Which two events trigger a CoA for an endpoint when CoA is enabled globally for ReAuth? (Choose two.)
An administrator must block access to BYOD endpoints that were onboarded without a certificate and have been reported as stolen in the Cisco ISE My Devices Portal. Which condition must be used when configuring an authorization policy that sets DenyAccess permission?
What is a valid guest portal type?
What sends the redirect ACL that is configured in the authorization profile back to the Cisco WLC?
Which two roles are taken on by the administration person within a Cisco ISE distributed environment? (Choose two.)
A network engineer is configuring a network device that needs to filter traffic based on security group tags using a security policy on a routed into this task?
An engineer tests Cisco ISE posture services on the network and must configure the compliance module to automatically download and install on endpoints Which action accomplishes this task for VPN users?
Which Cisco ISE service allows an engineer to check the compliance of endpoints before connecting to the network?
A Cisco device has a port configured in multi-authentication mode and is accepting connections only from hosts assigned the SGT of SGT_0422048549 The VLAN trunk link supports a maximum of 8 VLANS What is the reason for these restrictions?
The IT manager wants to provide different levels of access to network devices when users authenticate using TACACS+. The company needs specific commands to be allowed based on the Active Directory group membership of the different roles within the IT department. The solution must minimize the number of objects created in Cisco ISE. What must be created to accomplish this task?
An administrator is manually adding a device to a Cisco ISE identity group to ensure that it is able to access the network when needed without authentication Upon testing, the administrator notices that the device never hits the correct authorization policy line using the condition EndPoints LogicalProfile EQUALS static_list Why is this occurring?
An engineer is creating a new authorization policy to give the endpoints access to VLAN 310 upon successful authentication The administrator tests the 802.1X authentication for the endpoint and sees that it is authenticating successfully What must be done to ensure that the endpoint is placed into the correct VLAN?
An administrator needs to connect ISE to Active Directory as an external authentication source and allow the proper ports through the firewall. Which two ports should be opened to accomplish this task? (Choose two)
A network administrator is setting up wireless guest access and has been unsuccessful in testing client access. The endpoint is able to connect to the SSID but is unable to grant access to the guest network through the guest portal. What must be done to identify the problem?
In a standalone Cisco ISE deployment, which two personas are configured on a node? (Choose two )
When configuring an authorization policy, an administrator cannot see specific Active Directory groups present in their domain to be used as a policy condition. However, other groups that are in the same domain are seen What is causing this issue?
An administrator is configuring sponsored guest access using Cisco ISE Access must be restricted to the sponsor portal to ensure that only necessary employees can issue sponsored accounts and employees must be classified to do so What must be done to accomplish this task?
A company is attempting to improve their BYOD policies and restrict access based on certain criteria. The company's subnets are organized by building. Which attribute should be used in order to gain access based on location?
A customer wants to set up the Sponsor portal and delegate the authentication flow to a third party for added security while using Kerberos Which database should be used to accomplish this goal?
Which interface-level command is needed to turn on 802 1X authentication?
Which configuration is required in the Cisco ISE authentication policy to allow Central Web Authentication?
A Cisco ISE administrator needs to ensure that guest endpoint registrations are only valid for one day When testing the guest policy flow, the administrator sees that the Cisco ISE does not delete the endpoint in the Guest Endpoints identity store after one day and allows access to the guest network after that period. Which configuration is causing this problem?
An engineer is tasked with placing a guest access anchor controller in the DMZ. Which two ports or port sets must be opened up on the firewall to accomplish this task? (Choose two.)
An engineer is designing a BYOD environment utilizing Cisco ISE for devices that do not support native supplicants Which portal must the security engineer configure to accomplish this task?
Which two features are available when the primary admin node is down and the secondary admin node has not been promoted? (Choose two.)
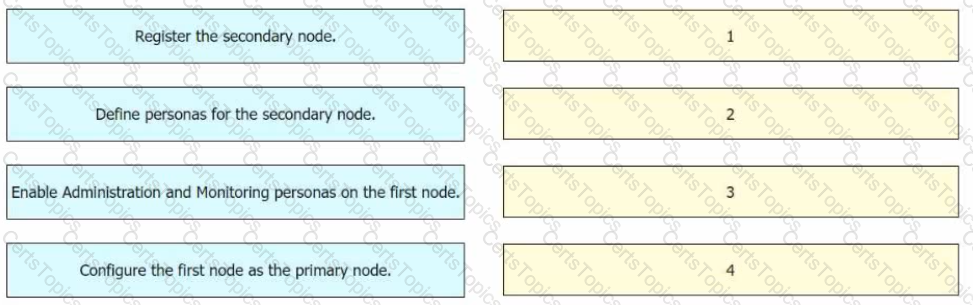
Drag and drop the configuration steps from the left into the sequence on the right to install two Cisco ISE nodes in a distributed deployment.
Which two endpoint compliance statuses are possible? (Choose two.)
Users in an organization report issues about having to remember multiple usernames and passwords. The network administrator wants the existing Cisco ISE deployment to utilize an external identity source to alleviate this issue. Which two requirements must be met to implement this change? (Choose two.)
An employee must access the internet through the corporate network from a new mobile device that does not support native supplicant provisioning provided by Cisco ISE. Which portal must the employee use to provision to the device?
An employee logs on to the My Devices portal and marks a currently on-boarded device as ‘Lost’.
Which two actions occur within Cisco ISE as a result oí this action? (Choose two)
Which two default guest portals are available with Cisco ISE? (Choose two.)
Which two methods should a sponsor select to create bulk guest accounts from the sponsor portal? (Choose two )
A network engineer needs to ensure that the access credentials are not exposed during the 802.1x authentication among components. Which two protocols should complete this task?

Refer to the exhibit Which switch configuration change will allow only one voice and one data endpoint on each port?
What is a function of client provisioning?