You are creating a real-time policy for cloud applications.
In addition to users, groups, and organizational units, which two source criteria would support this scenario? (Choose two.)
What are two valid use cases for the Cloud Confidence Index (CCI)? (Choose two.)
Click the Exhibit button.
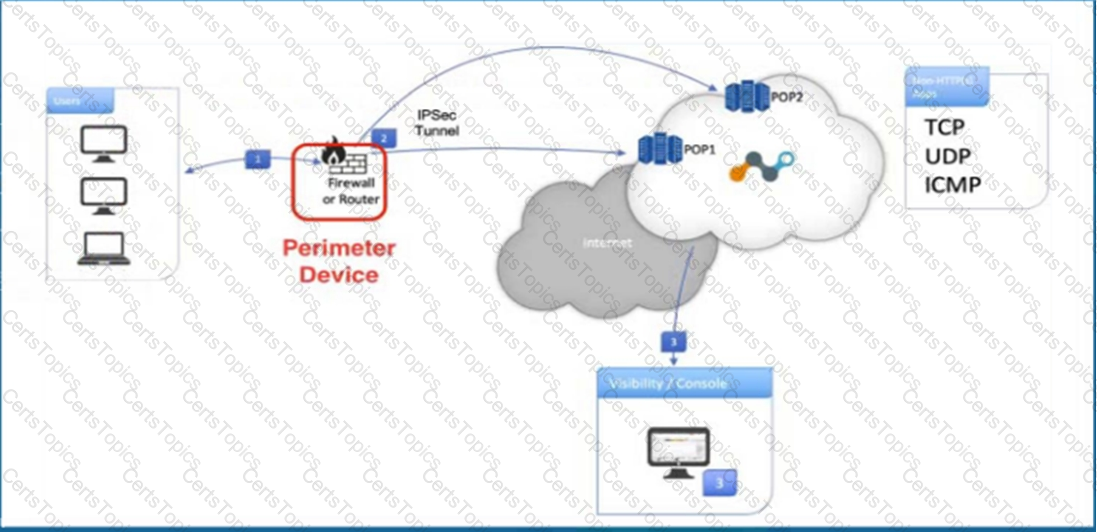
Referring to the exhibit, what are two recommended steps to be set on the perimeter device to monitor IPsec tunnels to a Netskope data plane? (Choose two.)
A customer wants to detect misconfigurations in their AWS cloud instances.
In this scenario, which Netskope feature would you recommend to the customer?
A new customer is concerned about performance, especially with respect to Microsoft 365. They have offices in 20 countries around the world and their workforce is mostly mobile.
In this scenario, which two statements about NewEdge would align with the customer's requirements? (Choose two.)
When would an administrator need to use a tombstone file?
Your department is asked to report on GDPR data publicly exposed in Microsoft 365, Salesforce. and Slack-sanctioned cloud applications. Which deployment model would you use to discover this data?
You have an issue with the Netskope client connecting to the tenant.
In this scenario, what are two ways to collect the logs from the client machine? (Choose two.)
You are required to mitigate malicious scripts from being downloaded into your corporate devices every time a user goes to a website. Users need to access websites from a variety of categories, including new websites.
Which two actions would help you accomplish this task while allowing the user to work? (Choose two.)
In the Tenant III, which two methods would an administrator use to update a File Profile with malicious file hashes? (Choose two)
When designing an architecture with Netskope Private Access, which element guarantees connectivity between the Netskope cloud and the private application?
A company is attempting to steer traffic to Netskope using GRE tunnels. They notice that after the initial configuration, users cannot access external websites from their browsers.
What are three probable causes for this issue? (Choose three.)
Click the Exhibit button.

A user is uploading a file containing PCI-DSS data to the corporate Google Drive instance. You notice that the upload is not blocked by the policy shown in the exhibit. Which statement is correct in this scenario?
Which two statements are correct about DLP Incidents in the Netskope platform? (Choose two.)
You want to set up a Netskope API connection to Box.
What two actions must be completed to enable this connection? (Choose two.)
What are two pillars of CASB? (Choose two.)
You are deploying TLS support for real-time Web and SaaS transactions. What are two secure implementation methods in this scenario? (Choose two.)
Why would you want to define an App Instance?
What are two supported ways to provision users to your customer's Netskope tenant? (Choose two.)
Which two technologies form a part of Netskope's Threat Protection module? (Choose two.)
According to Netskope. what are two preferred methods to report a URL miscategorization? (Choose two.)
API-enabled Protection traffic is sent to which Netskope component?
You want to use an out-of-band API connection into your sanctioned Microsoft 365 OneDrive for Business application to find sensitive content, enforce near real-time policy controls, and quarantine malware.
In this scenario, which primary function in the Netskope platform would you use to connect your application to Netskope?
You are working with traffic from applications with pinned certificates. In this scenario, which statement is correct?
What information is displayed in an application's Cloud Confidence Index (CCI) page? (Choose two.)
You are required to create a policy that will notify and allow users to log into their personal Google Drive instance.
Which two policy components must be configured to enforce this use case? (Choose two.)
Click the Exhibit button.
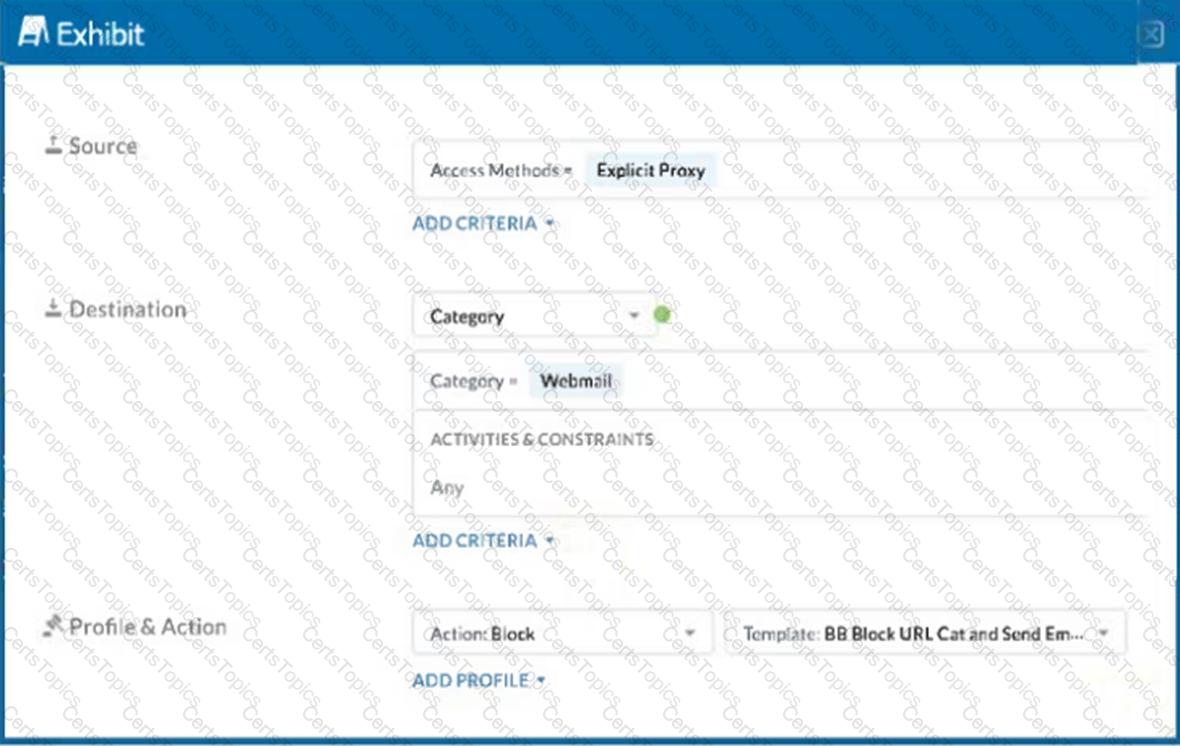
A user has the Netskope Client enabled with the correct steering configuration applied. The exhibit shows an inline policy that has a predefined webmail category blocked. However the user is still able to access Yahoo mail.
Which statement is correct in this scenario?
You want to see the actual data that caused the policy violation within a DLP Incident view.
In this scenario, which profile must be set up?
Users are connecting to sanctioned cloud applications from public computers, such as from a hotel business center.
Which traffic steering method would work in this scenario?
What are two CASB inline interception use cases? (Choose two.)
You want to take into account some recent adjustments to CCI scoring that were made in your Netskope tenant.
In this scenario, which two CCI aspects in the Ul would be used in a real-time protection policy? (Choose two.)
You investigate a suspected malware incident and confirm that it was a false alarm.
What are two uses for deploying a Netskope Virtual Appliance? (Choose two.)
A customer changes CCI scoring from the default objective score to another score. In this scenario, what would be a valid reason for making this change?
What are two uses for deploying a Netskope Virtual Appliance? (Choose two.)
In the Skope IT interface, which two event tables would be used to label a cloud application instance? (Choose two.)
As an administrator, you are investigating an increase in the number of incidents related to compromised credentials. You are using the Netskope Compromised Credentials feature on your tenant to assess the situation. Which insights would you find when using this feature? (Choose two)
Which two capabilities are part of Netskope's Adaptive Zero Trust Data Protection? (Choose two.)