Table: DeviceFileEvents
Aggregation function: count()
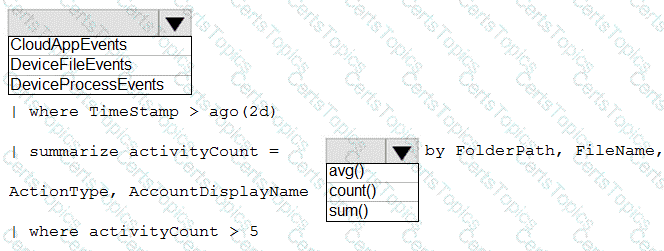
In Microsoft Defender XDR advanced hunting, data tables such as DeviceFileEvents, DeviceProcessEvents, and CloudAppEvents are used to investigate various types of activities. Since this query aims to investigate an issue related to file activity—specifically identifying when files have been accessed, modified, or created repeatedly—the correct data source table is DeviceFileEvents. This table contains information about file-level activities recorded by Defender for Endpoint sensors, including file path, file name, action type, and user account involved.
The KQL structure shown in the image follows standard hunting query syntax:
DeviceFileEvents
| where Timestamp > ago(2d)
| summarize activityCount = count() by FolderPath, FileName, ActionType, AccountDisplayName
| where activityCount > 5
Here’s why:
The where Timestamp > ago(2d) clause filters results from the last 2 days, a typical timeframe for immediate investigations.
The summarize operator groups events by FolderPath, FileName, ActionType, and AccountDisplayName, then uses count() to determine how many times each file was acted upon.
Finally, where activityCount > 5 filters to show only unusually high-frequency activity, which might indicate suspicious or automated file manipulation.
Microsoft Defender XDR documentation highlights that DeviceFileEvents is the correct schema for file activity investigations, while DeviceProcessEvents focuses on process creation and execution, and CloudAppEvents targets cloud application usage.
Thus, the verified and documented correct completions are:
Table: DeviceFileEvents
Aggregation function: count()