Which of the following types of releases best describes the update made to a code repository production release when it changes from version 1.0 to version 1.1?
A user's assigned cloud credentials are locked, and the user is unable to access the project's application. The cloud administrator reviews the logs and notices several attempts to log in with the user's account were made to a different application after working hours. Which of the following is the best approach for the administrator to troubleshoot this issue?
Which of the following is a field of computer science that enables computers to identify and understand objects and people in images and videos?
Which of the following requirements are core considerations when migrating a small business's on-premises applications to the cloud? (Select two).
A high-usage cloud resource needs to be monitored in real time on specific events to guarantee its availability. Which of the following actions should be used to meet this requirement?
Which of the following is true of SSDs?
During a project kickoff meeting, the project manager wants to set expectations for all of the team members. Which of the following actions should the project manager take to accomplish this goal?
A cloud deployment uses three different VPCs. The subnets on each VPC need to communicate with the others over private channels. Which of the following will achieve this objective?
Which of the following would help a project manager identify that project goals have been reached?
A cloud architect attempts to modify a protected branch but is unable to do so. The architect receives an error indicating the action cannot be completed. Which of the following should the architect try instead''
A company has ten cloud engineers working on different manual cloud deployments. In the past, engineers have had difficulty keeping deployments consistent. Which of the following is the best method to address this issue?
A developer is deploying a new version of a containerized application. The DevOps team wants:
• No disruption
• No performance degradation
* Cost-effective deployment
• Minimal deployment time
Which of the following is the best deployment strategy given the requirements?
A project manager must determine how ideas from the organization and results from the review committee should move through the enterprise for a new project. Which of the following does the project manager need to do?
An administrator used a script that worked in the past to create and tag five virtual machines. All of the virtual machines have been created: however, the administrator sees the following results:
{ tags: [ ] }
Which of the following is the most likely reason for this result?
A company's VMs that are created using the noncritical application tag are automatically shut down at 5:00 p.m. using a cronjob. Which of the following actions would allow a cloud engineer to stop all unresponsive instances with the least effort in case the automation fails?
An organization's security policy states that software applications should not exchange sensitive data in cleartext. The security analyst is concerned about a software application that uses Base64 to encode credit card data. Which of the following would be the best algorithm to replace Base64?
A cloud engineer is concerned about command-and-control (C2) communication out of a cloud network over HTTPS. Which of the following should the cloud engineer implement to most efficiently identify the type of communication?
An organization's web application experiences penodic bursts of traffic when a new video is launched. Users are reporting poor performance in the middle of the month. Which of the following scaling approaches should the organization use to scale based on forecasted traffic?
A company's content management system (CMS) service runs on an laaS cluster on a public cloud. The CMS service is frequently targeted by a malicious threat actor using DDoS.
Which of the following should a cloud engineer monitor to identify attacks?
An engineer wants lo scale several cloud workloads on demand. Which of the following approaches is the most suitable?
An IT manager is migrating the production environment to the cloud but needs to keep control of the operating systems, patches, and settings of all resources. Which of the following deployment models will best meet the requirements?
A retail store is rolling out a new point-of-sale solution to several locations where the staff members normally use cash registers. Which of the following activities will best assist staff members with integrating this new solution? (Select two).
A security analyst confirms a zero-day vulnerability was exploited by hackers who gained access to confidential customer data and installed ransomware on the server Which of the following steps should the security analyst take? (Select two).
Which of the following is the focus of DevSecOps?
A cloud administrator recently created three servers in the cloud. The goal was to create ACLs so the servers could not communicate with each other. The servers were configured
with the following IP addresses:

After implementing the ACLs, the administrator confirmed that some servers are still able to reach the other servers. Which of the following should the administrator change to
prevent the servers from being on the same network?
A company has ten cloud engineers working on different manual following is the best method to address this issue?
A customer is migrating applications to the cloud and wants to grant authorization based on the classification levels of each system. Which of the following should the customer implement to ensure authorisation to systems is granted when the user and system classification properties match? (Select two).
An organization needs to retain its data for compliance reasons but only when required. Which of the following would be the most cost-effective type of tiered storage?
A company serves customers globally from its website hosted in North America. A cloud engineer recently deployed new instances of the website in the Europe region. Which of the
following is the most likely reason?
An on-premises data center is located in an earthquake-prone location. The workload consists of real-time, online transaction processing. Which ot the following data protection strategies should be used to back up on-premises data to the cloud while also being cost effective?
A company recently migrated to a public cloud provider. The company's computer incident response team needs to configure native cloud services tor detailed logging. Which of the following should the team implement on each cloud service to support root cause analysis of past events? {Select two).
Given the following command:
Sdocker pull images.comptia.org/user1/myimage:latest
Which of the following correctly identifies images.comptia.org?
Which of the transfer when comparing a multiregional to a single-region cloud platform design?
A project sponsor has asked for a log listing all the bugs identified within a specific project. Which of the following tools should the project manager provide to the sponsor?
An e-commerce company is migrating from an on-premises private cloud environment to
a public cloud IaaS environment. You are tasked with right-sizing the environment to
save costs after the migration. The company's requirements are to provide a 20% overhead above the average resource consumption, rounded up.
INSTRUCTIONS
Review the specifications and graphs showing resource usage for the web and database servers. Determine the average resource usage and select the correct specifications from the available drop-down options.


Which of the following service options would provide the best availability for critical applications in the event of a disaster?
A cloud administrator needs to collect process-level, memory-usage tracking for the virtual machines that are part of an autoscaling group. Which of the following is the best way to
accomplish the goal by using cloud-native monitoring services?
The performance of an e-commerce website decreases dramatically during random periods. The IT team is evaluating available resources to mitigate the situation. Which of the following is the best approach to effectively manage this scenario'?
Servers in the hot site are clustered with the main site.
A cloud engineer is reviewing the following Dockerfile to deploy a Python web application:

Which of the following changes should the engineer make lo the file to improve container security?
Users have been reporting that a remotely hosted application is not accessible following a recent migration. However, the cloud administrator is able to access the application from
the same site as the users. Which of the following should the administrator update?
Which of the following cloud-native architecture designs is the most easily maintained, decentralized, and decoupled?
A company that has several branches worldwide needs to facilitate full access to a specific cloud resource to a branch in Spain. Other branches will have only read access. Which of
the following is the best way to grant access to the branch in Spain?
A cloud security analyst is concerned about security vulnerabilities in publicly available container images. Which of the following is the most appropriate action for the analyst to
recommend?
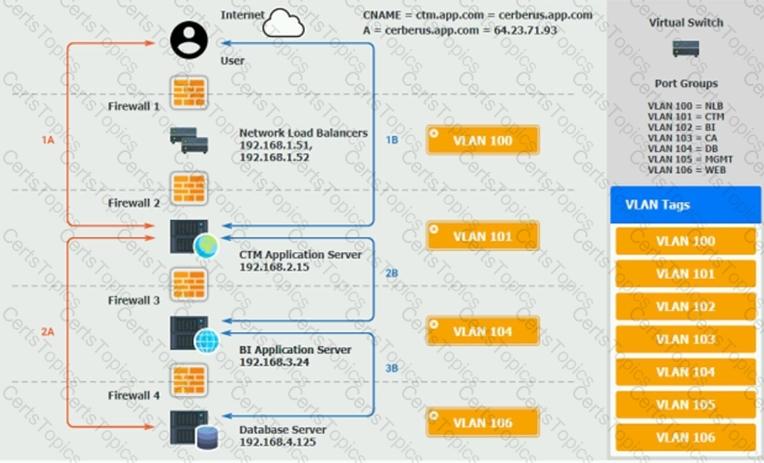
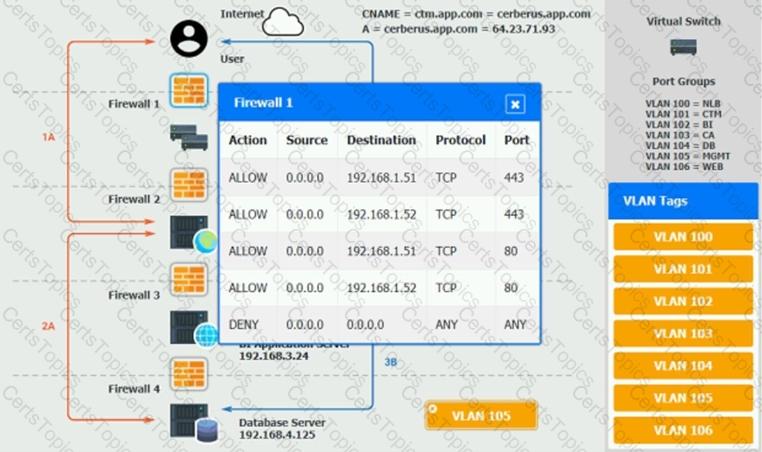
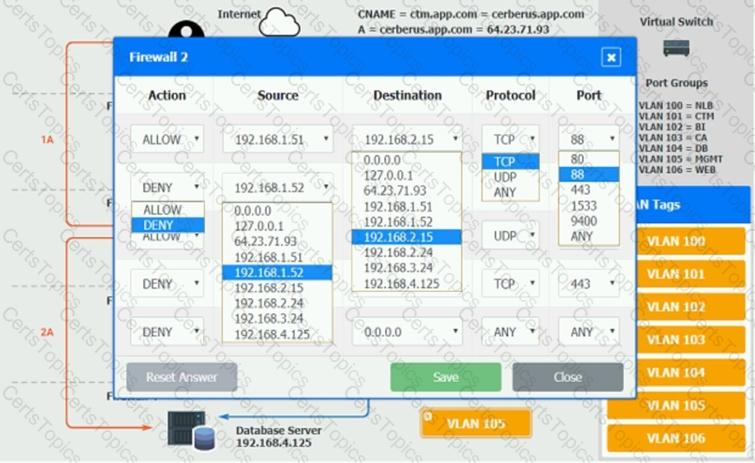
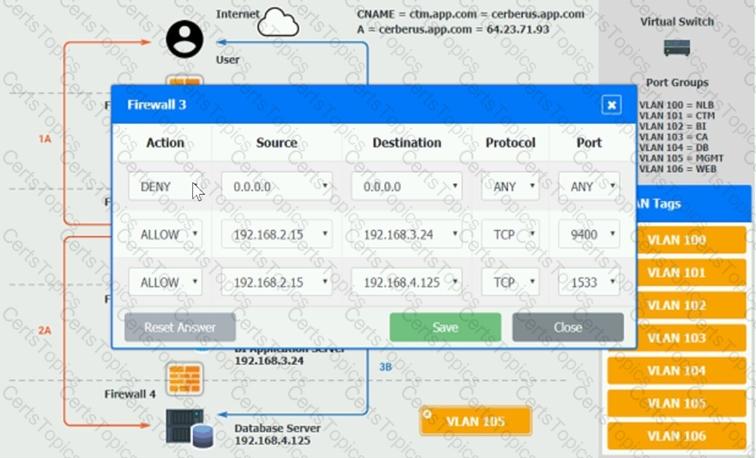
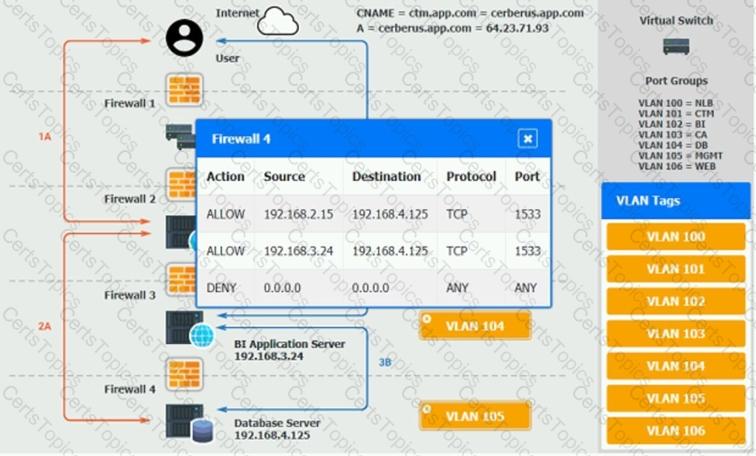
The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS.
Refer to the application dataflow:
1A – The end user accesses the application through a web browser to enter and view clinical data.
2A – The CTM application server reads/writes data to/from the database server.
1B – The end user accesses the application through a web browser to run reports on clinical data.
2B – The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
3B – The BI application server gets the data from the database server and presents it to the CTM application server.
When UAT users try to access the application using or they get a message stating: “Browser cannot display the webpage.” The QA team has raised a ticket to troubleshoot the issue.
INSTRUCTIONS
You are a cloud engineer who is tasked with reviewing the firewall rules as well as virtual network settings.
You should ensure the firewall rules are allowing only the traffic based on the dataflow.
You have already verified the external DNS resolution and NAT are working.
Verify and appropriately configure the VLAN assignments and ACLs. Drag and drop the appropriate VLANs to each tier from the VLAN Tags table. Click on each Firewall to change ACLs as needed.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A list of CVEs was identified on a web server. The systems administrator decides to close the ports and disable weak TLS ciphers. Which of the following describes this vulnerability management stage?
A cloud engineer wants to run a script that increases the volume storage size if it is below 100GB. Which of the following should the engineer run?

Which of the following communication methods between on-premises and cloud environments would ensure minimal-to-low latency and overhead?
A security engineer recently discovered a vulnerability in the operating system of the company VMs. The operations team reviews the issue and decides all VMs need to be updated
from version 3.4.0 to 3.4.1. Which of the following best describes the type of update that will be applied?
An organization's internal security team mandated that public cloud resources must be accessible only by a corporate VPN and not by direct public internet access. Which of the
following would achieve this objective?
A cloud administrator deploys new VMs in a cluster and discovers they are getting IP addresses in the range of 169.254.0.0/16. Which of the following is the most likely cause?
Which of the following is used to deliver code quickly and efficiently across the development, test, and production environments?
Which of the following models will best reduce the cost of running short-term, non-critical workloads?
A manager wants information about which users signed in to a certain VM during the past month. Which of the following can the cloud administrator use to obtain this information?
A technician receives an email from a vendor who is requesting payment of an invoice for human resources services. The email contains a request for bank account numbers. Which of the following types of attacks does this behavior most likely indicate?
A cloud developer is creating a static website that customers will be accessing globally. Which of the following services will help reduce latency?
A cloud developer needs to update a REST API endpoint to resolve a defect. When too many users attempt to call the API simultaneously, the following message is displayed:
Error: Request Timeout - Please Try Again Later
Which of the following concepts should the developer consider to resolve this error?
A company migrated its CRM system to a SaaS solution. The security team is updating the RAG matrix for the newly migrated CRM. Given the following table:

Which of the following responsibility assignments best aligns with the shared responsibility model for the new CRM?
A customer's facility is located in an area where natural disasters happen frequently. The customer requires the following:
• Data resiliency due to exposure to frequent natural disasters
• Data localization because of privacy regulations in the country
• High availability
Which of the following cloud resources should be provisioned to meet these requirements?
A cloud engineer is running a latency-sensitive workload that must be resilient and highly available across multiple regions. Which of the following concepts best addresses these
requirements?
Once a change has been made to templates, which of the following commands should a cloud architect use next to deploy an laaS platform?
A systems administrator is configuring backups on a VM and needs the process to run as quickly as possible, reducing the bandwidth on the network during all times from Monday through Saturday. In the event of data corruption, the management team expects the mean time to recovery to be as low as possible. Which of the following backup methods can the administrator use to accomplish these goals?
A developer is testing code that will be used to deploy a web farm in a public cloud. The main code block is a function to create a load balancer and a loop to create 1.000 web servers, as shown below:

The developer runs the code against the company's cloud account and observes that the load balancer is successfully created, but only 100 web servers have been created. Which of the following should the developer do to fix this issue?
Which of the following can reduce the risk of CI/CD pipelines leaking secrets?
A cloud administrator shortens the amount of time a backup runs. An executive in the company requires a guarantee that the backups can be restored with no data loss. Which of th€ following backup features should the administrator lest for?
Which of the following do developers use to keep track of changes made during software development projects?
A cloud infrastructure administrator updated the IP tables to block incoming connections and outgoing responses to 104.225.110.203. Which of the following vulnerability management steps is this an example of?
A government agency in the public sector is considering a migration from on premises to the cloud. Which of the following are the most important considerations for this cloud migration? (Select two).
Which of the following best explains the concept of migrating from on premises to the cloud?
A company is developing a new web application that requires a relational database management system with minimal operational overhead. Which of the following should the company choose?
A company receives files daily from a bank. The company requires that the files must be copied from the cloud storage resource to another cloud storage resource for further
processing. Which of the following methods requires the least amount of effort to achieve the task?
A cloud engineer hardened the WAF for a company that operates exclusively in North America. The engineer did not make changes to any ports, and all protected applications have
continued to function as expected. Which of the following configuration changes did the engineer most likely apply?
A company needs to deploy its own code directly in the cloud without provisioning additional infrastructure. Which of the following is the best cloud service model for the company to use?
A network administrator is budding a site-to-site VPN tunnel from the company's headquarters office 10 the company's public cloud development network. The network administrator confirms the following:
The VPN tunnel is established on the headquarter office firewall.
While inside the office, developers report that they cannot connect to the development network resources.
While outside the office on a client VPN, developers report that they can connect to the development network resources.
The office and the client VPN have different IP subnet ranges.
The firewall flow logs show VPN traffic is reaching the development network from the office.
Which of the following is the next step the next network administrator should take to troubleshoot the VPN tunnel?
A cloud engineer wants to implement a monitoring solution to detect cryptojacking and other cryptomining malware on cloud instances. Which of the following metrics would most likely be used to identify the activity?
A security engineer Identifies a vulnerability m a containerized application. The vulnerability can be exploited by a privileged process to read tie content of the host's memory. The security engineer reviews the following Dockerfile to determine a solution to mitigate similar exploits:

Which of the following is the best solution to prevent similar exploits by privileged processes?