An Ethernet switch has eight ports and all ports must be operational for 24 hours from Monday through Friday.
However, a failure of Port 7 occurs as follows:
● Monday=4 PM to 11 PM
● Wednesday= 2 PM to 10 PM
● Friday= 5 AM to11 AM
What is the MTTR of Port 7?
An organization wants to deploy a VM storage migration solution into their data center environment.
What is the result of deploying this type of solution?
What is an impact of a Denial of Service (DoS) attack?
Which modern technology enables data to be securely collected and processed at point of creation to create new value?
An organization is interested in a cloud service that provides middleware, development tools, and database management systems for application development and deployment.
Which cloud service model meets these requirements?
Why is it important for organizations to store protect and manage their data?
Which data protection solution provides the ability to select a backup technology based on demand?
In an SDS environment, which protocol supports the resource-oriented architecture for the development of scalable and lightweight web applications while adhering to a set of constraints?
Refer to the exhibit.
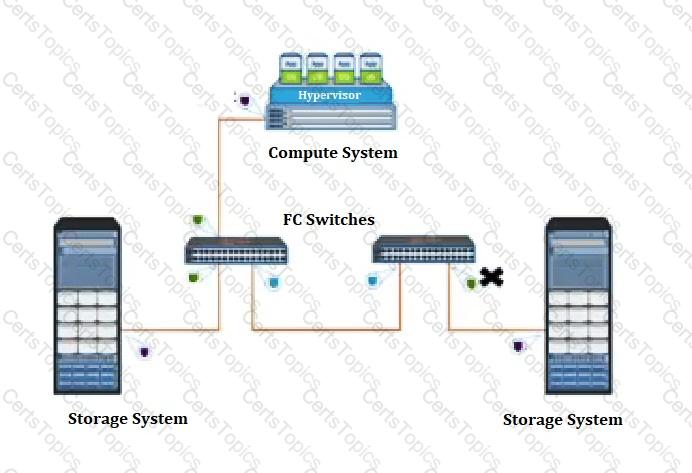
What type of Fibre Channel port does the “X” represent?
An organization wants to protect data from accidental deletion, application crashes, data corruption, and disaster.
Which solution should the organization adopt?
Which file system provides a streaming interface using the MapReduce framework?
Which Dell EMC product is designed to host both file and object data?
Which performance feature does an intelligent storage system provide?
Which network file sharing protocol provides cloud-based file sharing through a REST API interface?
Why is it important for organizations lo deploy business continuity solutions in their data center environment?
Which statement is true regarding virtual provisioning?
Which type of interface connects SSD drives to the storage array controller?
What is true about scale-out NAS storage architecture? (First Choose Correct option and give detailed explanation delltechnologies.com)
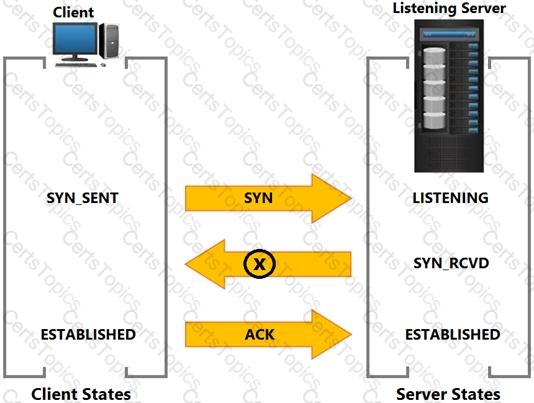
Based on the exhibit, what does the “X” represent?
How is NVMe used to connect a host to M.2 storage devices?
What is a benefit of using an existing Ethernet network infrastructure for storage connectivity?
Which Connectrix FC switch model supports NVMe in a 32Gb/s SAN fabric exclusively?
What is the function of a control plane in the SDDC?
An organization has two data centers separated by a distance of 1600 km. They want to replicate between these data centers for disaster recovery purposes. They are concerned that this will impact application response time.
Which solution will address this concern?
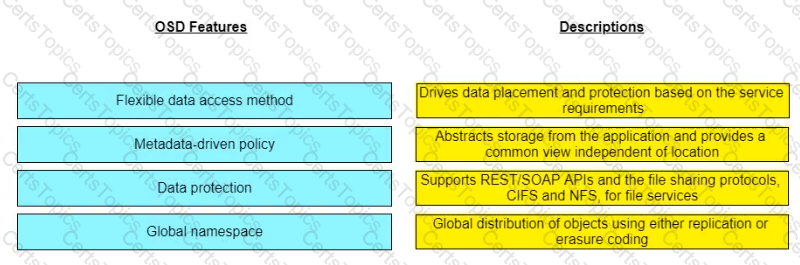
Match the object-based storage device (OSD) features with their descriptions.
Which plane of the SDDC architecture provides a CLI and GUI for IT to administrator the infrastructure and to configure policies? (Choose Correct Answer from Associate - Information Storage and Management version 5 Manual from dellemc.com and give explanation)
Which infrastructure building process allows organizations to repurpose existing infrastructure components and provides cost benefits?
What is an accurate statement about data shredding?
What is the maximum number of VLANs that can be supported with one VLAN tag field?
What is an accurate statement about scale-out NAS?
Under the PaaS model, which elements are managed by the consumer?
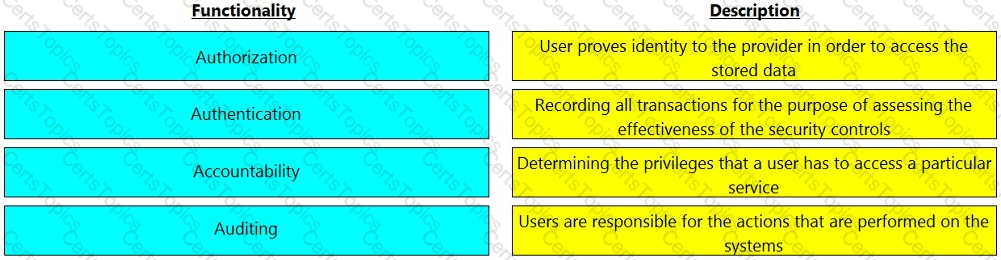
Match the functionality of a security goal with its description.
What is a benefit of using the FCoE storage protocol?
What is a benefit of migrating to a modern data center?
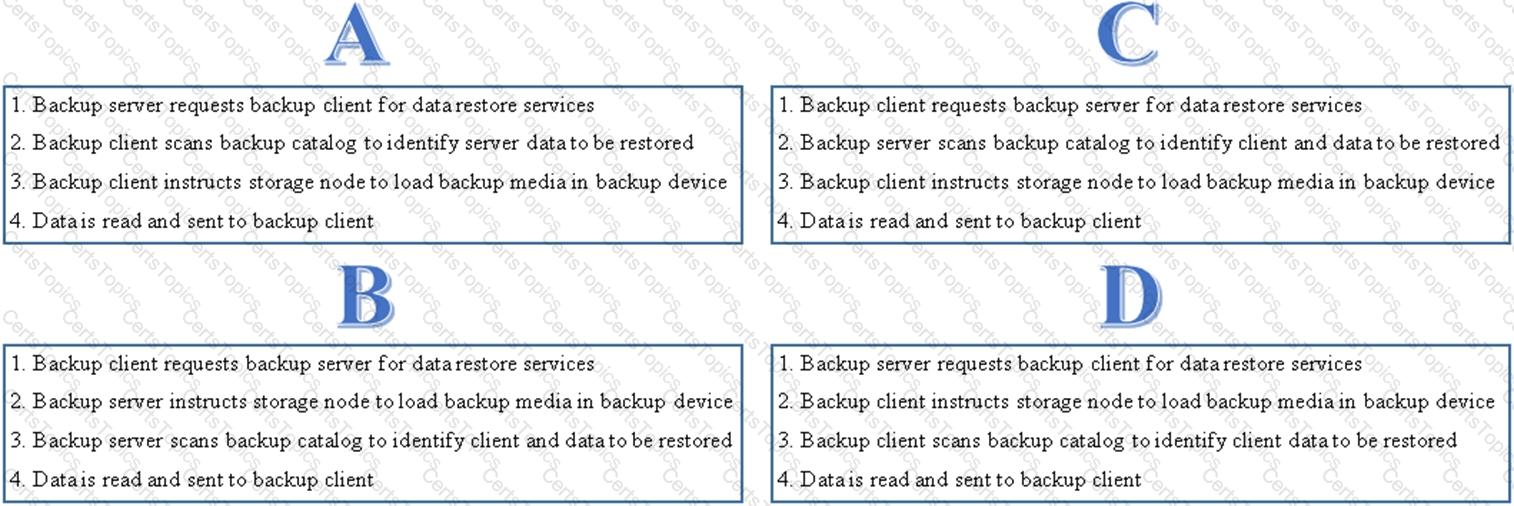
Which option shows the correct sequence of steps to perform a data recovery operation?
Which intelligent storage system component performs replication and storage management functions?
What is a feature a hypervisor?
What is the functionality of the application server in a Mobile Device Management?
A company is using an intrusion detection and prevention system (IDPS) to scan and analyze intrusion events.
Which IDPS technique uses a database that contains known attack patterns?
Which technology allows automation of sensors and devices to share and process information?
What is a benefit of using an existing IP-based network infrastructure for storage connectivity?
What is the key advantage of cloning a VM?
What occurs during a Shared Technology Vulnerability threat?
What is a purpose of the policy engine in a data archiving environment?
What is a function of a continuous data protection (CDP) appliance?
Which Dell EMC product is a disk-based backup and recovery solution that provides inherent source-based deduplication?
Refer to the Exhibit:
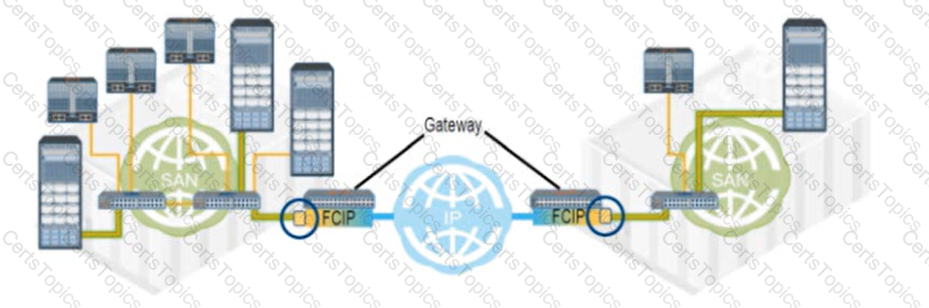
What type of FC port connects each FCIP gateway to each FC SAN?
An IT organization wants to deploy four FC switches for compute and storage system connectivity. To meet performance requirements, a maximum of one active ISL and redundant ISLs for their compute to storage traffic.
Which FC SAN topology should be recommended?
What is the lowest to highest order of I/O performance among these storage devices?
What is true about scale-out NAS storage architecture?
What information is available in a capacity planning report for storage infrastructure?
What is true about a software defined data center?
Why is it important for organizations to implement a multi-site remote replication solution?
Which block storage device protocol achieves the optimal cost-effective balance between I/O performance and high storage capacity for midrange storage applications?
A Fibre Channel switch has eight ports and all ports must be operational from 8 AM to 8 PM, Monday through Friday. However, a failure of Port 2 occurs on a particular week as follows:
Monday = 10 AM to 12 PM Wednesday = 4 PM to 9 PM Thursday = 4 PM to 7 PM
Friday = 3 PM to 6 PM Saturday = 9 AM to 1 PM
What is the availability of Port 2 in that week?
An organization is planning to adopt pre-integrated systems to deploy compute, network, storage, and management functions as a single engineered solution.
Which approach should the organization adopt?