Li was asked to create a Splunk configuration to monitor syslog files stored on Linux servers at their organization. This configuration will be pushed out to multiple systems via a Splunk app using the on-prem deployment server.
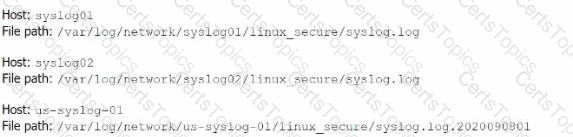
The system administrators have provided Li with a directory listing for the logging locations on three syslog hosts, which are representative of the file structure for all systems collecting this data. An example from each system is shown below:
A)
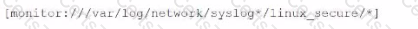
B)
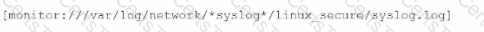
C)
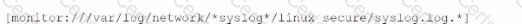
D)
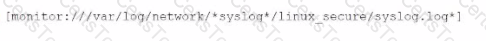
Which of the following is not a path used by Splunk to execute scripts?
Consider the following configurations:
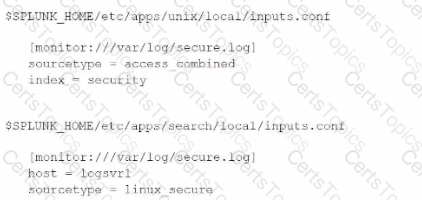
What is the value of the sourcetype property for this stanza based on Splunk's configuration file precedence?
When is data deleted from a Splunk Cloud index?
A monitor has been created in inputs. con: for a directory that contains a mix of file types.
How would a Cloud Admin fine-tune assigned sourcetypes for different files in the directory during the input phase?
In case of a Change Request, which of the following should submit a support case for Splunk Support?
Which of the following is the default bandwidth limit in the Splunk Universal Forwarder credentials package?
Which of the following tasks is not managed by the Splunk Cloud administrator?
What is the correct syntax to monitor /apache/too/logo, /apache/bor/logs, and /apache/bar/l/logo?
A)
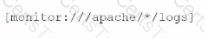
B)

C)
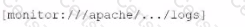
D)
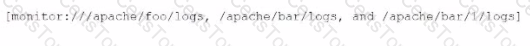
The following sample log event shows evidence of credit card numbers being present in the transactions. loc file.
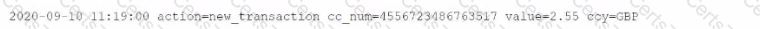
Which of these SEDCM3 settings will mask this and other suspected credit card numbers with an Y character for each character being masked? The indexed event should be formatted as follows:

A)
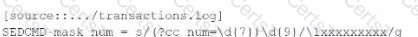
B)
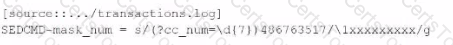
C)
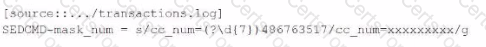
D)
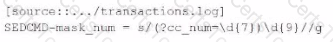
Which of the following statements is true regarding sedcmd?
Configuration folders named default contain configuration files/settings specified in the Splunk product or default settings specified in apps. Which of the following is recommended to override these settings?
Which of the following methods is valid for creating index-time field extractions?
Which of the following statements regarding apps in Splunk Cloud is true?
In Splunk terminology, what is an index?
When monitoring network inputs, there will be times when the forwarder is unable to send data to the indexers. Splunk uses a memory queue and a disk queue. Which setting is used for the disk queue?
What two files are used in the data transformation process?
What can be used in a Splunk Cloud environment to create new sourcetypes?
Which of the following is a valid stanza in props. conf?
What does the followTail attribute do in inputs.conf?
A log file is being ingested into Splunk, and a few events have no date stamp. How would Splunk first try to determine the missing date of the events?
Which file or folder below is not a required part of a deployment app?
How is it possible to test a script from the Splunk perspective before using it within a scripted input?
A customer has worked with their LDAP administrator to configure an LDAP strategy in Splunk. The configuration works, and user Mia can log into Splunk using her LDAP Account. After some time, the Splunk Cloud administrator needs to move Mia from the user role to the power role. How should they accomplish this?