Microsoft Related Exams
SC-200 Exam







The Microsoft SC-200 exam assesses your knowledge in various security operation domains, including:
CertsTopics offers high-quality SC-200 exam dumps, questions and answers, and practice tests tailored to the Microsoft Certified: Security Operations Analyst Associate Exam syllabus. Our SC-200 study materials come in PDF and testing engine formats, ensuring effective preparation and a high success rate.
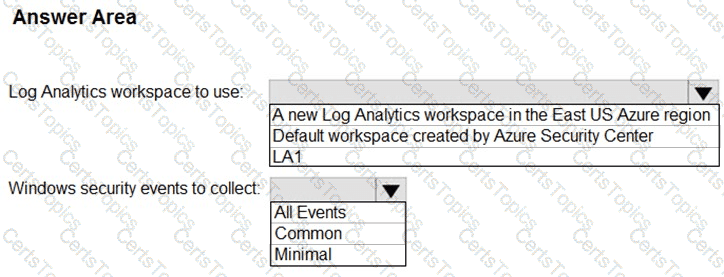
You need to implement Microsoft Defender for Cloud to meet the Microsoft Defender for Cloud requirements and the business requirements. What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to assign a role-based access control (RBAC) role to admin1 to meet the Azure Sentinel requirements and the business requirements.
Which role should you assign?
You need to restrict cloud apps running on CUENT1 to meet the Microsoft Defender for Endpoint requirements. Which two configurations should you modify? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.