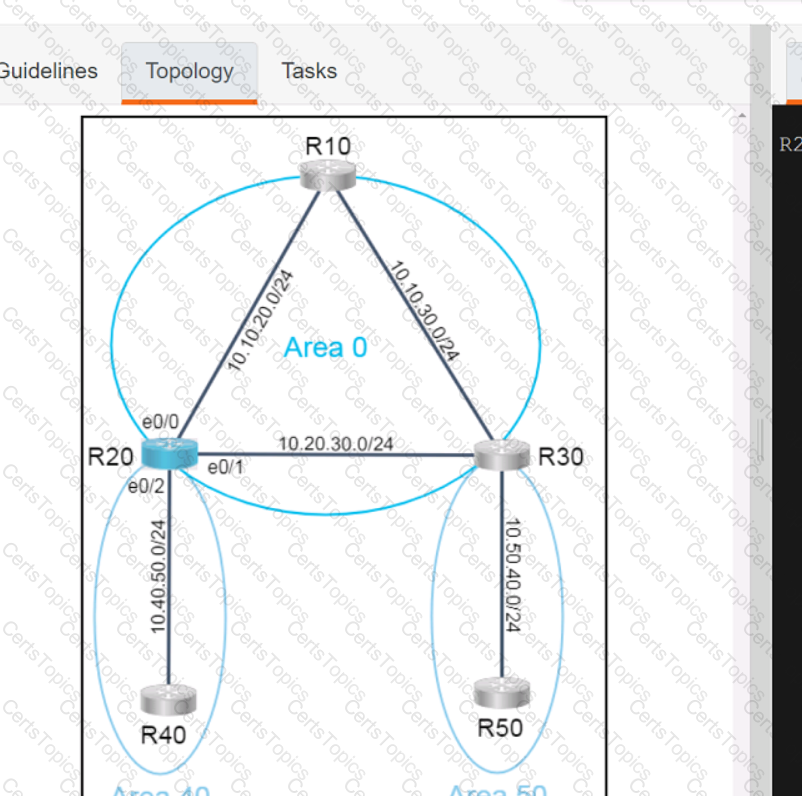
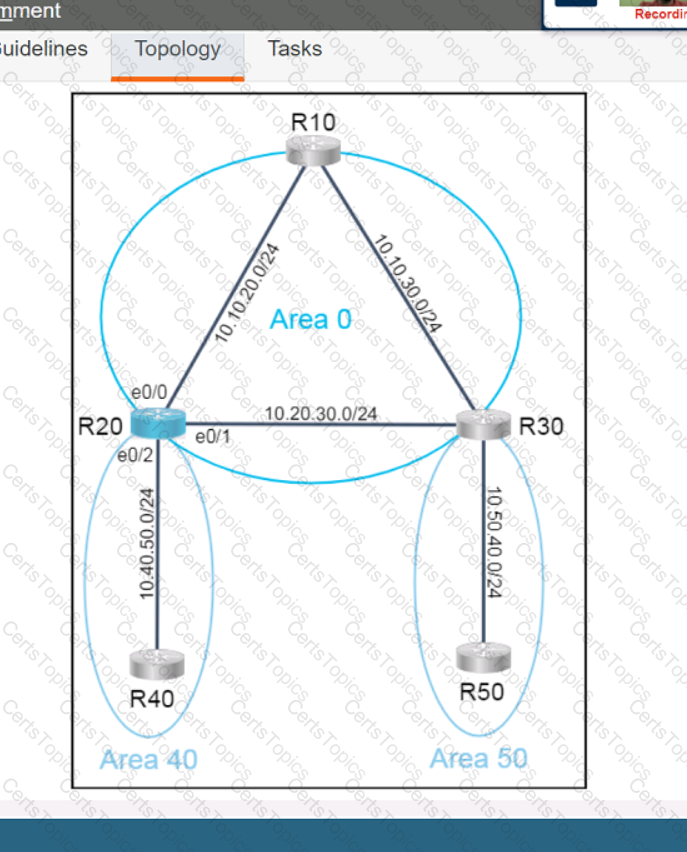
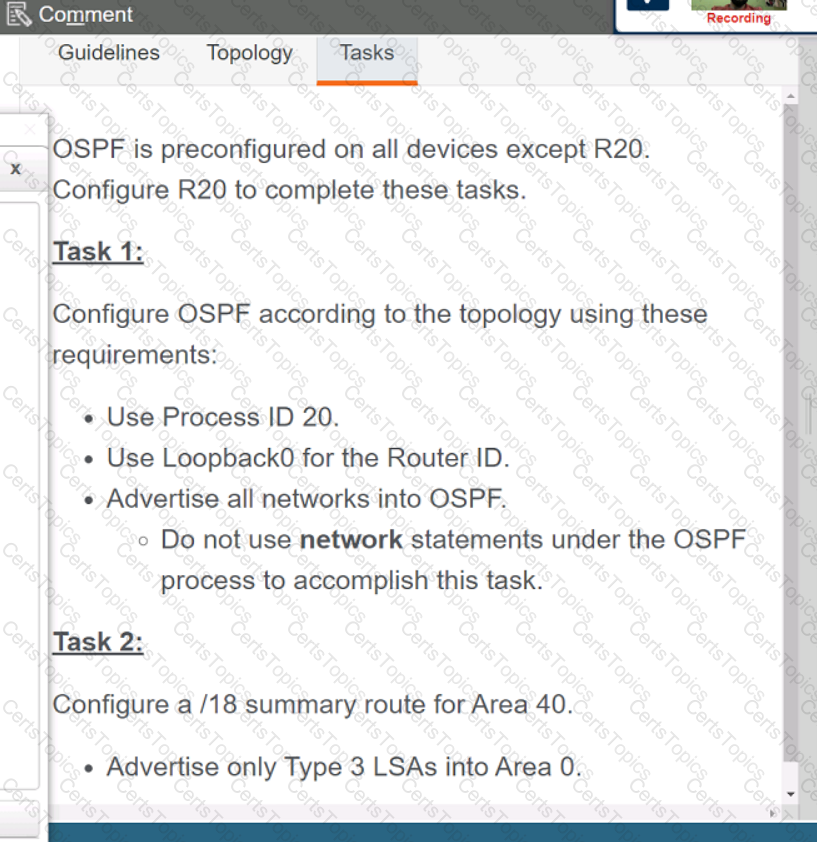
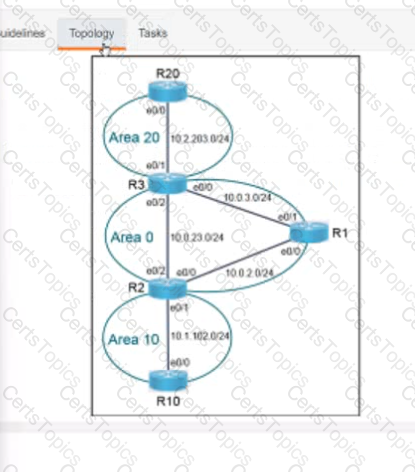
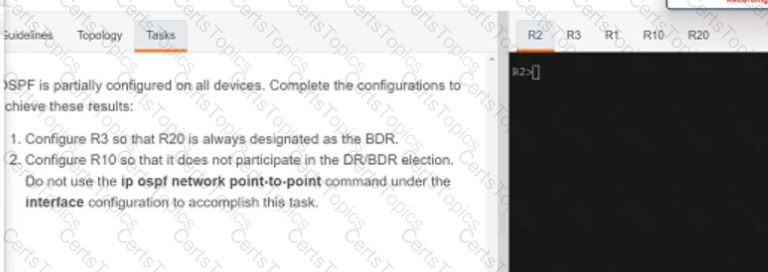
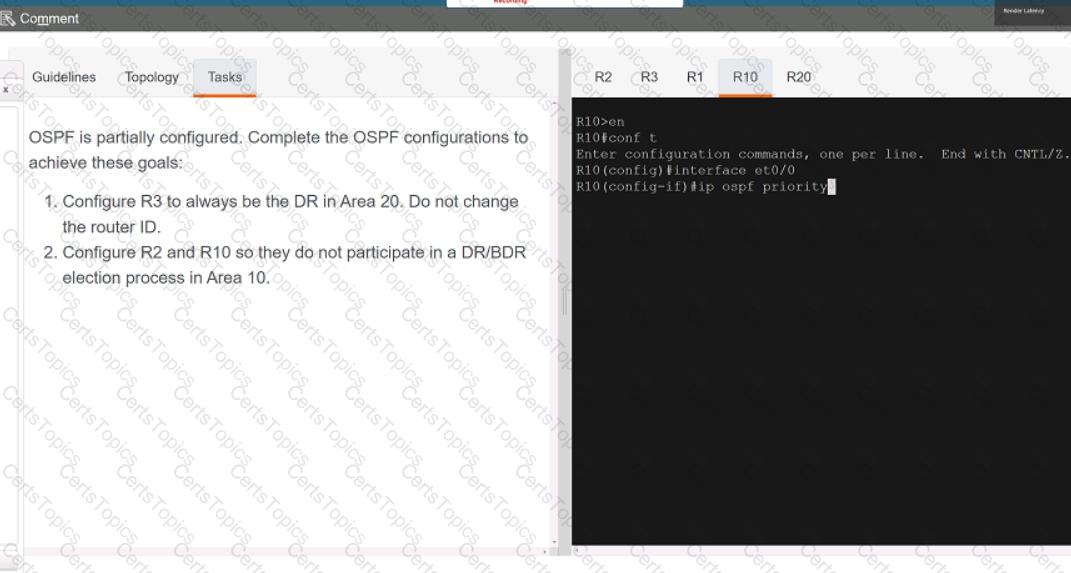
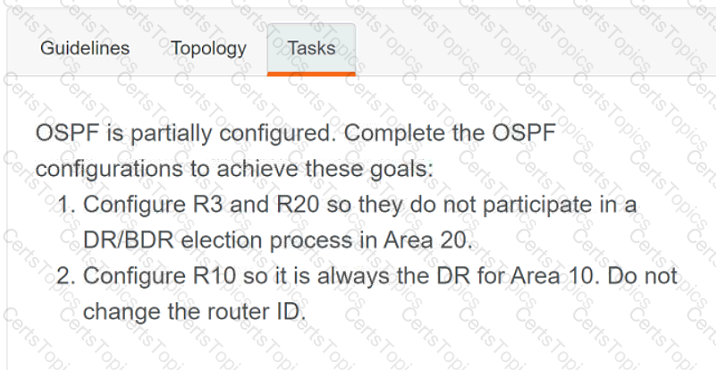
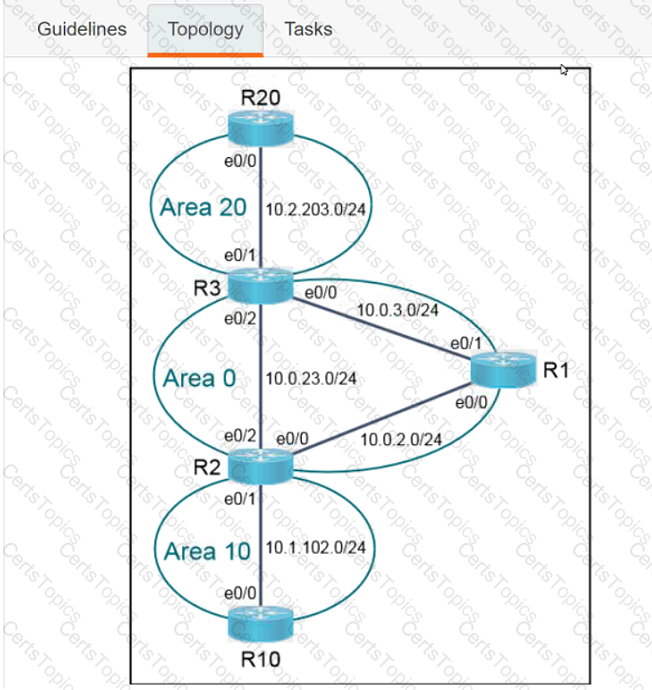
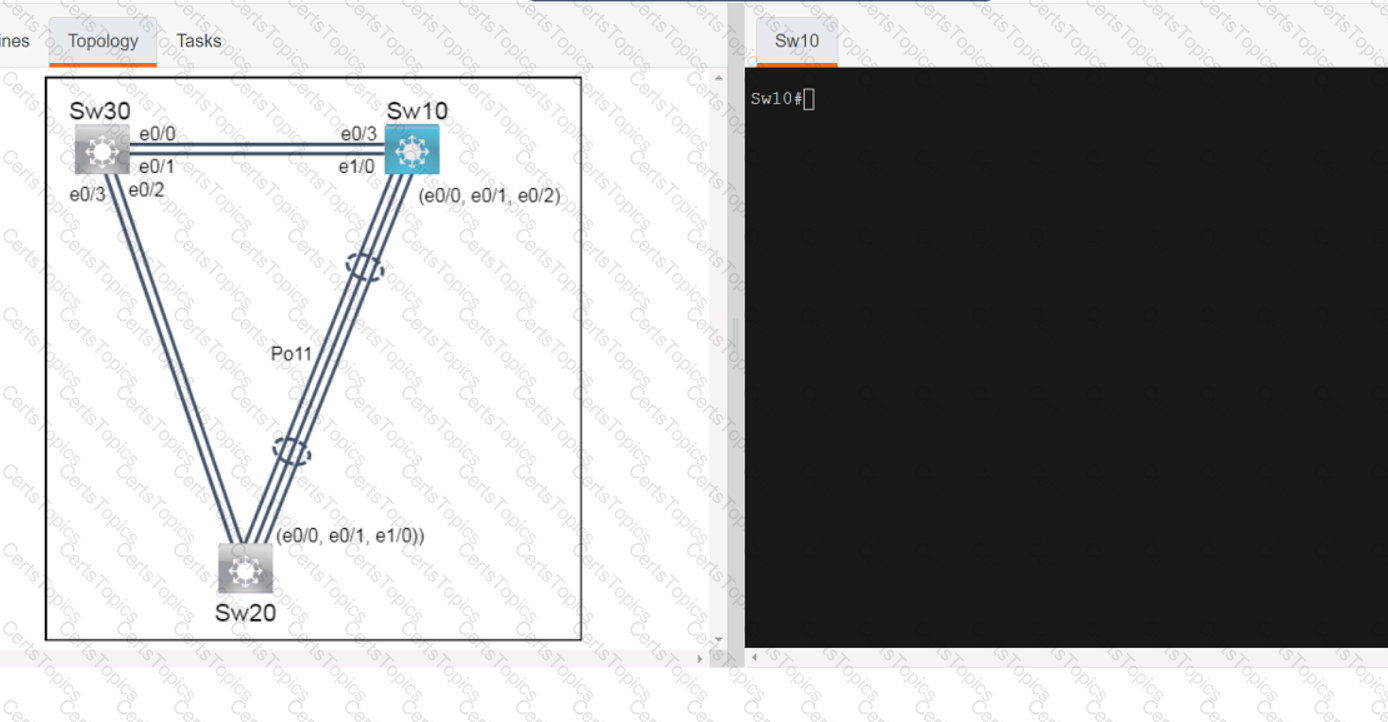
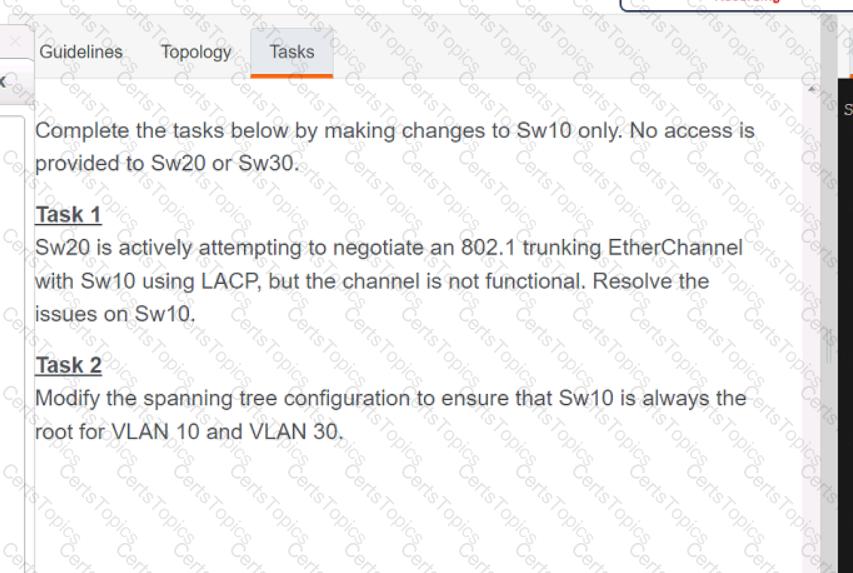
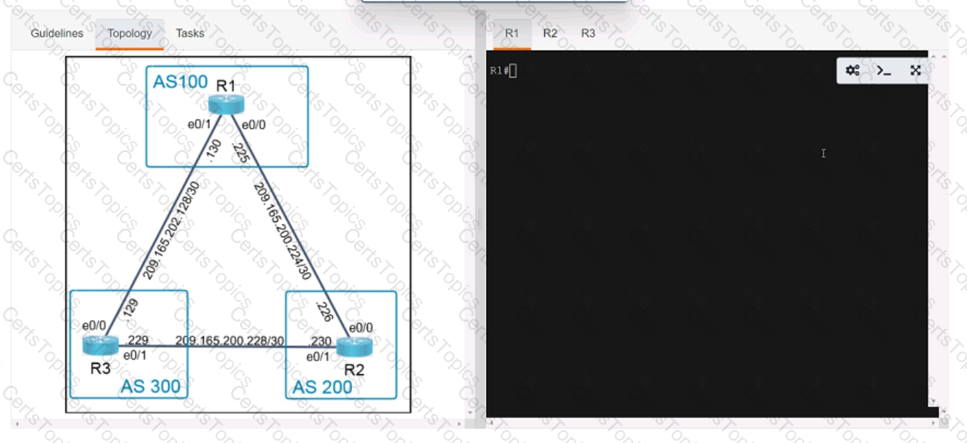
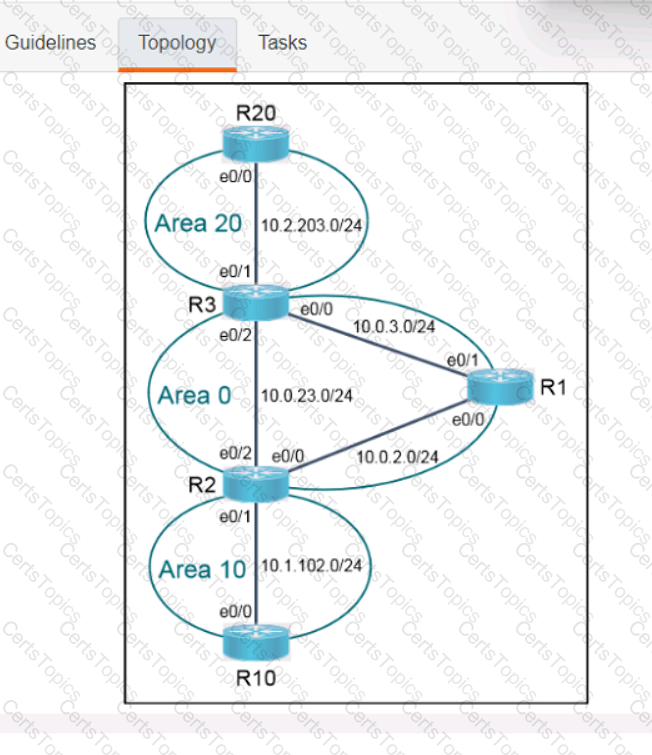
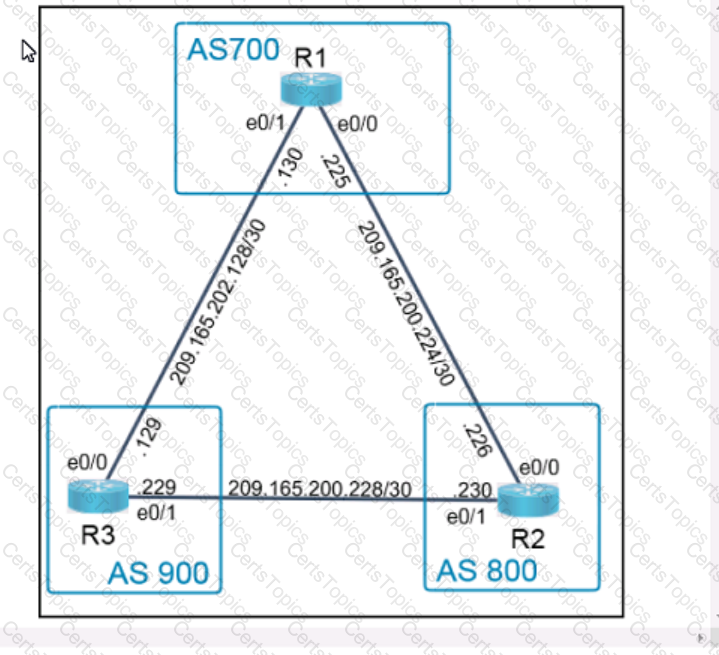
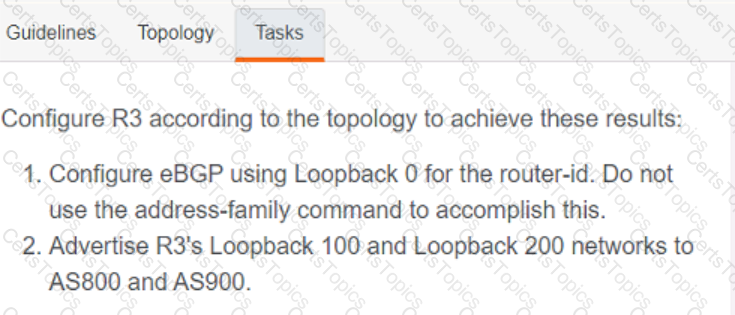
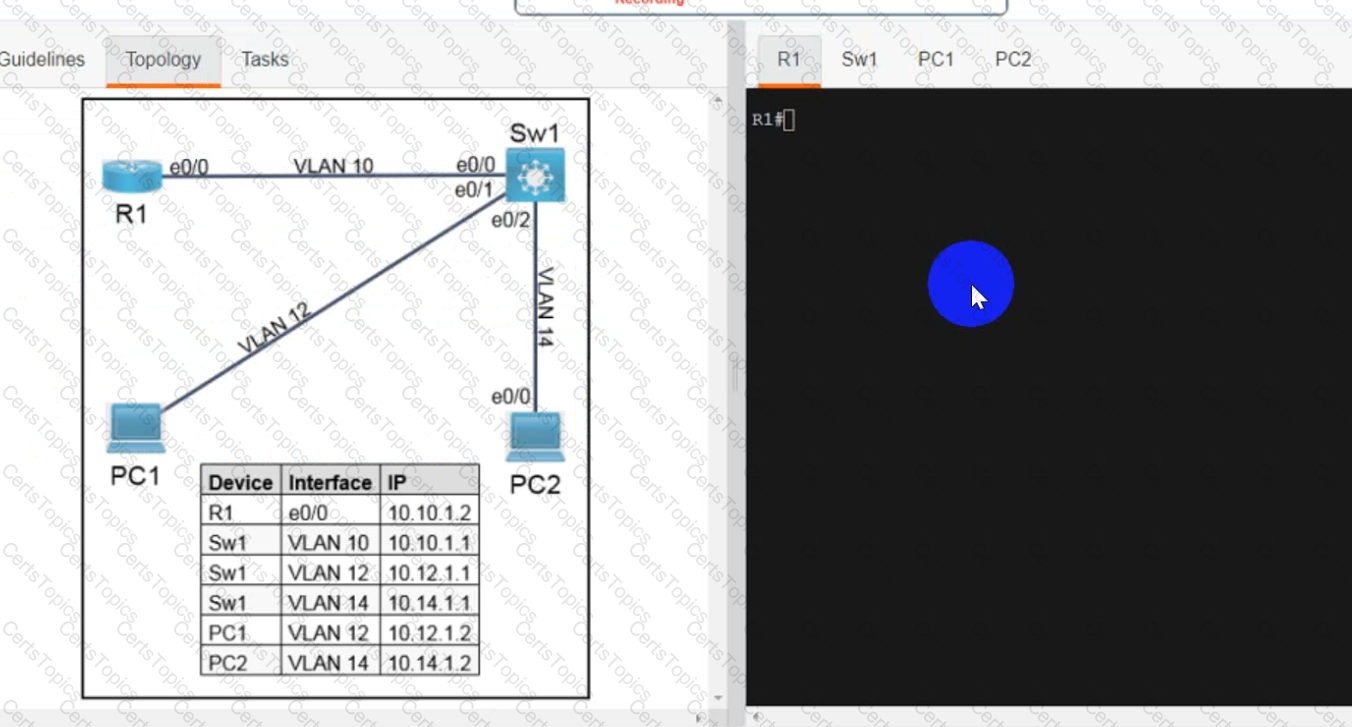
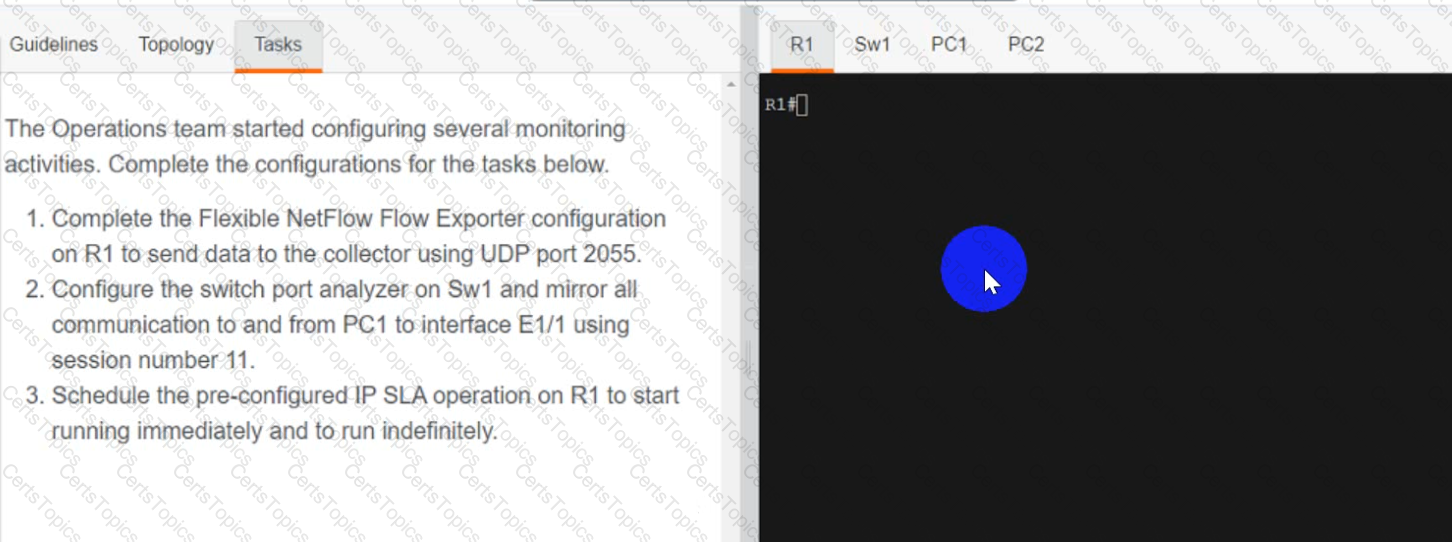
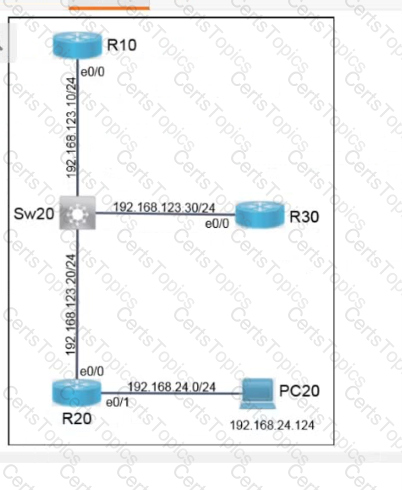
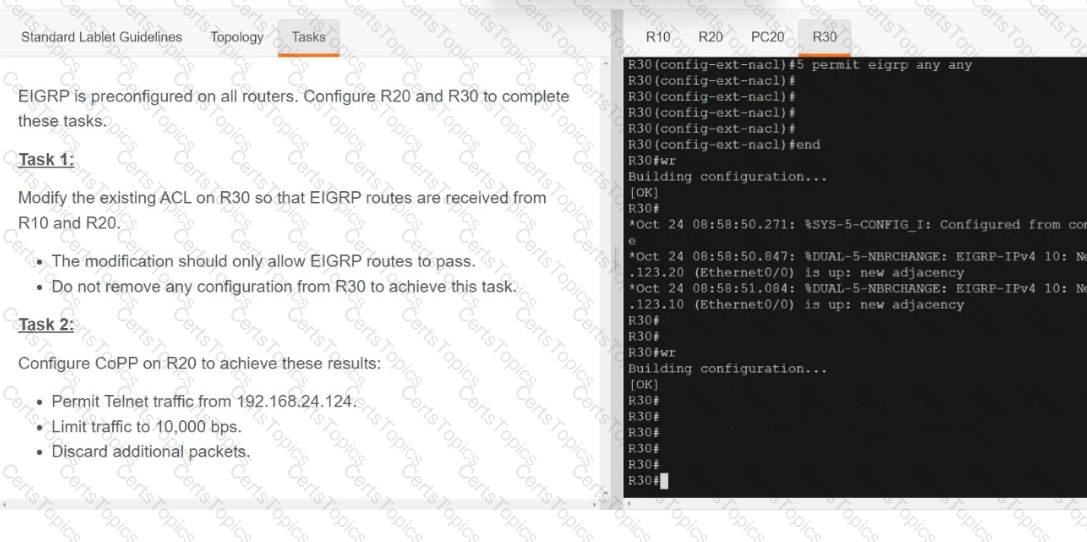
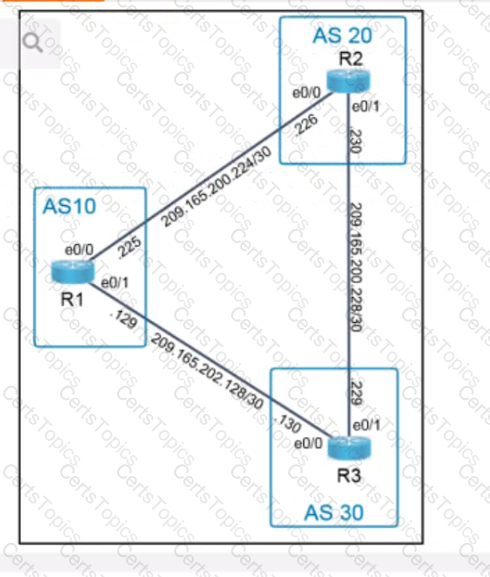
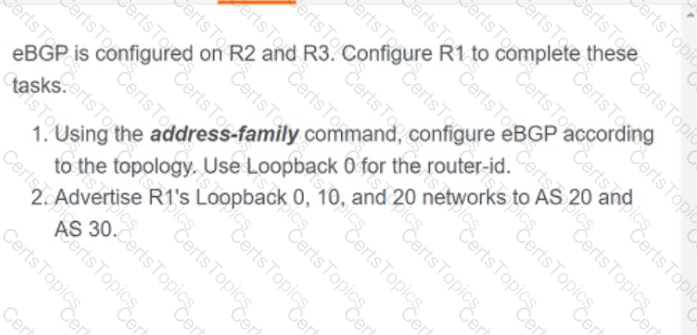
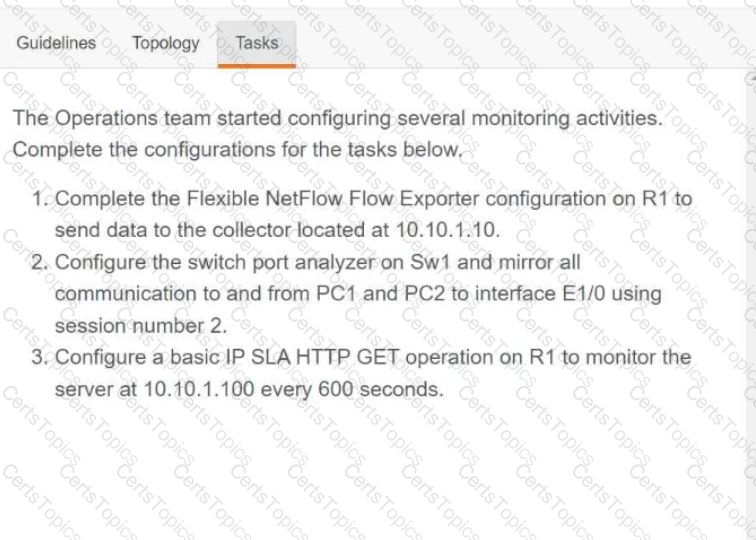
A script contains the statement white loop != 999 ’ Which value terminates the loop?
What is the purpose of data modeling languages?
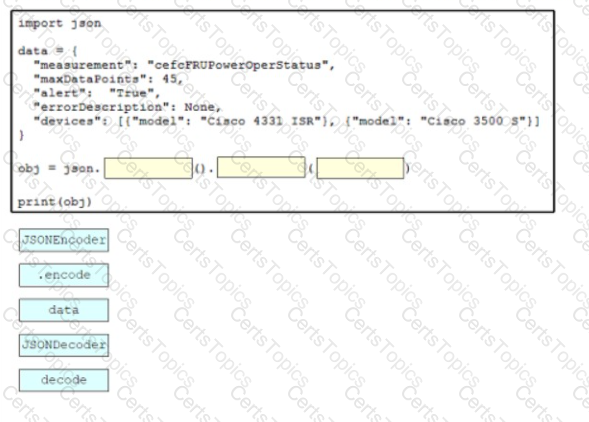
Drag and drop the code snippets from the bottom onto the blanks in the script to convert a Python object into a JSON string. Not all options are used
Which data is properly formatted with JSON?

An engineer is configuring RADIUS-Based Authentication with EAP. MS-CHAPv2 is configured on a client device. Which outer method protocol must be configured on the ISE to support this authentication type?
Which solution simplifies management of secure access to network resources?
Which method ensures the confidentiality of data exchanged over a REST API?
What is a characteristic of VRRP?
What is used by vManage to interact with Cisco SD-WAN devices in the fabric?
An engineer is reviewing a PCAP file that contains a packet capture of a four-way handshake exchange between a client and AP using WPA2 Enterprise Which EAPOL message validates and confirms that the client device has successfully Installed the GTK?
To support new clients in the environment, an engineer must enable Fast Transition on the corporate WLAN. Which command must be applied on a Cisco Catalyst 9800 Series WLC?
How does SSO work with HSRP to minimize network disruptions?
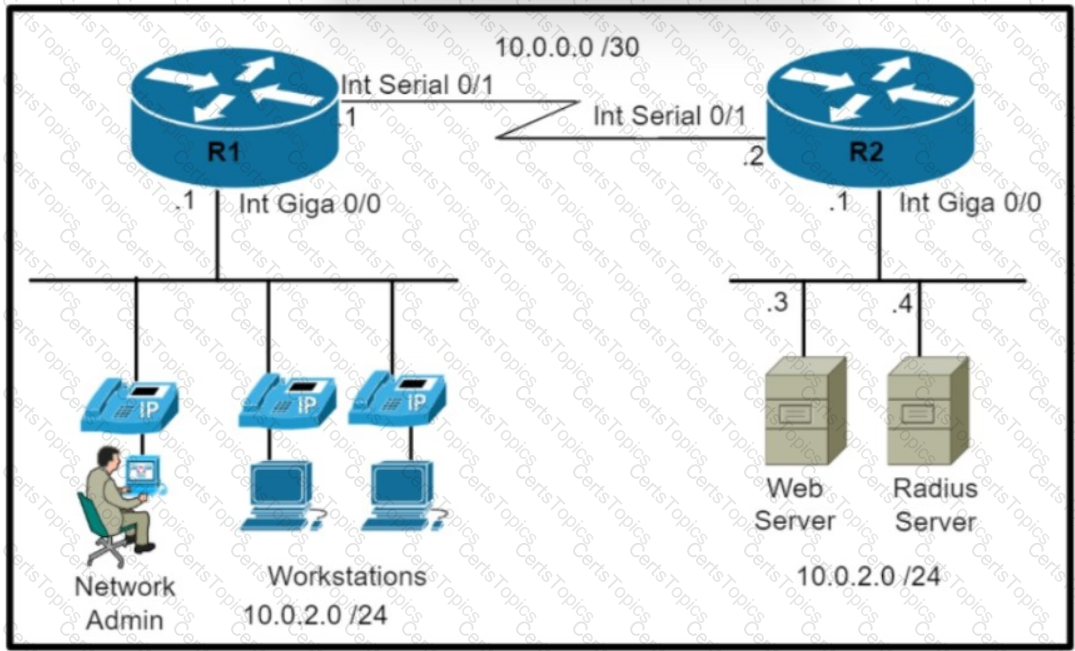
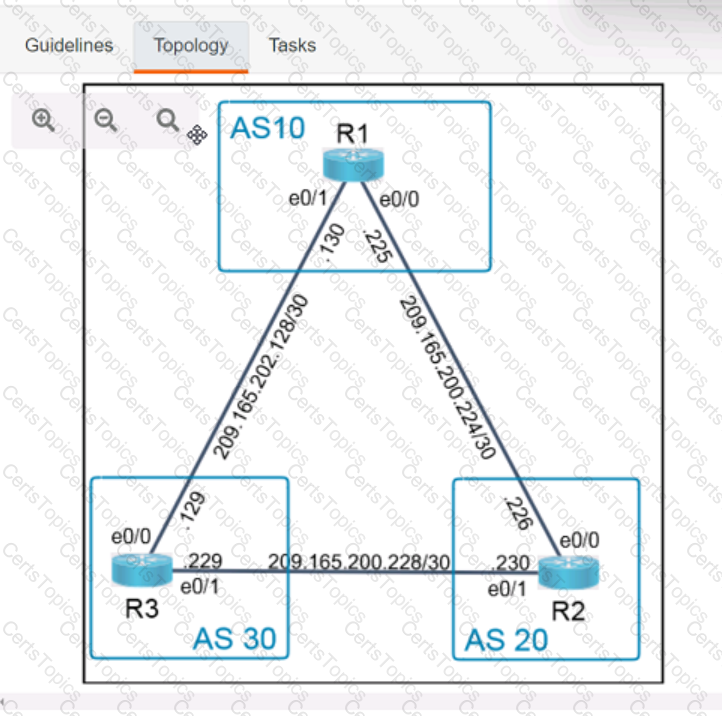
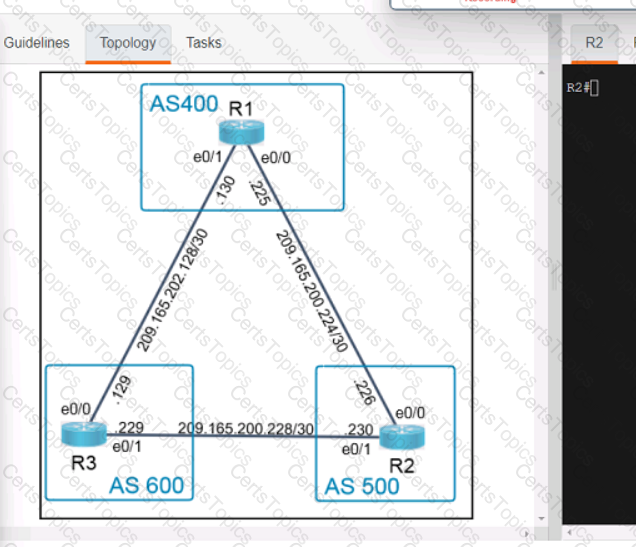
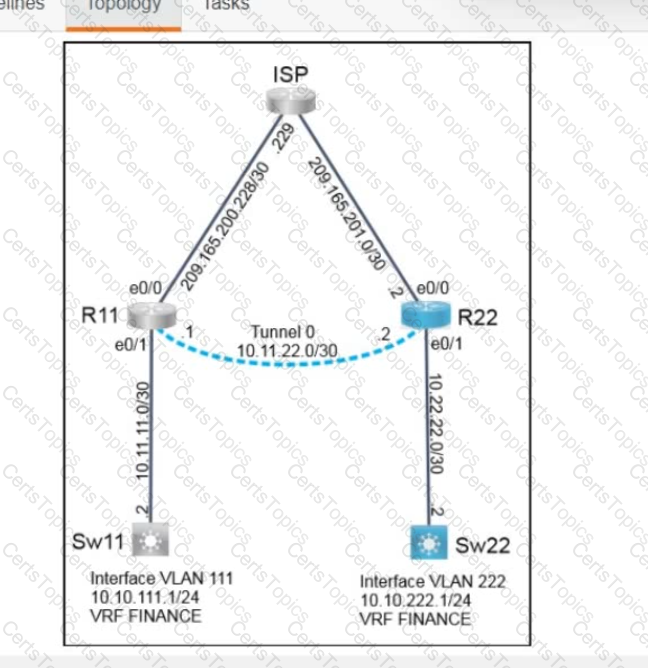
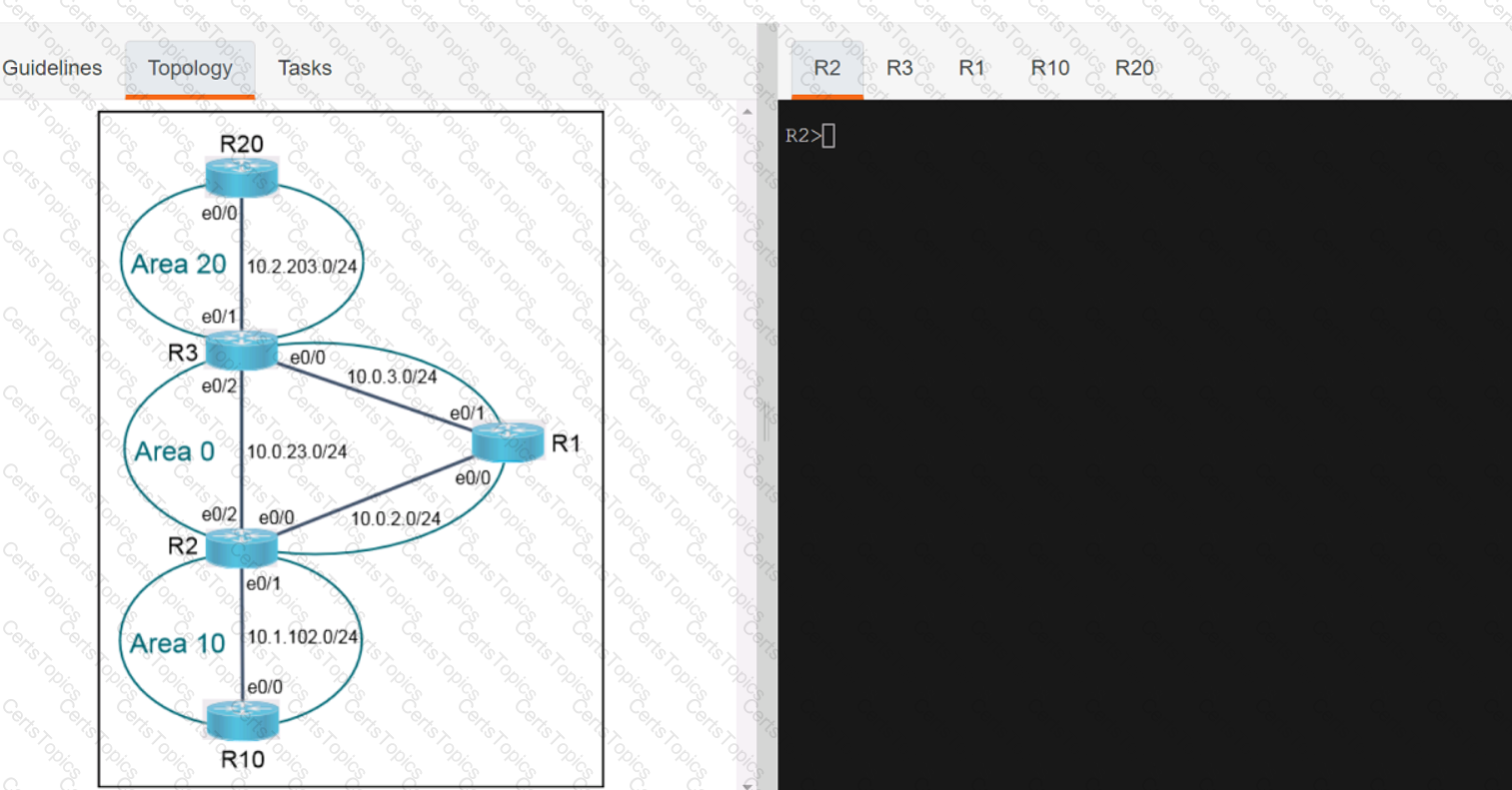
Refer to the exhibit Which command set is required on router R1 to allow the network administrator to authenticate via RADIUS'?

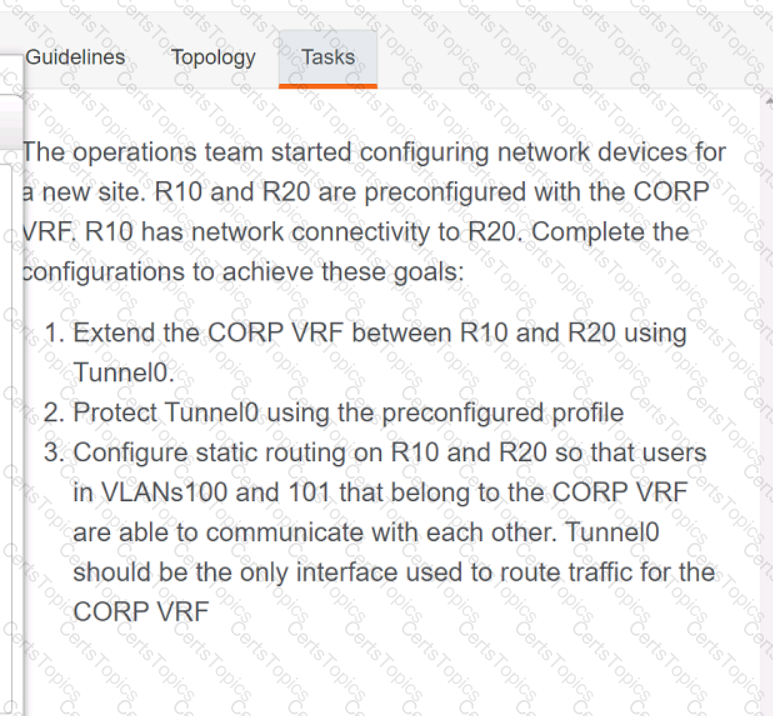
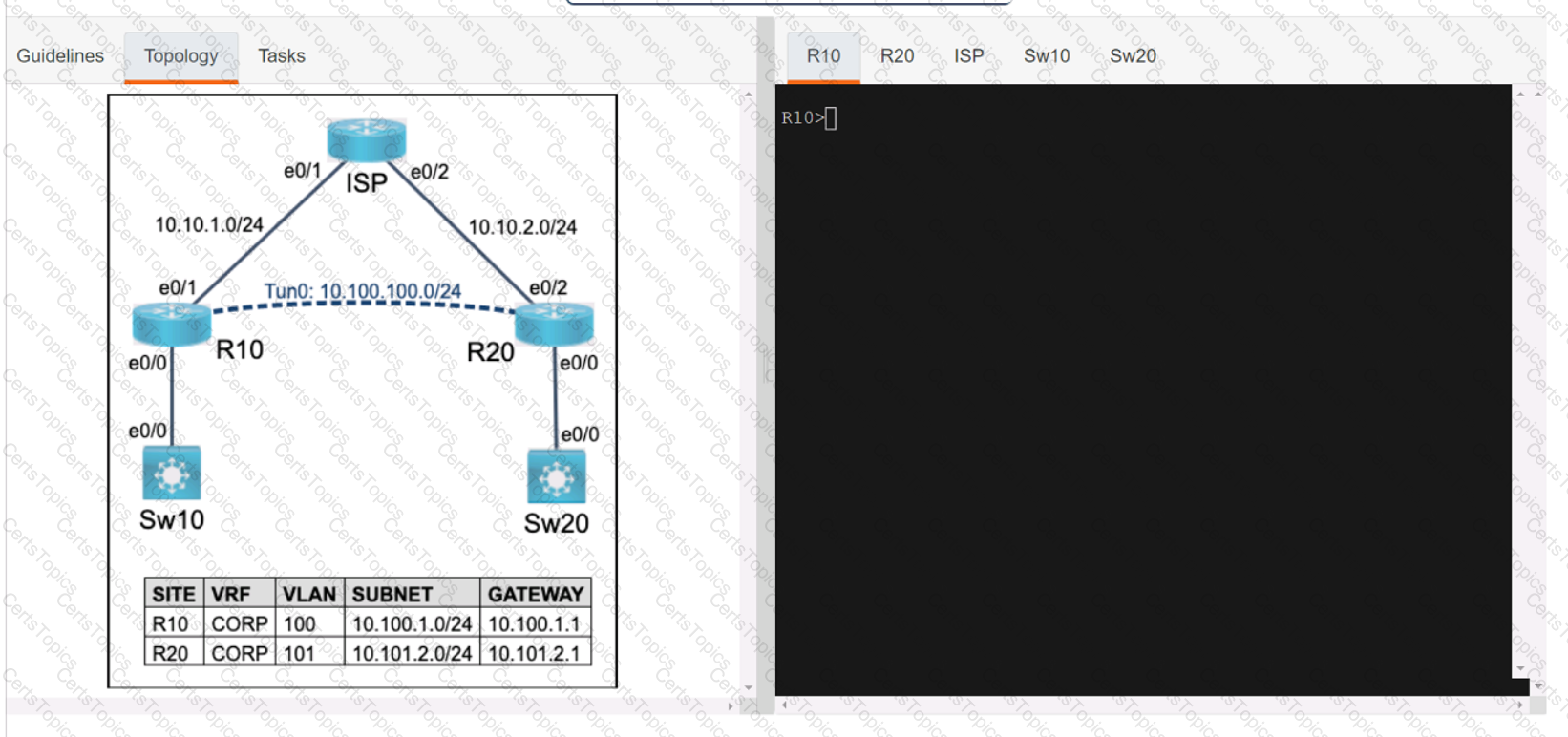
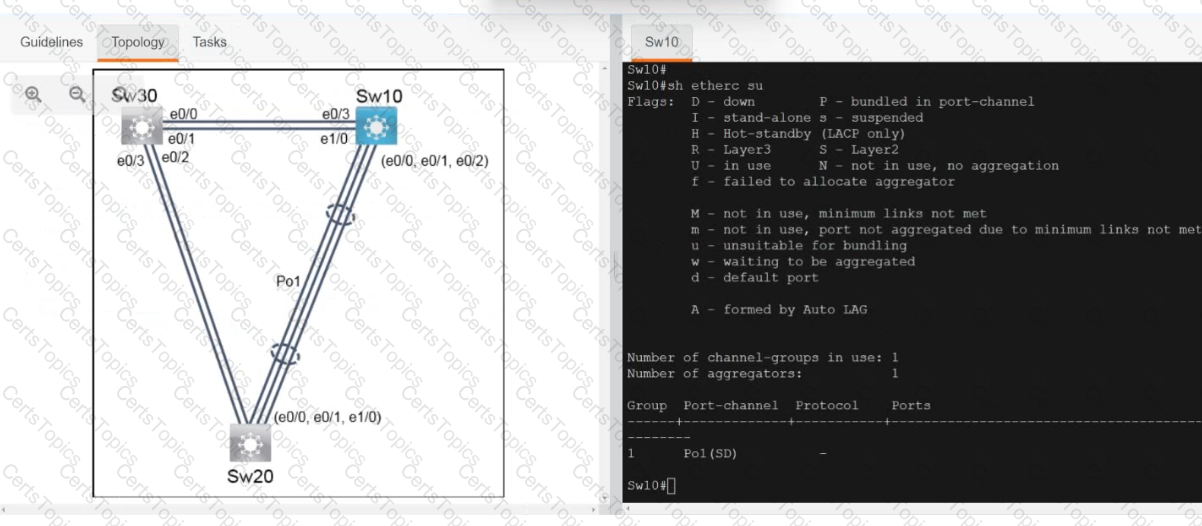
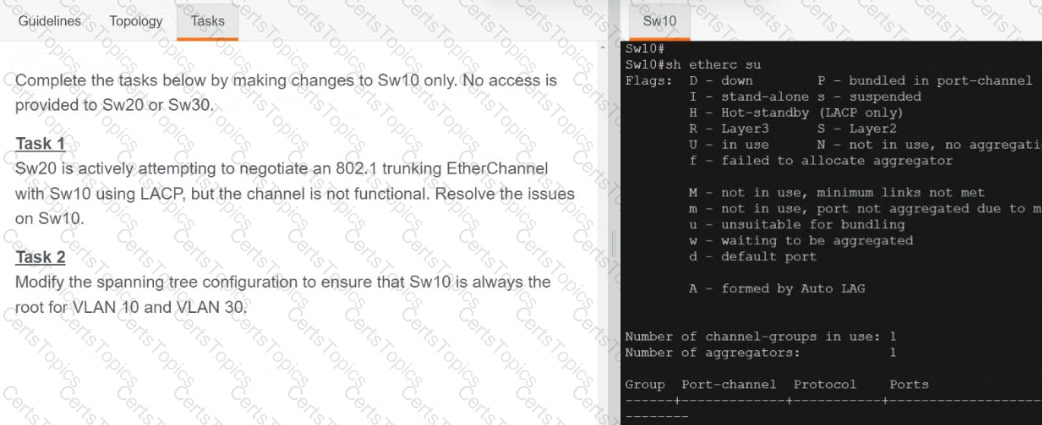
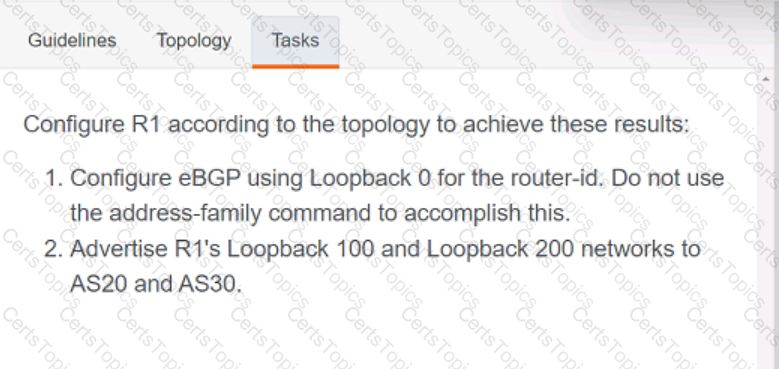
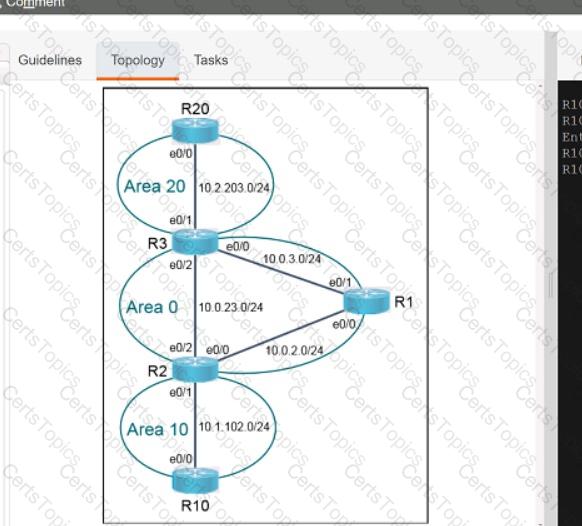
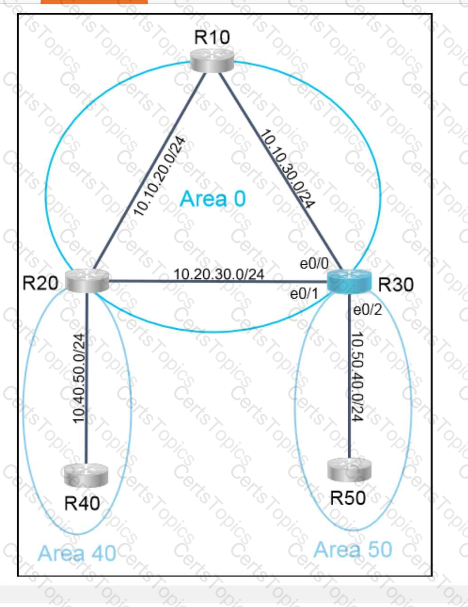
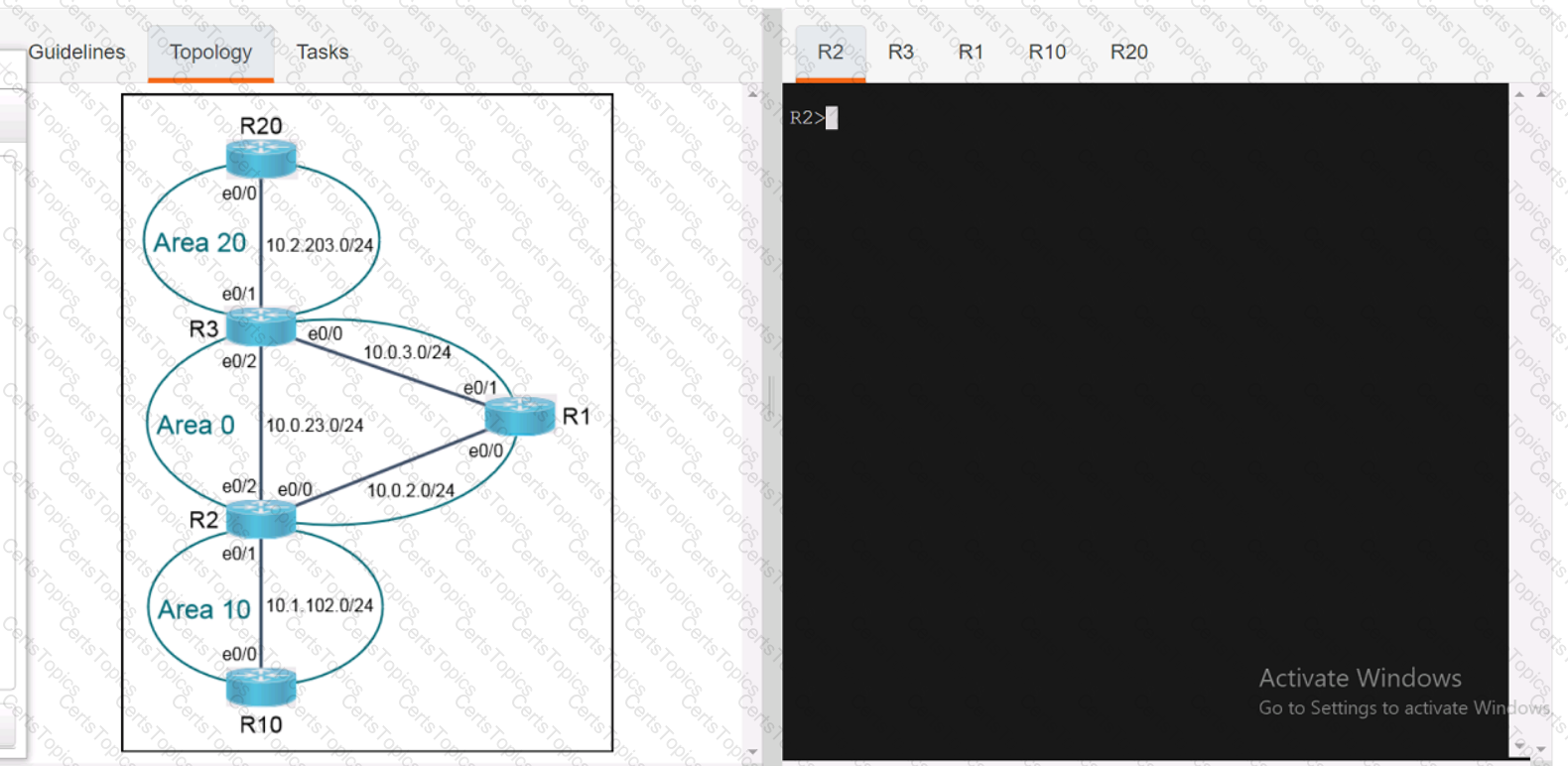
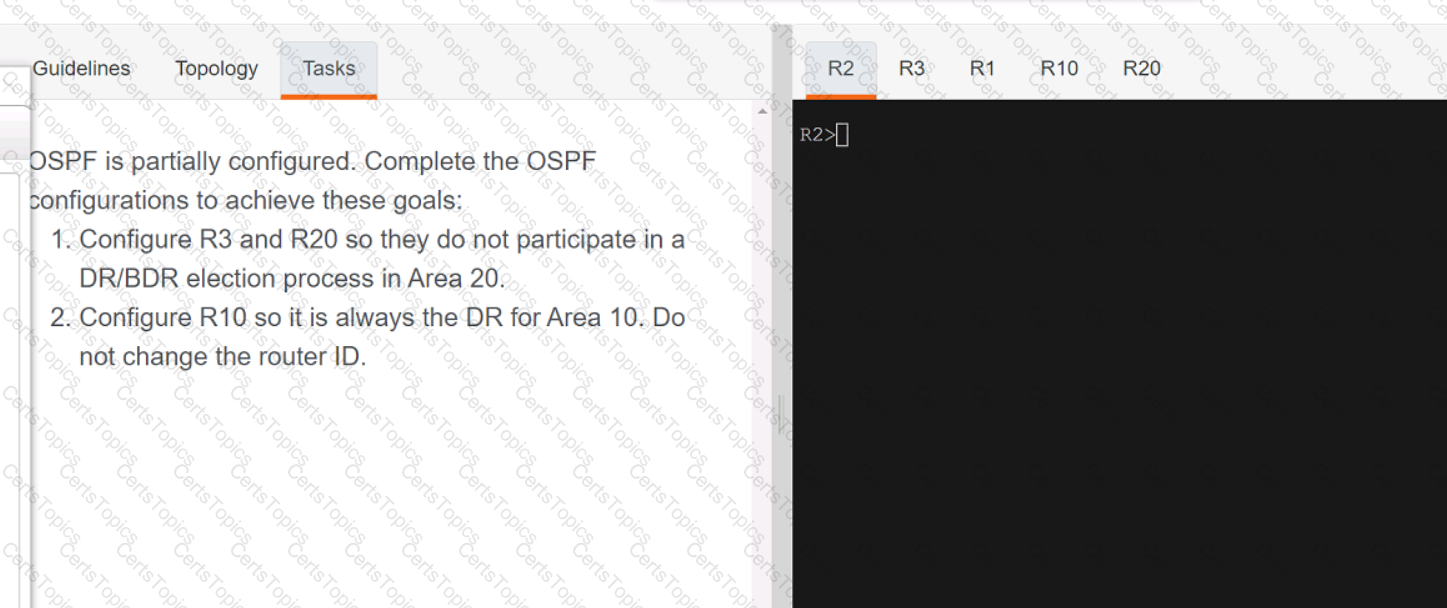
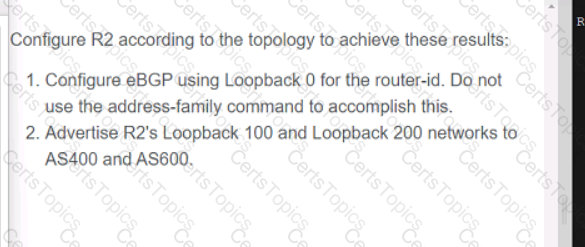
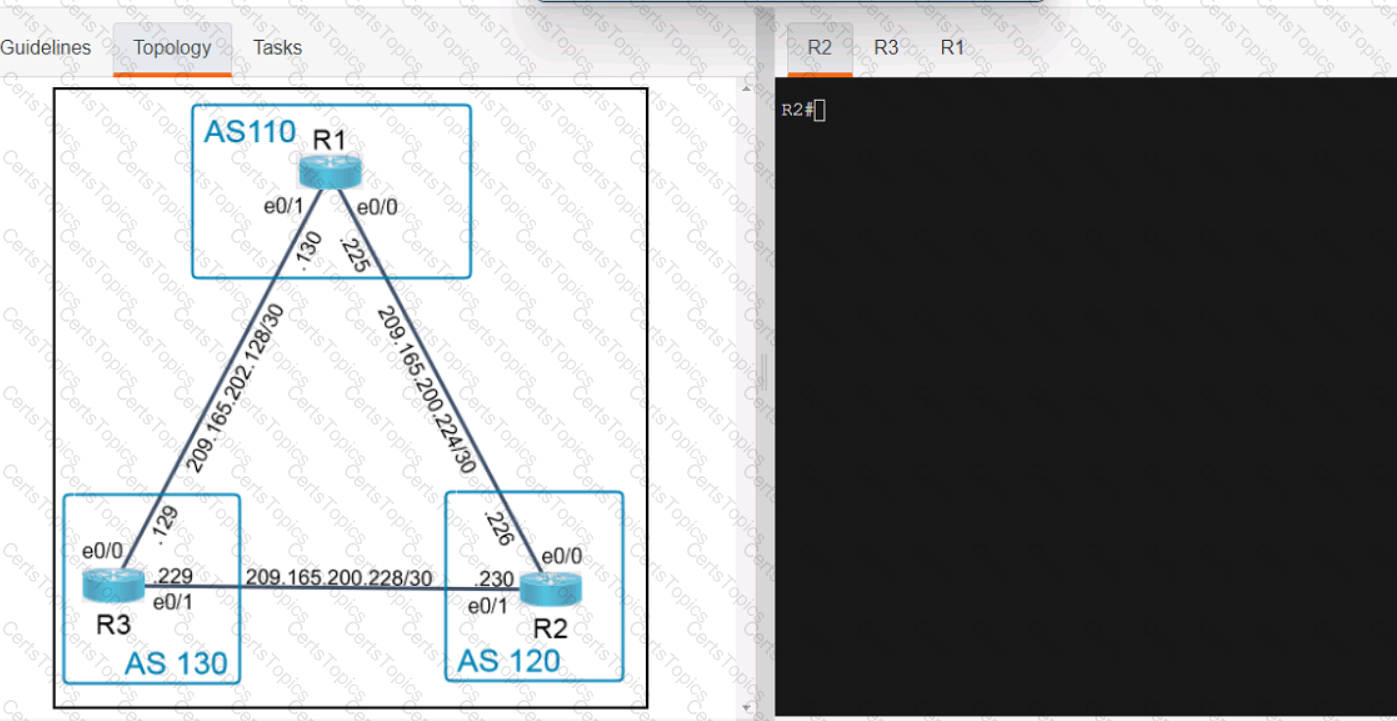
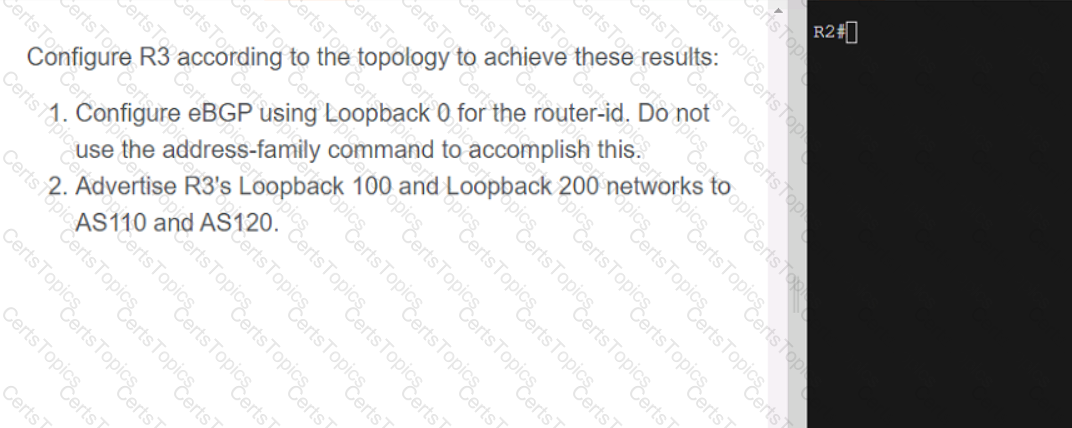
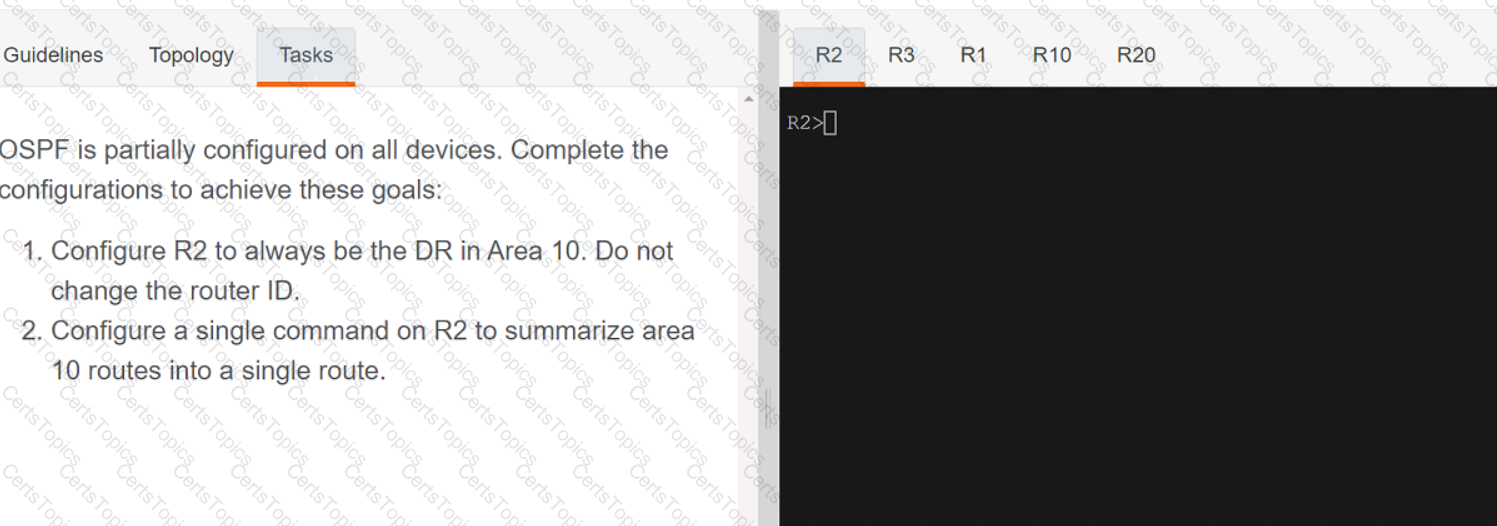
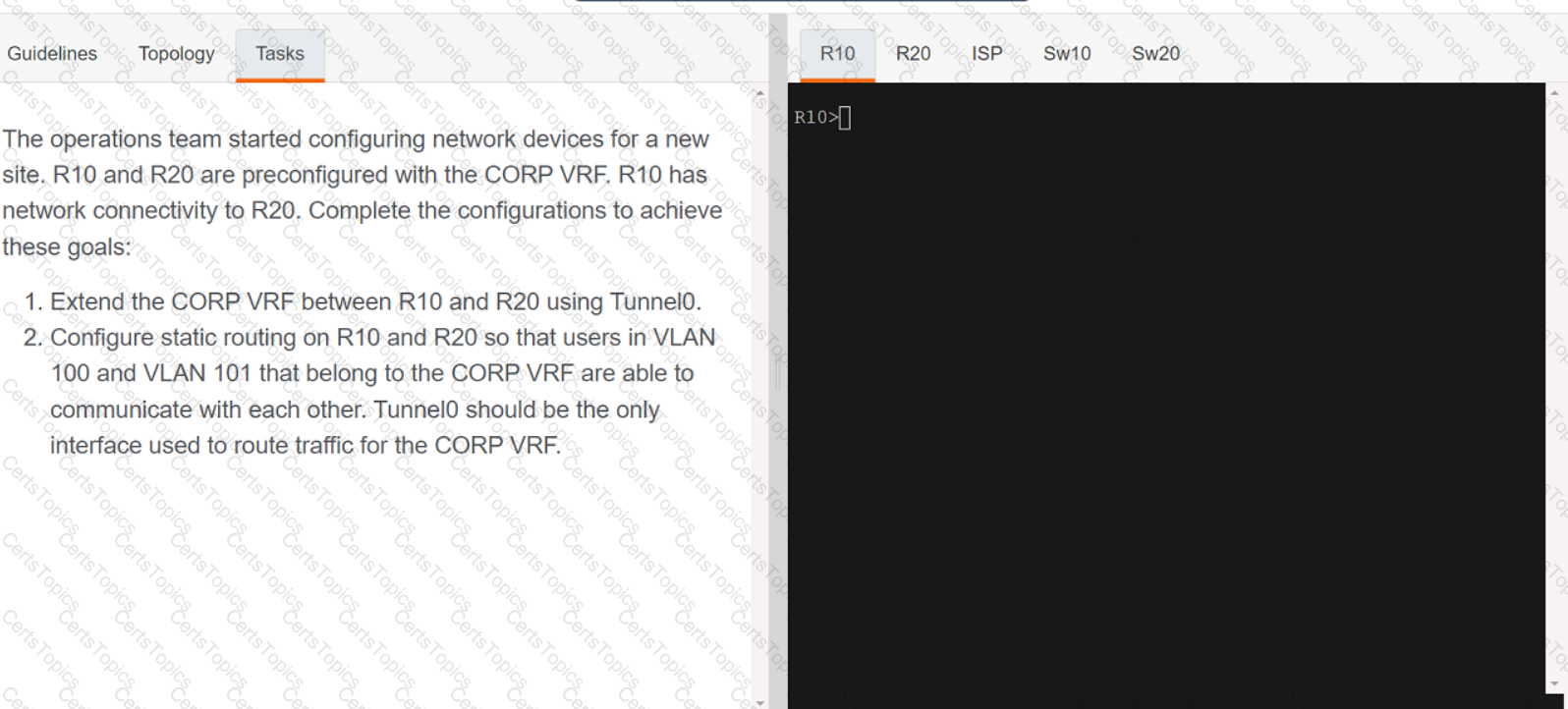
Refer to the exhibit.

Which EEM script generates a critical-level syslog message and saves a copy of the running configuration to the bootflash when an administrator saves the running configuration to the startup configuration?

Which nodes require VXLAN encapsulation support In a Cisco SD-Access deployment?

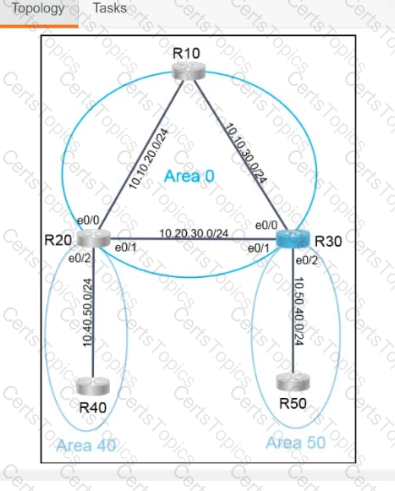
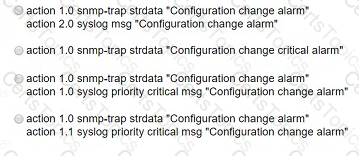
Refer to the exhibit. A network engineer must be notified when a user switches to configuration mode. Which script should be applied to receive an SNMP trap and a critical-level log message?
What is the function of an intermediate node in a Cisco SD-Access fabric?
What does the statement print(format(0.8, \0%')) display?
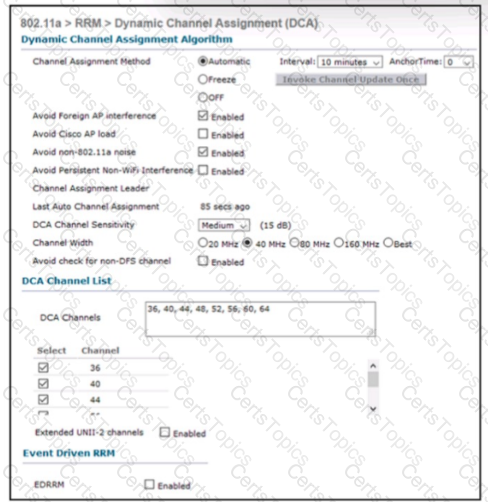
Refer to the exhibit An engineer is troubleshooting an issue with non-Wi-Fi interference on the 5-GHz band The engineer has enabled Cisco CleanAir and set the appropriate traps, but the AP does not change the channel when it detects significant interference Which action will resolve the issue?
Which data format can be used for an API request?
Which two operations are valid for RESTCONF? (Choose two)
Which AP mode analyzes the spectrum to detect sources of interference?
How is Layer 3 roaming accomplished in a unified wireless deployment?
Which RF value represents the decline of the RF signal amplitude over a given distance"?
An engineer measures the Wi-Fi coverage at a customer site. The RSSI values are recorded as follows:
•LocationA -72dBm
• Location B:-75 dBm
• Location C; -65 dBm
• Location D -80 dBm
Which two statements does the engineer use to explain these values to the customer? (Choose two.)
Which features does Cisco EDR use to provide threat detection and response protection?
Which tag defines the roaming domain and properties of an AP deployment?
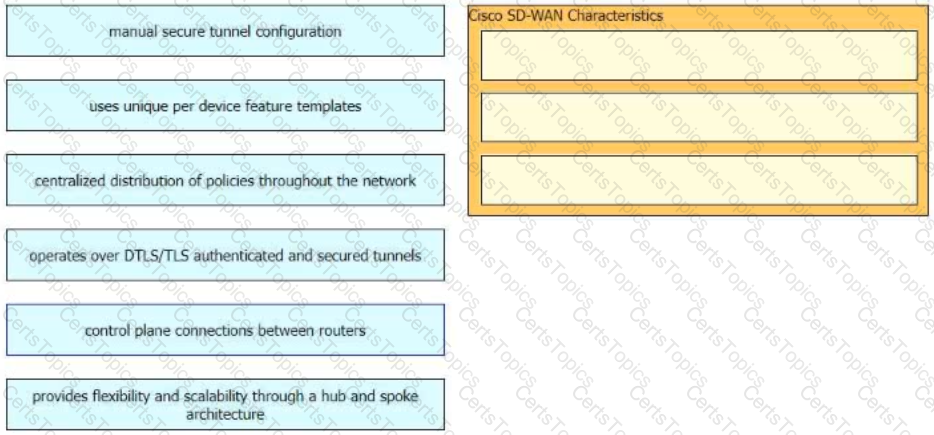
Drag and drop the characteristics of Cisco Catalyst SD-WAN from the left onto the right. Not all options are used.
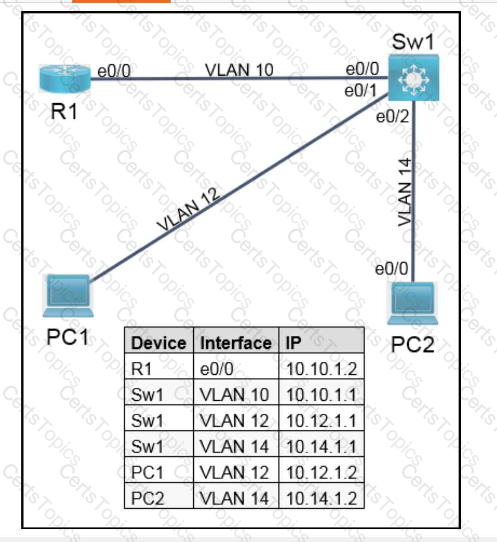
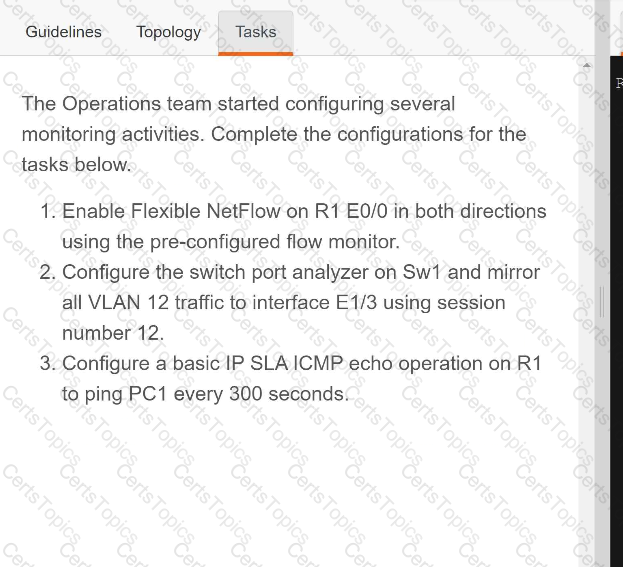
OR