Azure Automation now ships with the Azure PowerShell module of version 0.8.6, which introduced the ability to non-interactively authenticate to Azure using OrgId (Azure Active Directory user) credential-based authentication. Using the steps below, you can set up Azure Automation to talk to Azure using this authentication type.
Step 1: Find the Azure Active Directory associated with the Azure subscription to manage:
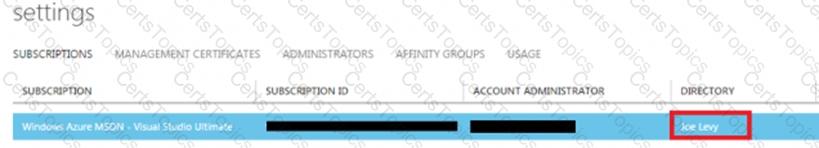
1. Log in to the Azure portal as the service administrator for the Azure subscription you want to manage using Azure Automation. You can find this user by logging in to the Azure portal as any user with access to this Azure subscription, then clicking Settings, then Administrators.

2. Note the name of the directory associated with the Azure subscription you want to manage. You can find this directory by clicking Settings, then Subscriptions.
Step 2: Create an Azure Active Directory user in the directory associated with the Azure subscription to manage:
You can skip this step if you already have an Azure Active Directory user in this directory. and plan to use this OrgId to manage Azure.
1. In the Azure portal click on Active Directory service.
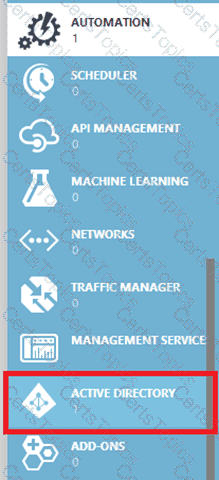
2. Click the directory name that is associated with this Azure subscription.
3. Click on the Users tab and then click the Add User button.
4. For type of user, select “New user in yourorganization.” Enter a username for the user to create.
5. Fill out the user’s profile. For role, pick “User.” Don’t enable multi-factor authentication. Multi-factor accounts cannot be used with Azure Automation.
6. Click Create.
7. Jot down the full username (including part after @ symbol) and temporary password.
Step 3: Allow this Azure Active Directory user to manage this Azure subscription.
1. Click on Settings (bottom Azure tab under StorSimple)

2. Click Administrators
3. Click the Add button. Type the full user name (including part after @ symbol) of the Azure Active Directory user you want to set up to manage Azure. For subscriptions, choose the Azure subscriptions you want this user to be able to manage. Click the check mark.
Step 4: ConfigureAzure Automation to use this Azure Active Directory user to manage this Azure subscription
Create an Azure Automation credential asset containing the username and password of the Azure Active Directory user that you have just created. You can create a credential asset in Azure Automation by clicking into an Automation Account and then clicking the Assets tab, then the Add Setting button.
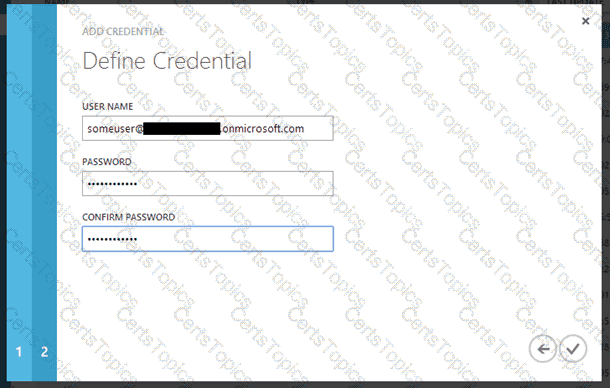
Note: Once you have set up the Azure Active Directory credential in Azure and Azure Automation, you can now manage Azure from Azure Automation runbooks using this credential.
[References:, https://azure.microsoft.com/sv-se/blog/azure-automation-authenticating-to-azure-using-azure-active-directory/, , ]