After a networking intern plugged in a switch, a significant number of users in a building lost connectivity. Which of the following is the most likely root cause?
A network administrator is configuring a wireless network with an ESSID. Which of the following is a user benefit of ESSID compared to SSID?
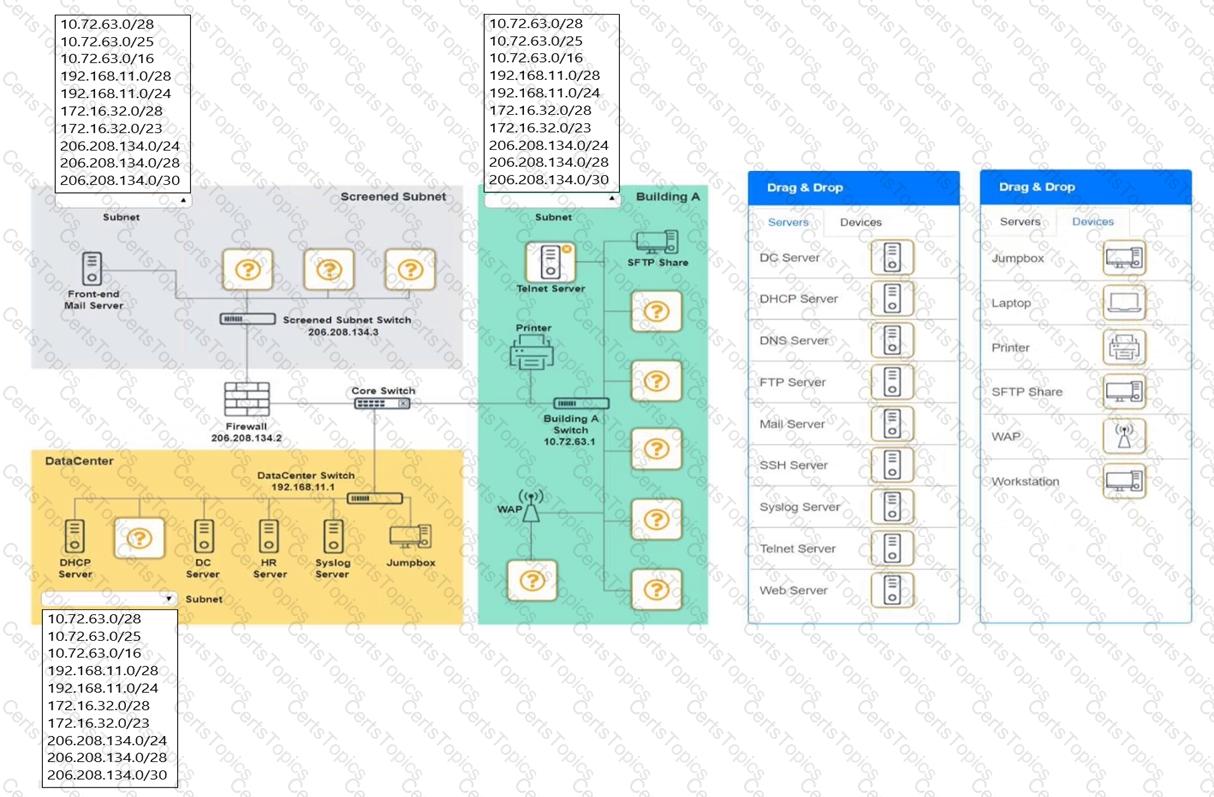
You are tasked with verifying the following requirements are met in order to ensure network security.
Requirements:
Datacenter
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide a dedicated server to resolve IP addresses and hostnames correctly and handle port 53 traffic
Building A
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide devices to support 5 additional different office users
Add an additional mobile user
Replace the Telnet server with a more secure solution
Screened subnet
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide a server to handle external 80/443 traffic
Provide a server to handle port 20/21 traffic
INSTRUCTIONS
Drag and drop objects onto the appropriate locations. Objects can be used multiple times and not all placeholders need to be filled.
Available objects are located in both the Servers and Devices tabs of the Drag & Drop menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A network administrator upgraded the wireless access points and wants to implement a configuration that will give users higher speed and less channel overlap based on device compatibility. Which of the following will accomplish this goal?
A network administrator needs to change where the outside DNS records are hosted. Which of the following records should the administrator change the registrar to accomplish this task?
Which of the following tools uses ICMP to help determine whether a network host is reachable?
A university is implementing a new campus wireless network. A network administrator needs to configure the network to support a large number of devices and high-bandwidth demands from students.
Which of the following wireless technologies should the administrator consider for this scenario?
Which of the following ports is used to transfer data between mail exchange servers?
Which of the following protocol ports should be used to securely transfer a file?
Developers want to create a mobile application that requires a runtime environment, developer tools, and databases. The developers will not be responsible for security patches and updates. Which of the following models meets these requirements?
A network administrator is trying to troubleshoot an issue with a newly installed switch that is not connecting to the network. The administrator logs on to the switch and observes collisions on the interface. Which of the following is most likely the issue?
Which of the following should an installer orient a port-side exhaust to when installing equipment?
Which of the following is an XML-based security concept that works by passing sensitive information about users, such as login information and attributes, to providers?
A network technician needs to configure IP addressing in a Class C network with eight subnets total:
Three subnets for 60 hosts
Three subnets for 15 hosts
Two subnets for seven hosts
Which of the following solutions should the technician use to accomplish this task?
A company is hosting a secure that requires all connections to the server to be encrypted. A junior administrator needs to harded the web server. The following ports on the web server. The following ports on the web server are open:

Which of the following ports should be disabled?
Which of the following standards enables the use of an enterprise authentication for network access control?
Which of the following connectors provides console access to a switch?
Which of the following can support a jumbo frame?
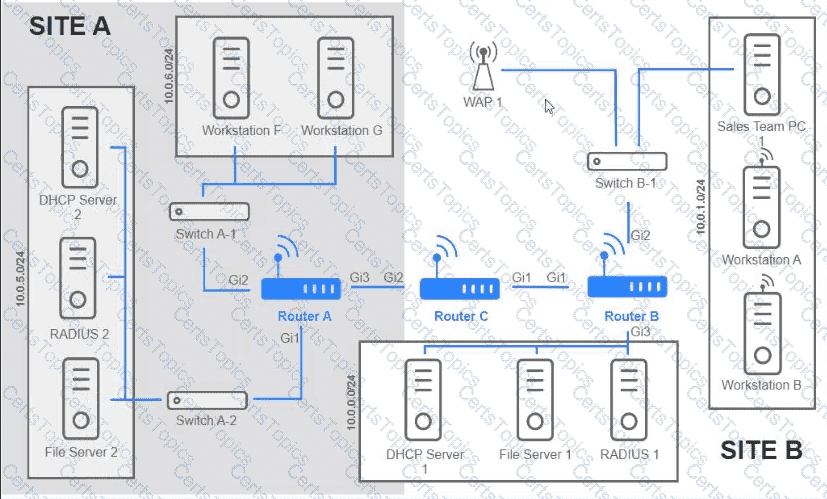
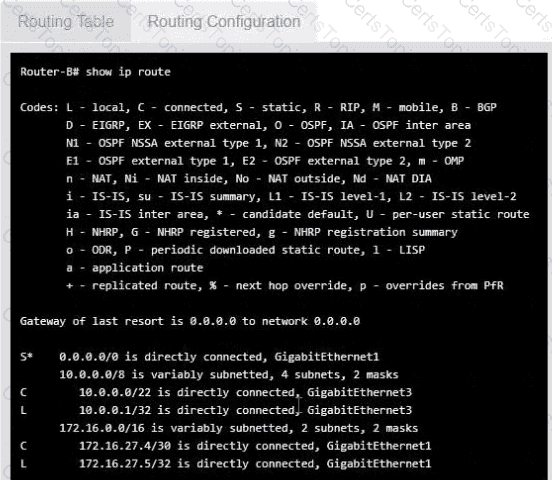
Users are unable to access files on their department share located on flle_server 2. The network administrator has been tasked with validating routing between networks hosting workstation A and file server 2.
INSTRUCTIONS
Click on each router to review output, identity any Issues, and configure the appropriate solution
If at any time you would like to bring back the initial state of trie simulation, please click the reset All button;
A network engineer discovers network traffic that is sending confidential information to an unauthorized and unknown destination. Which of the following best describes the cause of this network traffic?
A network administrator needs to connect two routers in a point-to-point configuration and conserve IP space. Which of the following subnets should the administrator use?
A user tries to visit a website, but instead of the intended site, the page displays vmw.cba.com. Which of the following should be done to reach the correct website?
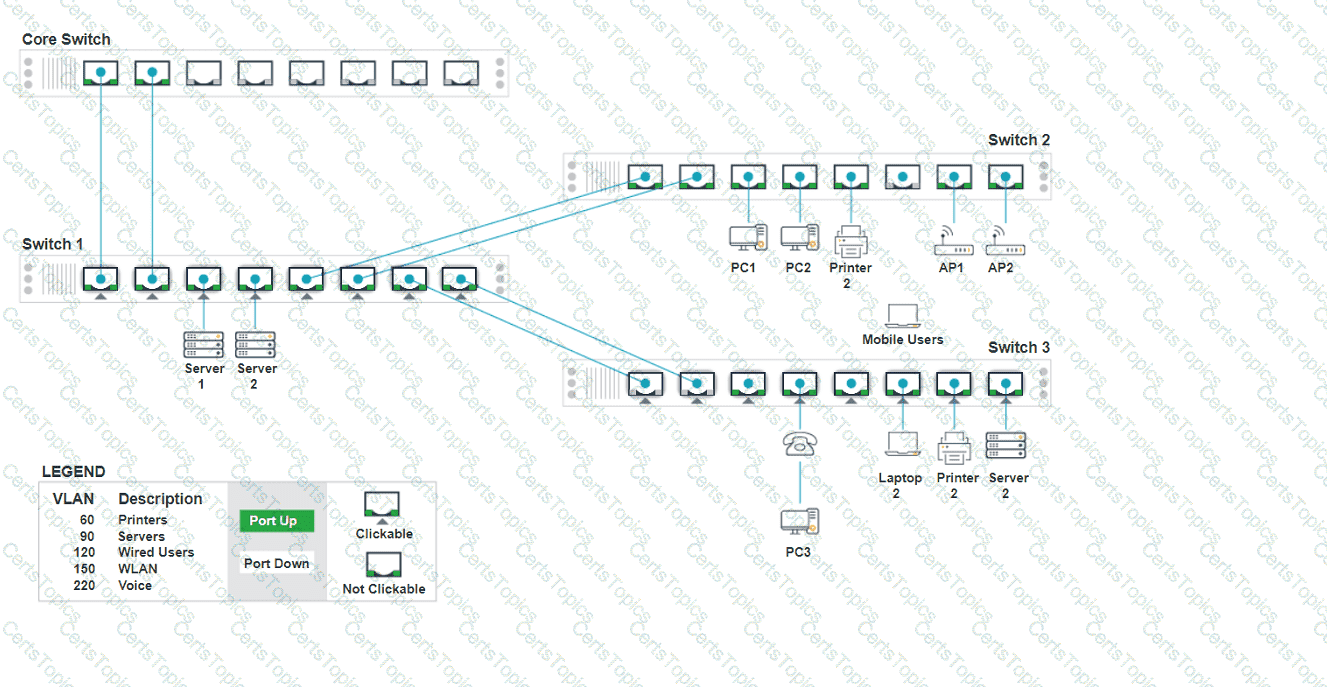
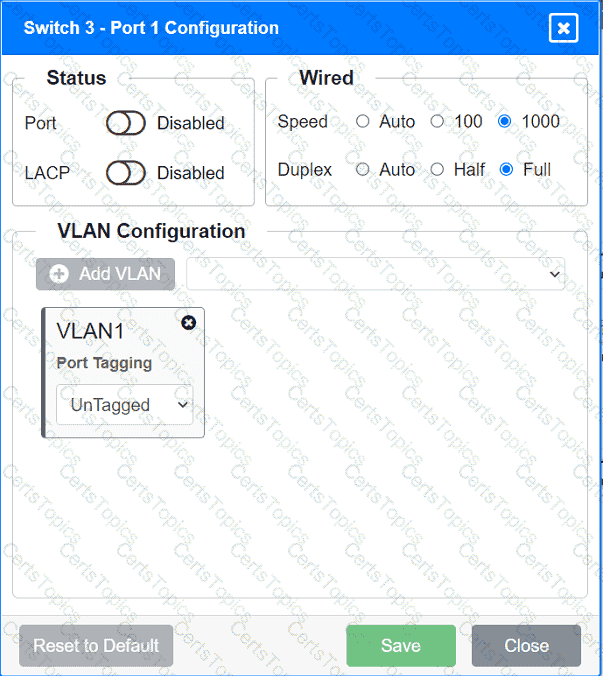
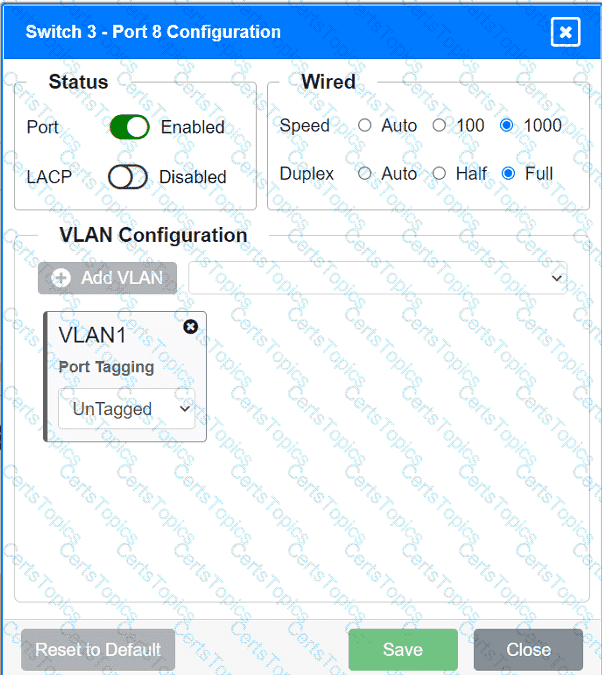
A network technician replaced an access layer switch and needs to reconfigure it to allow the connected devices to connect to the correct networks.
INSTRUCTIONS
Click on the appropriate port(s) on Switch 1 and Switch 3 to verify or reconfigure the
correct settings:
· Ensure each device accesses only its
correctly associated network.
· Disable all unused switchports.
. Require fault-tolerant connections
between the switches.
. Only make necessary changes to
complete the above requirements.
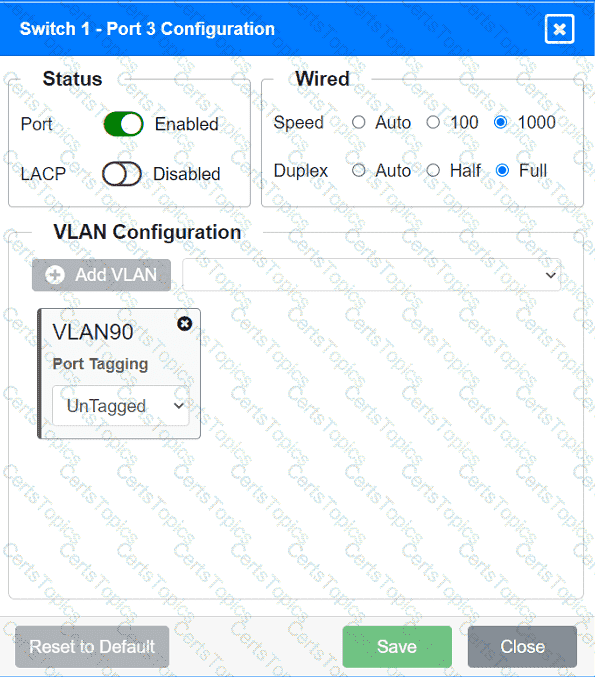
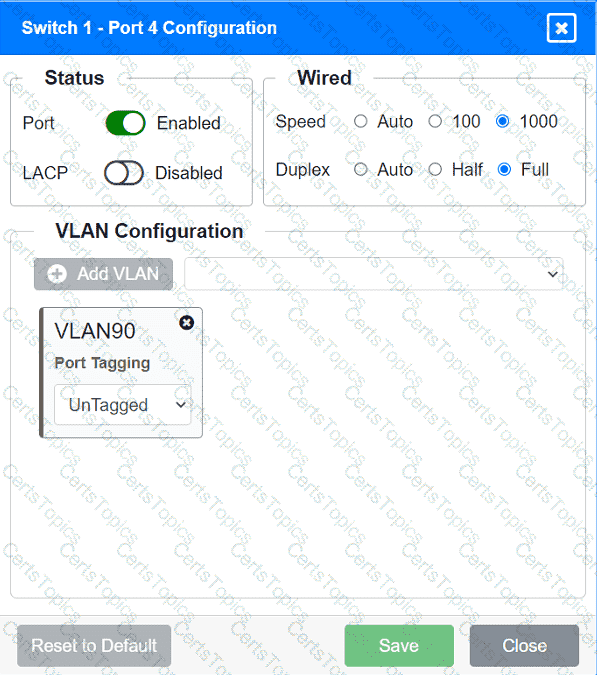
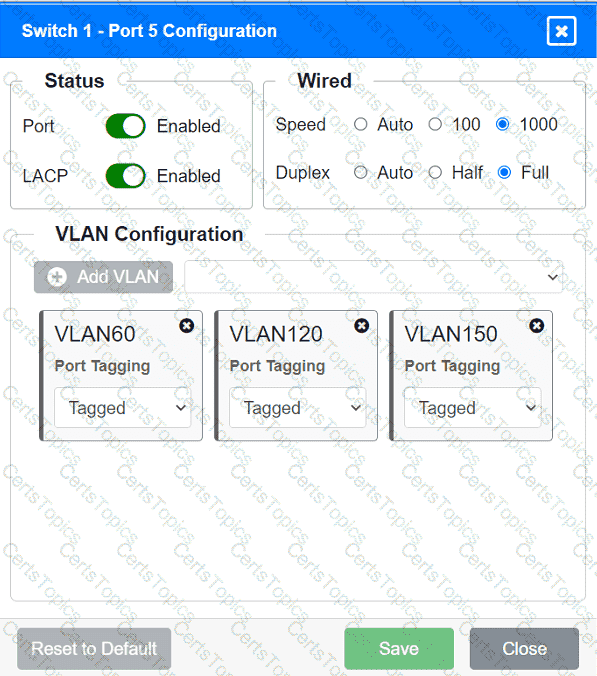
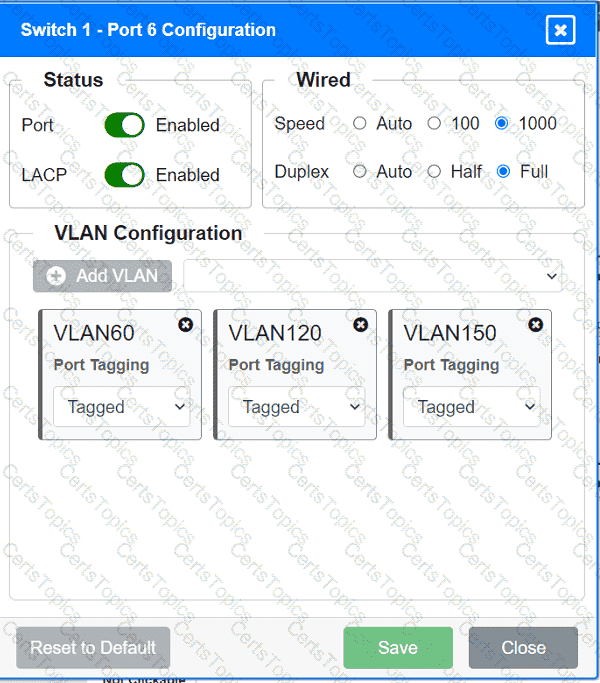
A company is opening a new site that needs to be divided into subnets that accommodate 75 hosts each. Which of the following is the most efficient subnet?
A network administrator wants to update a geofencing policy to limit remote access to the corporate network based on country location. Which of the following would the administrator most likely leverage?
Which of the following requires network devices to be managed using a different set of IP addresses?
Which of the following would be violated if an employee accidentally deleted a customer ' s data?
An attacker gained access to the hosts file on an endpoint and modified it. Now, a user is redirected from the company’s home page to a fraudulent website. Which of the following most likely happened?
A network administrator notices interference with industrial equipment in the 2.4GHz range. Which of the following technologies would most likely mitigate this issue? (Select two).
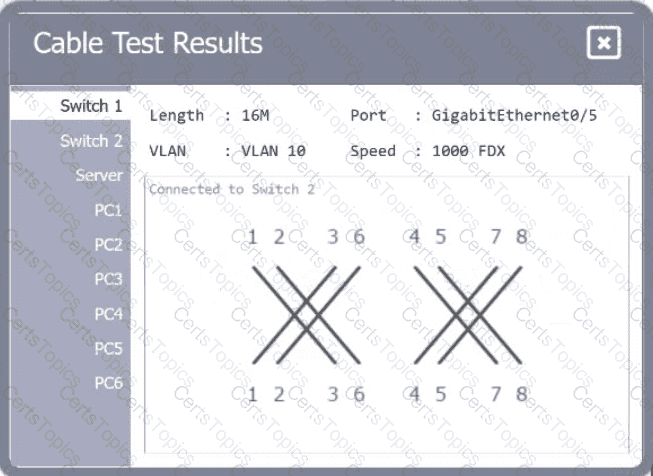
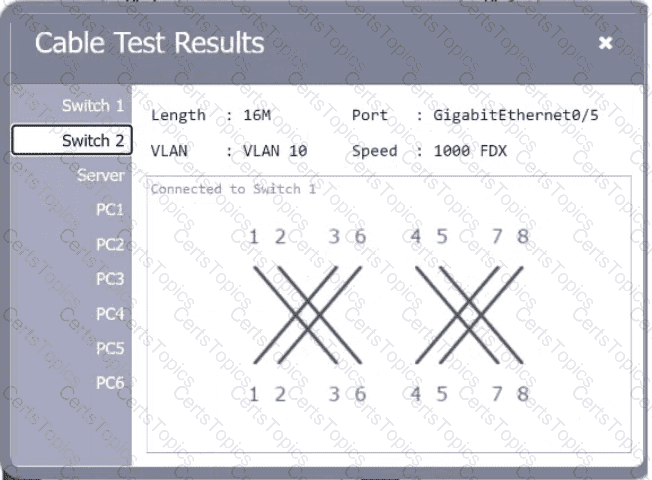
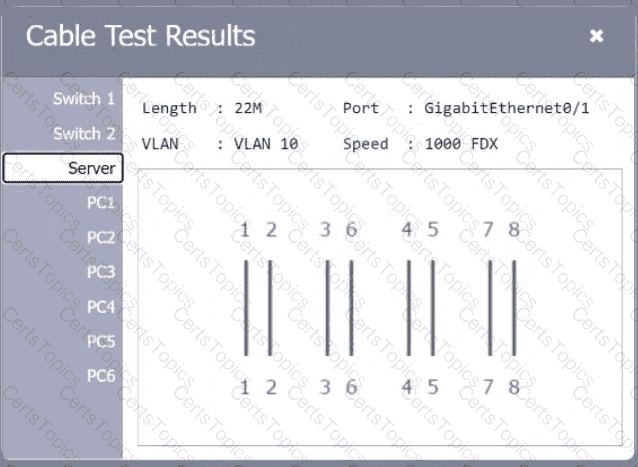
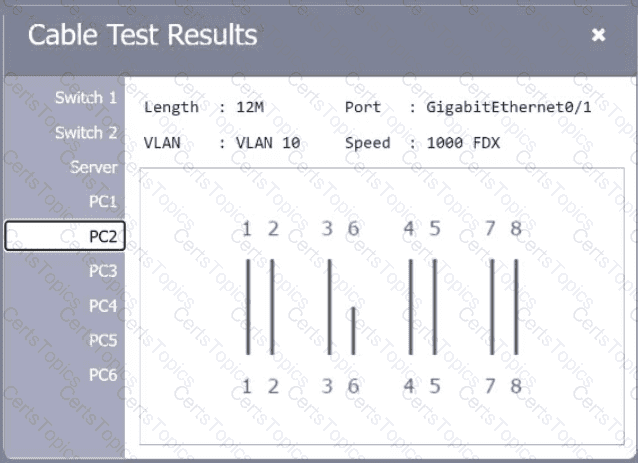
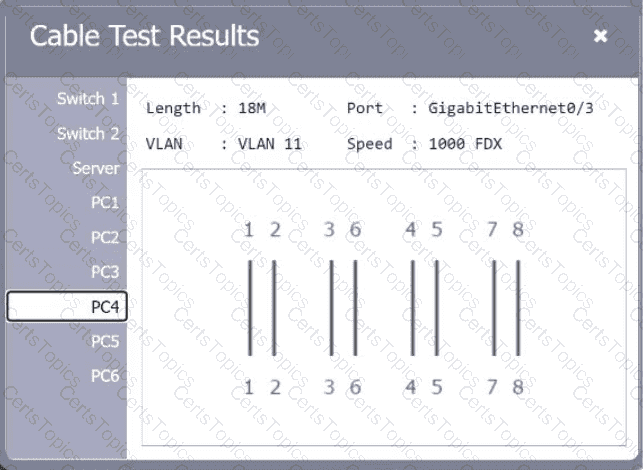
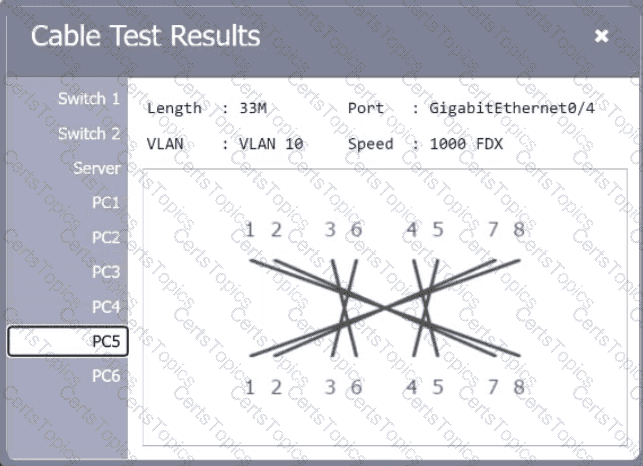
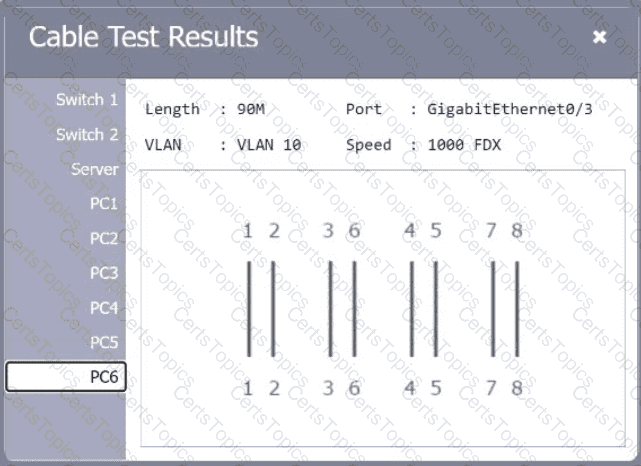
A network technician needs to resolve some issues with a customer ' s SOHO network. The
customer reports that some of the PCs are not connecting to the network, while others
appear to be working as intended.
INSTRUCTIONS
Troubleshoot all the network components.
Review the cable test results first, then diagnose by clicking on the appropriate PC,
server, and Layer 2 switch.
Identify any components with a problem and recommend a solution to correct each
problem.
If at any time you would like to bring back
the initial state of the simulation, please
click the Reset All button.
Which of the following is used most often when implementing a secure VPN?
Users are experiencing significant lag while connecting to a cloud-based application during peak hours. An examination of the network reveals that the bandwidth is being heavily utilized. Further analysis shows that only a few users are using the application at any given time. Which of the following is the most cost-effective solution for this issue?
A technician is planning an equipement installation into a rack in a data center that practices hot aisle/cold aise ventilation. Which of the following directions should the equipement exhaust face when installed in the rack?
Which of the following best describes the transmission format that occurs at the transport layer over connectionless communication?
A company ' s marketing team created a new application and would like to create a DNS record for newapplication.comptia.org that always resolves to the same address as Which of the following records should the administrator use?
Which of the following technologies is the best choice to listen for requests and distribute user traffic across web servers?
A network administrator is troubleshooting a connectivity issue between two devices on two different subnets. The administrator verifies that both devices can successfully ping other devices on the same subnet. Which of the following is the most likely cause of the connectivity issue?
A newtwork administrator needs to create an SVI on a Layer 3-capable device to separate voice and data traffic. Which of the following best explains this use case?
A network administrator needs to ensure that users accept internet usage rules. Which of the following will help the administrator accomplish this task?
A network administrator wants to restrict inbound traffic to allow only HTTPS to the company website, denying all other inbound traffic from the internet. Which of the following would best accomplish this goal?
While troubleshooting connectivity issues, a junior network administrator is given explicit instructions to test the host ' s TCP/IP stack first. Which of the following commands should the network administrator run?
Which of the following best describes a characteristic of a DNS poisoning attack?
A small company has the following IP addressing strategy:
A user is unable to connect to the company fileshare server located at 192.168.10.1. The user’s networking configuration is:
Which of the following will most likely correct the issue?
A user calls the help desk after business hours to complain that files on a device are inaccessible and the wallpaper was changed. The network administrator thinks that this issue is an isolated incident, but the security analyst thinks the issue might be a ransomware attack. Which of the following troubleshooting steps should be taken first?
Which of the following is the best way to securely access a network appliance from an external location?
Which of the following physical installation factors is the most important when a network switch is installed in a sealed enclosure?
Which of the following would most likely be used to implement encryption in transit when using HTTPS?
A customer calls the help desk to report issues connection to the internet. The customer can reach a local database server. A technician goes to the site and examines the configuration:
Which of the following is causing the user ' s issue?
Which of the following steps of the troubleshooting methodology comes after testing the theory to determine cause?
An administrator needs to configure an IoT device with a /21 subnet mask, but the device will only accept dotted decimal notation. Which of the following subnet masks should the administrator use?
An organization wants to ensure that incoming emails were sent from a trusted source. Which of the following DNS records is used to verify the source?
Which of the following provides an opportunity for an on-path attack?
A network administrator needs to fail over services to an off-site environment. This process will take four weeks to become fully operational. Which of the following DR (Disaster Recovery) concepts does this describe?
A network engineer is configuring network ports in a public office. To increase security, the engineer wants the ports to allow network connections only after authentication. Which of the following security features should the engineer use?
A newly opened retail shop uses a combination of new tablets, PCs, printers, and legacy card readers. Which of the following wireless encryption types is the most secure and compatible?
A customer wants to cache commonly used content to reduce the number of full page downloads from the internet. Which of the following should the network administrator recommend?
Which of the following protocols is commonly associated with TCP port 443?
As part of an attack, a threat actor purposefully overflows the content-addressable memory (CAM) table on a switch. Which of the following types of attacks is this scenario an example of?
A customer needs six usable IP addresses. Which of the following best meets this requirement?
A network administrator wants to implement security zones in the corporate network to control access to only individuals inside of the corporation. Which of the following security zones is the best solution?
A new network is being created to support 126 users . Which of the following CIDR ranges provides the most efficient use of space?
A network technician is terminating a cable to a fiber patch panel in the MDF. Which of the following connector types is most likely in use?
Which of the following cloud deployment models is most commonly associated with multitenancy and is generally offered by a service provider?
Which of the following is most closely associated with a dedicated link to a cloud environment and may not include encryption?
An employee has a new laptop and reports slow performance when using the wireless network. Switch firmware was updated the previous night. A network administrator logs in to the switch and sees the following statistics on the switch interface for that employee:
98469 packets input, 1681937 bytes, 0 no buffer
Received 1548 broadcasts (25285 multicasts)
65335 runts, 0 giants, 0 throttles
11546 input errors, 5 CRC, 0 frame, 0 overrun, 0 ignored
0 input packets with dribble condition detected
22781 packets output, 858040 bytes, 0 underruns
0 output errors, 89920 collisions, 0 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier
0 output buffer failures, 0 output buffers swapped out
Which of the following is most likely the cause of the issue?
A company ' s network is experiencing high levels of suspicious network traffic. The security team finds that the traffic is coming from an unknown, foreign IP address. Which of the following is the most cost-efficient way to mitigate this threat?
A network technician is troubleshooting a faulty NIC and tests the theory. Which of the following should the technician do next?
Which of the following troubleshooting steps would provide a change advisory board with the information needed to make a decision?
A network analyst is installing a wireless network in a corporate environment. Employees are required to use their domain identities and credentials to authenticate and connect to the WLAN. Which of the following actions should the analyst perform on the AP to fulfill the requirements?
A network technician is installing a new switch that does not support STP at the access layer of a network. The technician wants a redundant connection to the distribution switch. Which of the following should the technician use?
A network administrator suspects users are being sent to malware sites that are posing as legitimate sites. The network administrator investigates and discovers that user workstations are configured with incorrect DNS IP addresses. Which of the following should the network administrator implement to prevent this from happening again?
During a VoIP call, a user notices inconsistent audio and logs an incident ticket. A network administrator notices inconsistent delays in arrival of the RTP packets. Which of the following troubleshooting tools should the network administrator use to determine the issue?
You have been tasked with implementing an ACL on the router that will:
1. Permit the most commonly used secure remote access technologies from the management network to all other local network segments
2. Ensure the user subnet cannot use the most commonly used remote access technologies in the Linux and Windows Server segments.
3. Prohibit any traffic that has not been specifically allowed.
INSTRUCTIONS
Use the drop-downs to complete the ACL
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A network technician is working on a PC with a faulty NIC. The host is connected to a switch with secured ports. After testing the connection cables and using a known-good NIC, the host is still unable to connect to the network. Which of the following is causing the connection issue?
Which of the following indicates a computer has reached end-of-support?
Which of the following is a company most likely enacting if an accountant for the company can only see the financial department ' s shared folders?
A user connects to a corporate VPN via a web browser and is able to use TLS to access the internal financial system to input a time card. Which of the following best describes how the VPN is being used?
Which of the following is enforced through legislation?
A customer purchases a new UTM device and wants the development team to integrate some of the device’s data-reporting capabilities into the company’s custom internal support software. Which of the following features should the development team use to obtain the device’s data?
A detective is investigating an identity theft case in which the target had an RFID-protected payment card issued and compromised in the same day. The only place the target claims to have used the card was at a local convenience store. The detective notices a video camera at the store is placed in such a way that customers ' credentials can be seen when they pay. Which of the following best explains this social engineering technique?
Which of the following protocols has a default administrative distance value of 90?
Which of the following is a type of NAC that uses a set of policies to allow or deny access to the network based on the user’s identity?
Which of the following is used to stage copies of a website closer to geographically dispersed users?
Which of the following steps in the troubleshooting methodology would be next after putting preventive measures in place?
Which of the following is the best way to reduce the likelihood of electrostatic discharge?
Which of the following allows a user to authenticate to multiple resources without requiring additional passwords?
Which of the following should be used to obtain remote access to a network appliance that has failed to start up properly?
A company ' s Chief Information Security Officer requires that servers and firewalls have accurate time stamps when creating log files so that security analysts can correlate events during incident investigations. Which of the following should be implemented?
Employees report that the network is slow. The network engineer thinks the performance issue is with an upstream router. Which of the following tools should the engineer use to determine the location of the issue?
A network administrator is configuring a network for a new site that will have 150 users. Within the next year, the site is expected to grow by ten users. Each user will have two IP addresses, one for a computer and one for a phone connected to the network. Which of the following classful IPv4 address ranges will be best-suited for the network?
Which of the following Layer 1 devices is responsible for the termination of fiber-optic connections on an SFP-capable switch?
A network administrator is managing network traffic so that classified services and applications are prioritized. Which of the following technologies should the network administrator use?
A data center interconnect using a VXLAN was recently implemented. A network engineer observes slow performance and fragmentation on the interconnect. Which of the following technologies will resolve the issue?
A technician is troubleshooting wireless connectivity near a break room. Whenever a user turns on the microwave, connectivity to the user ' s laptop is lost. Which of the following frequency bands is the laptop most likely using?
A technician is troubleshooting a computer issue for a user who works in a new annex of an office building. The user is reporting slow speeds and intermittent connectivity. The computer is connected via a Cat 6 cable to a distribution switch that is 492ft (150m) away. Which of the following should the technician implement to correct the issue?
A technician needs to quickly set up a network with five wireless devices. Which of the following network types should the technician configure to accomplish this task?
After changes were made to a firewall, users are no longer able to access a web server. A network administrator wants to ensure that ports 80 and 443 on the web server are still accessible from the user IP space. Which of the following commands is best suited to perfom this testing?
After a company installed a new IPS, the network is experiencing speed degradation. A network administrator is troubleshooting the issue and runs a speed test. The results from the different network locations are as follows:
LocationSpeed DownSpeed Up
Wireless laptop4.8 Mbps47.1 Mbps
Wired desktop5.2 Mbps49.3 Mbps
Firewall48.8 Mbps49.5 Mbps
Which of the following is the most likely issue?
A network consultant needs to decide between running an ethernet uplink or using the built-in 5GHz-to-point functionality on a WAP. Which of the following documents provides the best information to assist the consultant with this decision?
Which of the following is a major difference between an IPS and IDS?
A network administrator is troubleshooting issues with a DHCP server at a university. More students have recently arrived on campus, and the users are unable to obtain an IP address. Which of the following should the administrator do to address the issue?
Which of the following is the most cost-effective way for a network administrator to establish a persistent, secure connection between two facilities?
A company wants to implement data loss prevention by restricting user access to social media platforms and personal cloud storage on workstations. Which of the following types of filtering should the company deploy to achieve these goals?
Which of the following would an adversary do while conducting an evil twin attack?
Which of the following appliances provides users with an extended footprint that allows connections from multiple devices within a designated WLAN?
A client wants to increase overall security after a recent breach. Which of the following would be best to implement? (Select two.)
A network engineer needs to deploy an access point at a remote office so that it will not communicate back to the wireless LAN controller. Which of the following deployment methods must the engineer use to accomplish this task?
Which of the following VPN configurations forces a remote user to access internet resources through the corporate network?
An administrator wants to find the top destination for traffic across the infrastructure on a specific day. Which of the following should the administrator use?
Which of the following connectors allows a singular QSFP transceiver to have several physical connections?
A technician is troubleshooting a user ' s laptop that is unable to connect to a corporate server. The technician thinks the issue pertains to routing. Which of the following commands should the technician use to identify the issue?
Which of the following is the best reason to create a golden configuration?
Which of the following is used to redistribute traffic between one source and multiple servers that run the same service?
A network administrator needs to ensure all network ports use a security method that only permits authenticated devices. The solution must meet the following requirements:
• Reduced chance of spoofing
• Centrally managed solution
• Auditable logs
Which of the following technologies provides this functionality?
A network administrator configured a router interface as 10.0.0.95 255.255.255.240. The administrator discovers that the router is not routing packets to a web server with IP 10.0.0.81/28. Which of the following is the best explanation?
A client with a 2.4GHz wireless network has stated that the entire office is experiencing intermittent issues with laptops after the WAP was moved. Which of the following is the most likely reason for these issues?
Which of the following best describes a group of devices that is used to lure unsuspecting attackers and to study the attackers ' activities?
Ten new laptops are added to an existing network, and they can only communicate with one another. An administrator reviews documentation and sees the following:
Subnet: 10.8.100.1/24
Scope: 10.8.100.50 – 10.8.100.150
Reservation: 10.8.100.151 – 10.8.100.175
A technician scans the network and receives the following results:
IP addresses used: 10.8.100.45 – 10.8.100.175
Which of the following should be done to ensure connectivity on all laptops?
Which of the following ports is a secure protocol?
A user ' s VoIP phone and workstation are connected through an inline cable. The user reports that the VoIP phone intermittently reboots, but the workstation is not having any network-related issues Which of the following is the most likely cause?
During a security audit, a consulting firm notices inconsistencies between the documentation and the actual environment. Which of the following can keep a record of who made the changes and what the changes are?
Which of the following is the most closely associated with segmenting compute resources within a single cloud account?
Which of the following does a router prioritize first in the route selection process?
Which of the following technologies are X.509 certificates most commonly associated with?
Which of the following is most commonly associated with many systems sharing one IP address in the public IP-addressing space?
A network administrator deploys several new desk phones and workstation cubicles. Each cubicle has one assigned switchport. The administrator runs the following commands:
nginx
CopyEdit
switchport mode access
switchport voice vlan 69
With which of the following VLANs will the workstation traffic be tagged?
Which of the following should a company implement in order to share a single IP address among all the employees in the office?
A network technician sets up a computer on the accounting department floor for a user from the marketing department. The user reports that they cannot access the marketing department’s shared drives but can access the internet. Which of the following is the most likely cause of this issue?
Which of the following allows an organization to map multiple internal devices to a single external-facing IP address?
Which of the following types of attacks is most likely to occur after an attacker sets up an evil twin?
Which of the following troubleshooting steps provides a change advisory board with the information needed to make a decision?
Which of the following ports creates a secure connection to a directory service?
Which of the following network cables involves bouncing light off of protective cladding?
A user reports having intermittent connectivity issues to the company network. The network configuration for the user reveals the following:
IP address: 192.168.1.10
Subnet mask: 255.255.255.0
Default gateway: 192.168.1.254
The network switch shows the following ARP table:
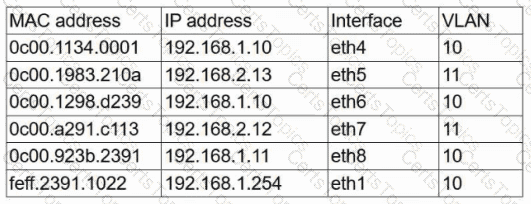
Which of the following is the most likely cause of the user ' s connection issues?
Which of the following connector types is most commonly associated with Wi-Fi antennas?
A network administrator needs to implement a solution to filter access to the internet. Which of the following should the administrator most likely implement?
A network administrator is responding to a request to configure a new IP phone. Which of the following should the network administrator do to allow data and voice traffic to be properly prioritized?
A network administrator receives complaints of intermittent network connectivity issues. The administrator investigates and finds that the network design contains potential loop scenarios. Which of the following should the administrator do?
A network security administrator needs to monitor the contents of data sent between a secure network and the rest of the company. Which of the following monitoring methods will accomplish this task?
A research facility is expecting to see an exponential increase in global network traffic in the near future. The offices are equipped with 2.5Gbps fiber connections from the ISP, but the facility is currently only utilizing 1Gbps connections. Which of the following would need to be configured in order to use the ISP ' s connection speed?