An administrator would like to troubleshoot why templating is not working for some traffic. How can he determine at which rule templating is disabled?
When gathering information about a gateway using CPINFO, what information is included or excluded when using the “-x” parameter?
Where do you create and modify the Mobile Access policy in R81?
Which statement is true about ClusterXL?
In SmartEvent, what are the different types of automatic reactions that the administrator can configure?
Which web services protocol is used to communicate to the Check Point R81 Identity Awareness Web API?
Which of the following will NOT affect acceleration?
How do Capsule Connect and Capsule Workspace differ?
What is the command to check the status of the SmartEvent Correlation Unit?
You need to see which hotfixes are installed on your gateway, which command would you use?
Which command gives us a perspective of the number of kernel tables?
What is the protocol and port used for Health Check and State Synchronization in ClusterXL?
When an encrypted packet is decrypted, where does this happen?
Customer’s R81 management server needs to be upgraded to R81.20. What is the best upgrade method when the management server is not connected to the Internet?
What is a best practice before starting to troubleshoot using the “fw monitor” tool?
Which command shows the current connections distributed by CoreXL FW instances?
With Mobile Access enabled, administrators select the web-based and native applications that can be accessed by remote users and define the actions that users can perform the applications. Mobile Access encrypts all traffic using:
Which one of the following is true about Capsule Connect?
When setting up an externally managed log server, what is one item that will not be configured on the R81 Security Management Server?
What scenario indicates that SecureXL is enabled?
What is the purpose of Priority Delta in VRRP?
Which statements below are CORRECT regarding Threat Prevention profiles in Smart Dashboard?
What information is NOT collected from a Security Gateway in a Cpinfo?
John detected high load on sync interface. Which is most recommended solution?
SandBlast has several functional components that work together to ensure that attacks are prevented in real-time. Which the following is NOT part of the SandBlast component?
Automation and Orchestration differ in that:
You want to store the GAIA configuration in a file for later reference. What command should you use?
When Dynamic Dispatcher is enabled, connections are assigned dynamically with the exception of:
What is the most recommended way to install patches and hotfixes?
Which Check Point daemon monitors the other daemons?
When installing a dedicated R81 SmartEvent server. What is the recommended size of the root partition?
As a valid Mobile Access Method, what feature provides Capsule Connect/VPN?
What is considered Hybrid Emulation Mode?
: 156
VPN Link Selection will perform the following when the primary VPN link goes down?
The Correlation Unit performs all but the following actions:
Both ClusterXL and VRRP are fully supported by Gaia R81.20 and available to all Check Point appliances. Which the following command is NOT related to redundancy and functions?
Which of the following links will take you to the SmartView web application?
What is the main difference between Threat Extraction and Threat Emulation?
How often does Threat Emulation download packages by default?
SmartEvent does NOT use which of the following procedures to identify events:
Using ClusterXL, what statement is true about the Sticky Decision Function?
To enable Dynamic Dispatch on Security Gateway without the Firewall Priority Queues, run the following command in Expert mode and reboot:
To accelerate the rate of connection establishment, SecureXL groups all connection that match a particular service and whose sole differentiating element is the source port. The type of grouping enables even the very first packets of a TCP handshake to be accelerated. The first packets of the first connection on the same service will be forwarded to the Firewall kernel which will then create a template of the connection. Which of the these is NOT a SecureXL template?
Which one of the following is true about Threat Extraction?
In the Check Point Firewall Kernel Module, each Kernel is associated with a key, which specifies the type of traffic applicable to the chain module. For Wire Mode configuration, chain modules marked with ____________ will not apply.
Which Check Point software blades could be enforced under Threat Prevention profile using Check Point R81.20 SmartConsole application?
SecureXL improves non-encrypted firewall traffic throughput and encrypted VPN traffic throughput.
What is a feature that enables VPN connections to successfully maintain a private and secure VPN session without employing Stateful Inspection?
What is true about the IPS-Blade?
Which command can you use to verify the number of active concurrent connections?
Which is NOT an example of a Check Point API?
You can select the file types that are sent for emulation for all the Threat Prevention profiles. Each profile defines a(n) _____ or _____ action for the file types.
Fill in the blank: The tool _____ generates a R81 Security Gateway configuration report.
What is the least amount of CPU cores required to enable CoreXL?
What is the difference between an event and a log?
Advanced Security Checkups can be easily conducted within:
Connections to the Check Point R81 Web API use what protocol?
What makes Anti-Bot unique compared to other Threat Prevention mechanisms, such as URL Filtering, Anti-Virus, IPS, and Threat Emulation?
You are working with multiple Security Gateways enforcing an extensive number of rules. To simplify security administration, which action would you choose?
The Event List within the Event tab contains:
NAT rules are prioritized in which order?
1. Automatic Static NAT
2. Automatic Hide NAT
3. Manual/Pre-Automatic NAT
4. Post-Automatic/Manual NAT rules
Which command would disable a Cluster Member permanently?
Where you can see and search records of action done by R81 SmartConsole administrators?
What command verifies that the API server is responding?
Which of the following is a new R81 Gateway feature that had not been available in R77.X and older?
Which one of these features is NOT associated with the Check Point URL Filtering and Application Control Blade?
In R81, how do you manage your Mobile Access Policy?
Which of the following process pulls application monitoring status?
What Factor preclude Secure XL Templating?
Which packet info is ignored with Session Rate Acceleration?
In a Client to Server scenario, which inspection point is the first point immediately following the tables and rule base check of a packet coming from outside of the network?
CPM process stores objects, policies, users, administrators, licenses and management data in a database. The database is:
The Security Gateway is installed on GAIA R81. The default port for the Web User Interface is ______ .
How many images are included with Check Point TE appliance in Recommended Mode?
Which CLI command will reset the IPS pattern matcher statistics?
fwssd is a child process of which of the following Check Point daemons?
Which statement is correct about the Sticky Decision Function?
In R81 spoofing is defined as a method of:
Automatic affinity means that if SecureXL is running, the affinity for each interface is automatically reset every
Which of the following authentication methods ARE NOT used for Mobile Access?
R81.20 management server can manage gateways with which versions installed?
Which of the following type of authentication on Mobile Access can NOT be used as the first authentication method?
To fully enable Dynamic Dispatcher on a Security Gateway:
Which view is NOT a valid CPVIEW view?
Which statement is true regarding redundancy?
When doing a Stand-Alone Installation, you would install the Security Management Server with which other Check Point architecture component?
What is the correct command to observe the Sync traffic in a VRRP environment?
Which Mobile Access Application allows a secure container on Mobile devices to give users access to internal website, file share and emails?
The Firewall kernel is replicated multiple times, therefore:
Fill in the blank: The command ___________________ provides the most complete restoration of a R81 configuration.
You noticed that CPU cores on the Security Gateway are usually 100% utilized and many packets were dropped. You don’t have a budget to perform a hardware upgrade at this time. To optimize drops you decide to use Priority Queues and fully enable Dynamic Dispatcher. How can you enable them?
There are 4 ways to use the Management API for creating host object with R81 Management API. Which one is NOT correct?
Fill in the blank: The R81 feature _____ permits blocking specific IP addresses for a specified time period.
SSL Network Extender (SNX) is a thin SSL VPN on-demand client that is installed on the remote user’s machine via the web browser. What are the two modes of SNX?
Which NAT rules are prioritized first?
Fill in the blank: The “fw monitor” tool can be best used to troubleshoot ____________________.
Fill in the blank: The R81 SmartConsole, SmartEvent GUI client, and _______ consolidate billions of logs and shows then as prioritized security events.
The system administrator of a company is trying to find out why acceleration is not working for the traffic. The traffic is allowed according to the rule base and checked for viruses. But it is not accelerated.
What is the most likely reason that the traffic is not accelerated?
After the initial installation on Check Point appliance, you notice that the Management-interface and default gateway are incorrect.
Which commands could you use to set the IP to 192.168.80.200/24 and default gateway to 192.168.80.1.
Which Check Point feature enables application scanning and the detection?
Which file contains the host address to be published, the MAC address that needs to be associated with the IP Address, and the unique IP of the interface that responds to ARP request?
What will SmartEvent automatically define as events?
What is the recommended number of physical network interfaces in a Mobile Access cluster deployment?
Which of the following Windows Security Events will not map a username to an IP address in Identity Awareness?
In the Check Point Firewall Kernel Module, each Kernel is associated with a key, which specifies the type of traffic applicable to the chain module. For Stateful Mode configuration, chain modules marked with __________________ will not apply.
On what port does the CPM process run?
Which path below is available only when CoreXL is enabled?
After trust has been established between the Check Point components, what is TRUE about name and IP-address changes?
Which tool provides a list of trusted files to the administrator so they can specify to the Threat Prevention blade that these files do not need to be scanned or analyzed?
The ____ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
Which of the following is NOT a VPN routing option available in a star community?
What key is used to save the current CPView page in a filename format cpview_”cpview process ID”.cap”number of captures”?
The SmartEvent R81 Web application for real-time event monitoring is called:
What kind of information would you expect to see using the sim affinity command?
Tom has connected to the R81 Management Server remotely using SmartConsole and is in the process of making some Rule Base changes, when he suddenly loses connectivity. Connectivity is restored shortly afterward.
What will happen to the changes already made?
Check Point APIs allow system engineers and developers to make changes to their organization’s security policy with CLI tools and Web Services for all the following except:
GAiA Software update packages can be imported and installed offline in situation where:
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ________ .
You have a Geo-Protection policy blocking Australia and a number of other countries. Your network now requires a Check Point Firewall to be installed in Sydney, Australia.
What must you do to get SIC to work?
Which is NOT an example of a Check Point API?
What is the valid range for VRID value in VRRP configuration?
SmartEvent provides a convenient way to run common command line executables that can assist in investigating events. Right-clicking the IP address, source or destination, in an event provides a list of default and customized commands. They appear only on cells that refer to IP addresses because the IP address of the active cell is used as the destination of the command when run. The default commands are:
What are the types of Software Containers?
In which formats can Threat Emulation forensics reports be viewed in?
Which blades and or features are not supported in R81?
Joey wants to upgrade from R75.40 to R81 version of Security management. He will use Advanced Upgrade with Database Migration method to achieve this.
What is one of the requirements for his success?
What statement best describes the Proxy ARP feature for Manual NAT in R81.20?
Vanessa is a Firewall administrator. She wants to test a backup of her company’s production Firewall cluster Dallas_GW. She has a lab environment that is identical to her production environment. She decided to restore production backup via SmartConsole in lab environment.
Which details she need to fill in System Restore window before she can click OK button and test the backup?
Fill in the blank: Identity Awareness AD-Query is using the Microsoft _______________ API to learn users from AD.
When SecureXL is enabled, all packets should be accelerated, except packets that match the following conditions:
SandBlast agent extends 0 day prevention to what part of the network?
What command would show the API server status?
How many policy layers do Access Control policy support?
Which application should you use to install a contract file?
In what way are SSL VPN and IPSec VPN different?
NO: 219
What cloud-based SandBlast Mobile application is used to register new devices and users?
With SecureXL enabled, accelerated packets will pass through the following:
Which of the following is NOT an option to calculate the traffic direction?
What is the order of NAT priorities?
What is the command to show SecureXL status?
What is not a purpose of the deployment of Check Point API?
What is the benefit of Manual NAT over Automatic NAT?
SmartEvent uses it's event policy to identify events. How can this be customized?
How can you see historical data with cpview?
Which of the following Central Deployment is NOT a limitation in R81.20 SmartConsole?
By default, how often does Threat Emulation update the engine on the Security Gateway?
Which 3 types of tracking are available for Threat Prevention Policy?
To enable Dynamic Dispatch on Security Gateway without the Firewall Priority Queues, run the following command in Expert mode and reboot:
After some changes in the firewall policy you run into some issues. You want to test if the policy from two weeks ago have the same issue. You don't want to lose the changes from the last weeks. What is the best way to do it?
What are the main stages of a policy installation?
What is the purpose of Captive Portal?
True or False: In a Distributed Environment, a Central License can be installed via CLI on a Security Gateway.
What command is used to manually failover a cluster during a zero-downtime upgrade?
The admin lost access to the Gaia Web Management Interface but he was able to connect via ssh. How can you check if the web service is enabled, running and which port is used?
Bob is asked by Alice to disable the SecureXL mechanism temporary tor further diagnostic by their Check Point partner. Which of the following Check Point Command is true:
Which is the command to identify the NIC driver before considering about the employment of the Multi-Queue feature?
Fill in the blank: With the User Directory Software Blade, you can create user definitions on a(n)_____________ Server.
What are the three SecureXL Templates available in R81.20?
Which of the following statements about Site-to-Site VPN Domain-based is NOT true?
An established connection is going to The Application Control Blade Is inspecting the traffic. If SecureXL and CoreXL are both enabled, which path is handling the traffic?
When Configuring Endpoint Compliance Settings for Applications and Gateways within Mobile Access, which of the three approaches will allow you to configure individual policies for each application?
What is the command used to activated Multi-Version Cluster mode?
What Is the difference between Updatable Objects and Dynamic Objects
Fill in the blanks: In the Network policy layer, the default action for the Implied last rule is ____ all traffic. However, in the Application Control policy layer, the default action is ______ all traffic.
Which of the following statements about SecureXL NAT Templates is true?
Alice works for a big security outsourcing provider company and as she receives a lot of change requests per day she wants to use for scripting daily (asks the API services from Check Point fof the Management API. Firstly she needs to be aware if the API services are running for the management. Which of the following Check Point Command is true:
Which two Identity Awareness daemons are used to support identity sharing?
When synchronizing clusters, which of the following statements is FALSE?
How can you switch the active log file?
The Check Point installation history feature in provides the following:
When configuring SmartEvent Initial settings, you must specify a basic topology for SmartEvent to help it calculate traffic direction for events. What is this setting called and what are you defining?
Which of the completed statements is NOT true? The WebUI can be used to manage user accounts and:
After verifying that API Server is not running, how can you start the API Server?
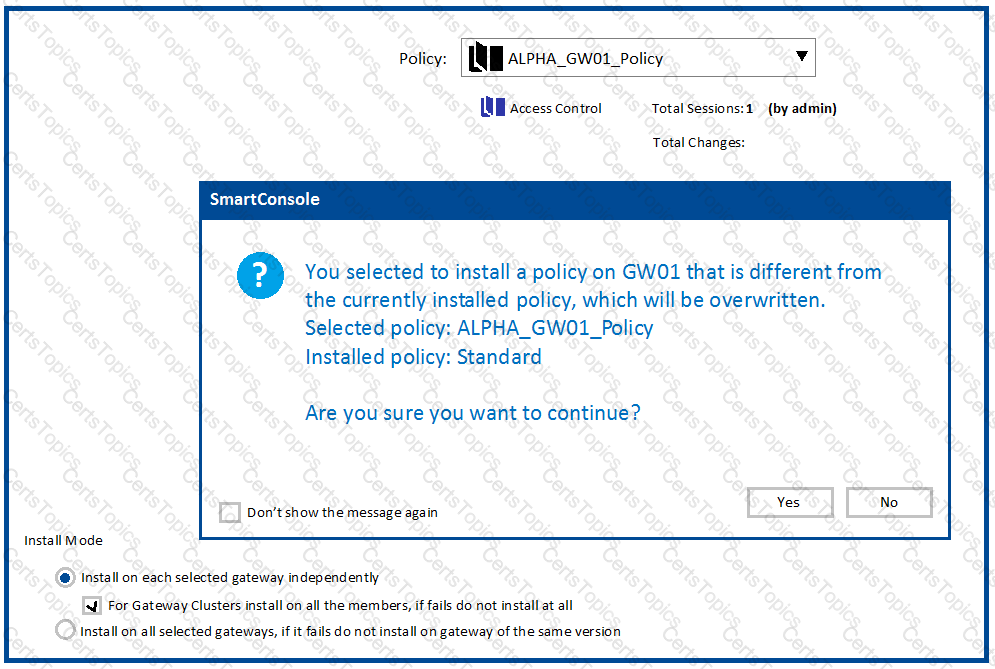
Why would an administrator see the message below?
Access roles allow the firewall administrator to configure network access according to:
By default how often updates are checked when the CPUSE Software Updates Policy is set to Automatic?
Fill in the blank: A ________ VPN deployment is used to provide remote users with secure access to internal corporate resources by authenticating the user through an internet browser.
Name the authentication method that requires token authenticator.
Fill in the blank: Permanent VPN tunnels can be set on all tunnels in the community, on all tunnels for specific gateways, or ______ .
What traffic does the Anti-bot feature block?
Within the Check Point Firewall Kernel resides Chain Modules, which are individually responsible for the
inspection of a specific blade or feature that has been enabled in the configuration of the gateway. For Wire
mode configuration, chain modules marked with _______ will not apply.
What is the correct description for the Dynamic Balancing / Split feature?
Which is the lowest gateway version supported by R81.20 management server?
What a valid SecureXL paths in R81.20?
Fill in the blank: An identity server uses a __________ for user authentication.
In order for changes made to policy to be enforced by a Security Gateway, what action must an administrator perform?
The fwd process on the Security Gateway sends logs to the fwd process on the Management Server, where it is forwarded to___________via____________
Which process handles connection from SmartConsole R81?